Funeral: Silent security analysis using traffic
I think network traffic analysis in pentest scenarios is vastly underrated. In this article, I will demonstrate a technique to silently analyze the security of network equipment based on traffic analysis alone.

I think network traffic analysis in pentest scenarios is vastly underrated. In this article, I will demonstrate a technique to silently analyze the security of network equipment based on traffic analysis alone.
Caster - Funeral
Genre: Offensive
Label: exploit.org
Release Date: 1 June 2024
Performed by: Caster
Written by: Magama Bazarov
Cover Man: Magama Bazarov (Sony ILCE-7M3, f/2.8, 1/100 sec)
Intro
This article will be useful for pentesters and network defense professionals alike.
The entire research is based on traffic analysis only, without creating any noise in the air. The traffic can potentially reveal sensitive information about the network infrastructure, such as the use of dynamic routing protocols, gateway redundancy. This article presents not only traffic analysis, but also talks about impact from attacks and mitigation techniques.
This article will discuss:
- 802.1X Detection, MACSec Detection
- Host Discovery with passive ARP
- Discovery Protocols
- VLAN Security Issues
- STP Security Issues
- Dynamic Routing
- First Hop Redundancy
- Name Resolution Protocol Attacks
- IPv6 Takeover with DHCPv6
The skeleton of this article is built on my tool Above, which is a traffic sniffer for finding network security issues. It is included in Kali Linux and anyone can install it.
caster@kali:~$ sudo apt update
caster@kali:~$ sudo apt install aboveDisclaimer
This article is of an introductory nature and is intended solely for information security specialists conducting testing within the framework of concluded contracts. The author and editorial staff of exploit.org are not liable for any damage caused by the use of the information presented. The distribution of malware, disruption of systems and confidentiality of correspondence is a violation of the law and may result in criminal liability.
802.1X
802.1X is an authentication standard to protect a network from unauthorized connections already at the link layer. It is a serious problem for pentesters because 802.1X must be bypassed to gain access to the LAN. Yes, 802.1X allows you to stop unauthorized access to the LAN, but 802.1X is also vulnerable to attacks.
A popular attack is the bridge-based attack. In this attack, the attacker effectively turns his machine into a transparent bridge, gaining access to the infrastructure without disrupting the legitimate host. However, this attack only works against 802.1X-2004, this attack will not work against 802.1X-2010, you will have to use more specific attack methods like using a custom solenoid device, EAP-MD5, Rogue Gateway.
Versions Checkup
However, it is fair to say that in my experience I have seen 802.1X-2004 most often. Implementing 802.1X-2010 is actually a complicated and expensive process. And with 802.1X AE, you need to have an agent on each device. EAPOL frame analysis will allow you to recognize the 802.1X version:
if packet[EAPOL].version == 3:
print ("[*] 802.1X Version: 2010")
elif packet[EAPOL].version == 2:
print ("[*] 802.1X Version: 2004")
elif packet[EAPOL].version == 1:
print ("[*] 802.1X Version: 2001")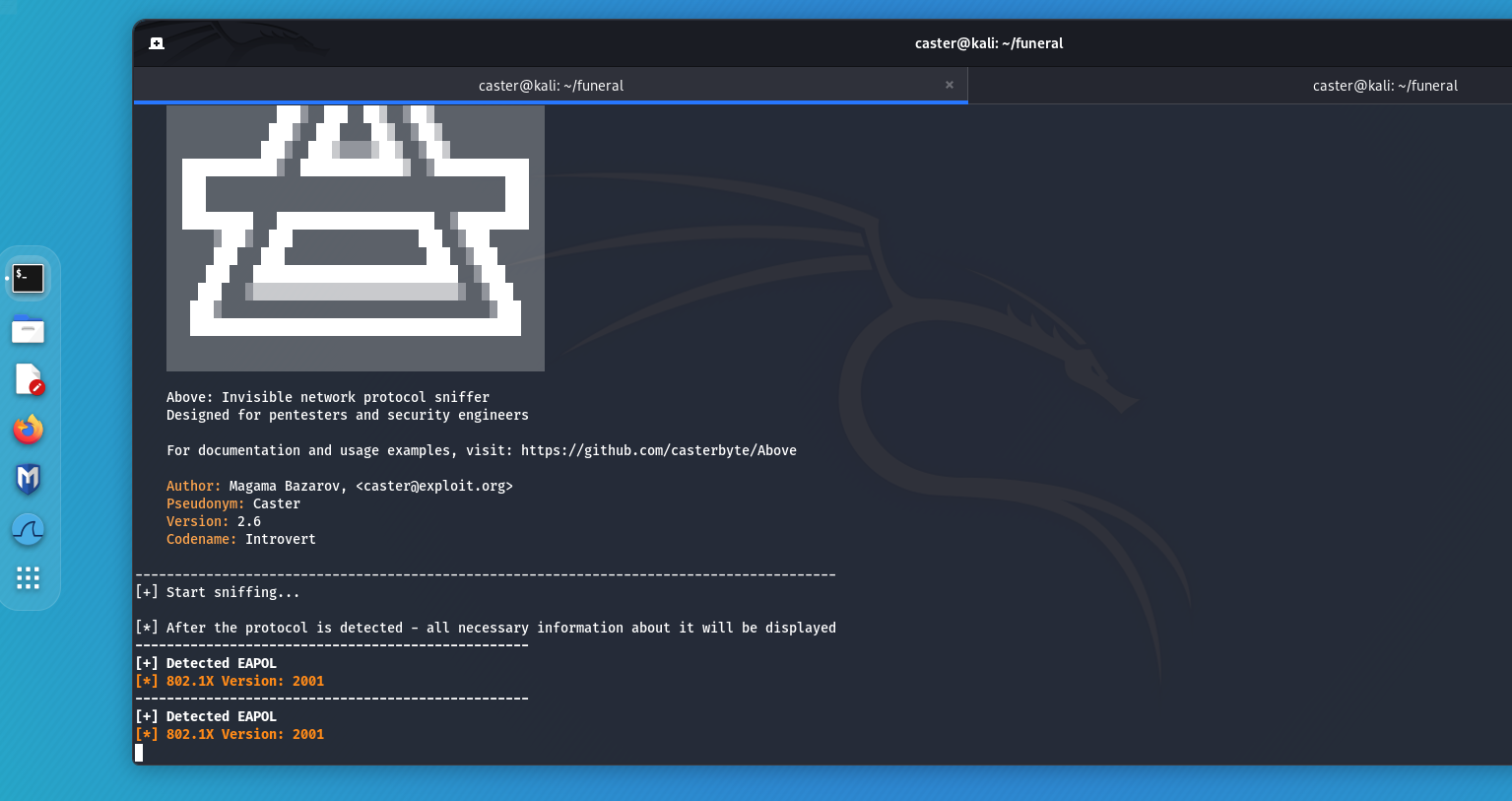
MACSec
MACSec is a technology that encrypts network traffic at the link layer. If an attacker attempts to intercept a frame protected with MACSec, he will be notified because the frame will be recognized as encrypted. But don't be forgotten. Despite the presence of MACSec, an attack on 802.1X is possible due to the potential use of EAP-MD5.
caster@kali:~$ sudo above --interface eth0 --timer 100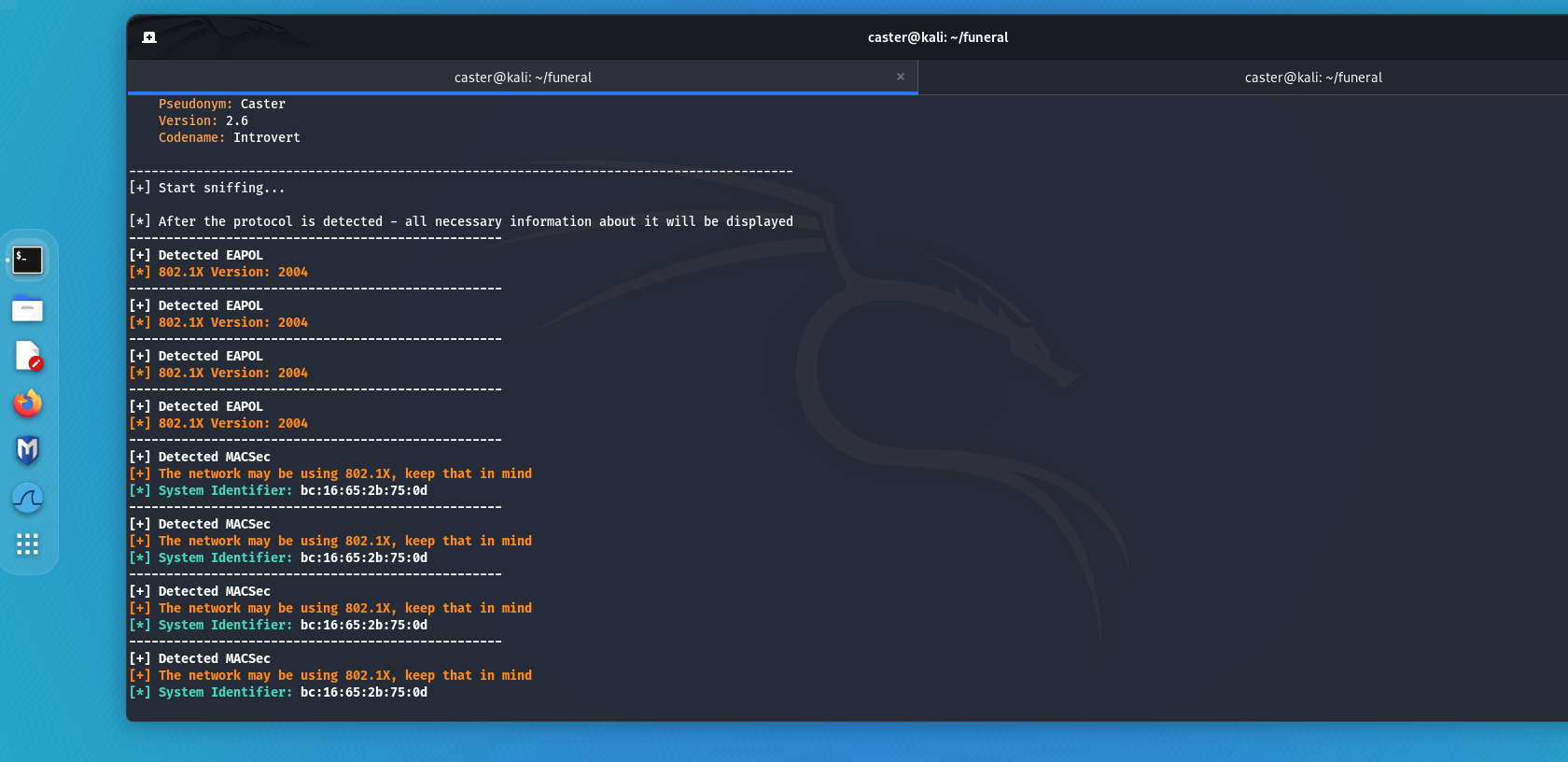
Mitigations
- Profiling
- MACSec + EAP-TLS (with server certificate verification)
Passive ARP
Reconnaissance is one of the important first steps of an infrastructure attacker. ARP scanning is widely known among pentesters because it allows you to quickly find out information about existing hosts. However, this scan generates a lot of noise in the air, and there is a risk of alarming the Storm-Control system, the traffic generated by ARP scanning can potentially exceed the threshold configured by the network administrator. Pentest will no longer be a secret because the Storm-Control alarm will cause network administrators to realize that something is going on with the network.
Passive ARP is a variant of finding hosts on a segment without making any noise on the air. This is accomplished by analyzing ARP frames and exfiltrating IP addresses from the ARP frames. Thus, without scanning anything, the attacker already knows which host is on the same segment as him.
caster@kali:~$ sudo above --interface eth0 --passive-arp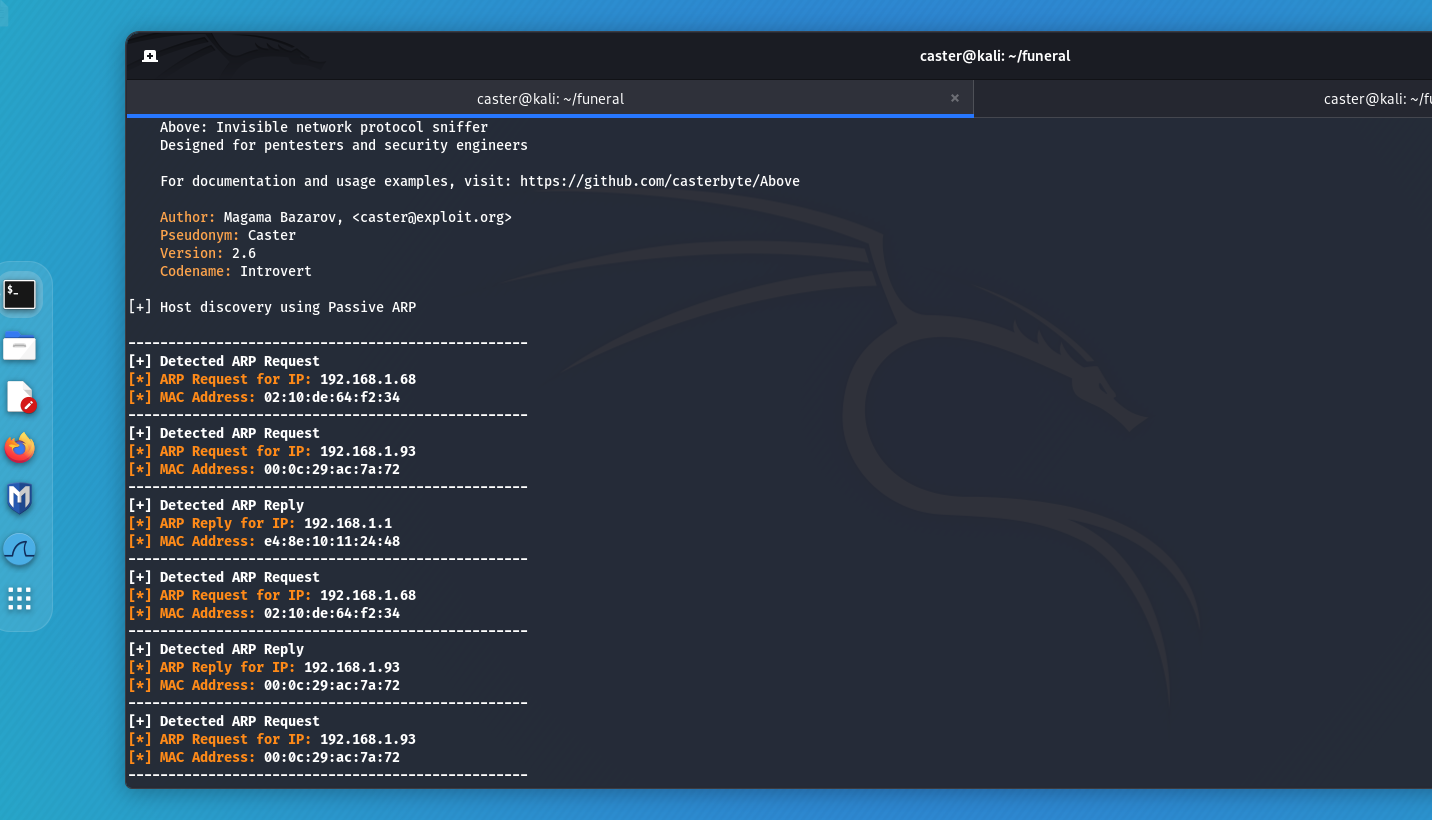
Discovery Protocols
Discovery protocols are designed to automatically exchange service information between network devices. They greatly simplify troubleshooting for network administrators. However, it is often the case that these protocols are enabled by default on all device interfaces. This creates a vulnerability because an attacker can gain access to sensitive information about the network infrastructure by connecting to a switch port and capturing packets from these protocols. Such information may include device model, operating system version, interface ID, and other data. The most common Discovery protocols include:
- CDP (Cisco Discovery Protocol): A protocol developed by Cisco, widely used in Cisco networks to exchange information between devices;
- LLDP (Link Layer Discovery Protocol): A standard protocol developed by IEEE, supported by various network equipment manufacturers;
- MNDP (MikroTik Neighbor Discovery Protocol): A protocol used by MikroTik devices to exchange information about neighboring devices.
caster@kali:~$ sudo above --interface eth0 --timer 100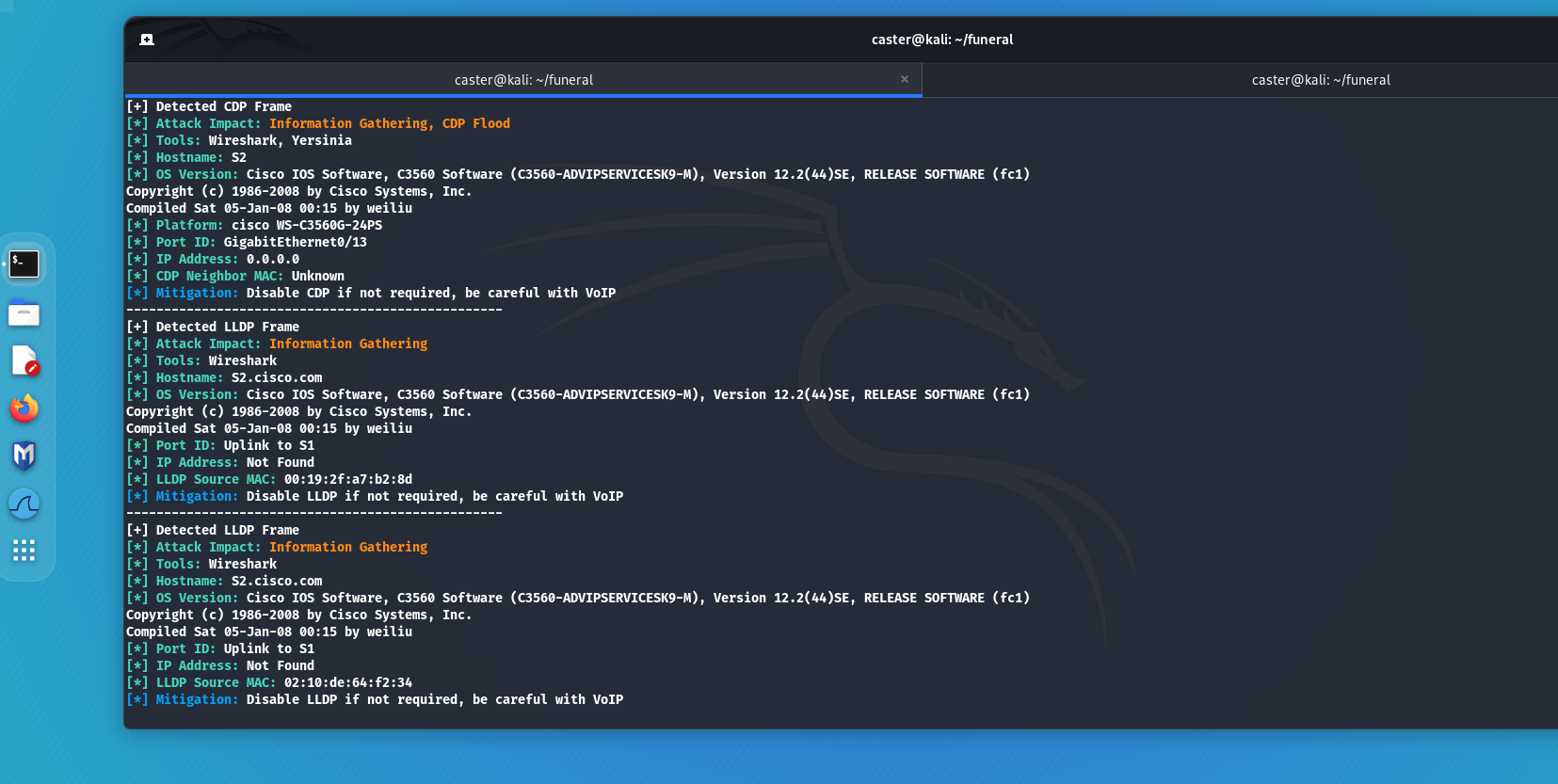
Mitigations
The solution to the security problem of Discovery protocols is quite simple: disable them where they are not needed. Leave these protocols running only on interfaces that connect network devices to each other (e.g. switch to switch, router to router, switch to router). However, you must be careful about the user ports to which VoIP telephony may be connected. Some VoIP systems use Discovery protocols for their operation. Disabling Discovery protocols on VoIP ports can cause telephony failures, so such actions require special care and testing beforehand.
VLAN
VLAN (Virtual Local Area Network) is a technology for dividing a physical network into logical segments. It is designed to reduce the load on the switch's computing resources. Each logical VLAN segment will be a separate broadcast domain. Where as in the default configuration, all switch ports are on VLAN 1 and there will be a single broadcast domain for all devices. This can have a negative impact on switch performance. Partitioning the network into VLANs not only allows for better utilization of switch resources, but also gives the network security if you need to separate a business-critical segment from the rest. And there are more specific versions of VLANs like Private VLAN, when inside the VLAN a host or a group of hosts is separated from the rest, but this is used in very specific cases, when you need to isolate a vulnerable host, SCADA devices, etc., but it is used in very specific cases.
DTP
DTP (Dynamic Trunking Protocol) is a protocol developed by Cisco engineers, which allows to implement an automatic trunking system, when switches themselves decide which port will be trunked and which will not. In my opinion, the use of DTP indicates poor network design, the network becomes less predictable. The network administrator should decide which port should be trunked and which should be in access mode.
caster@kali:~$ sudo above --interface eth0 --timer 100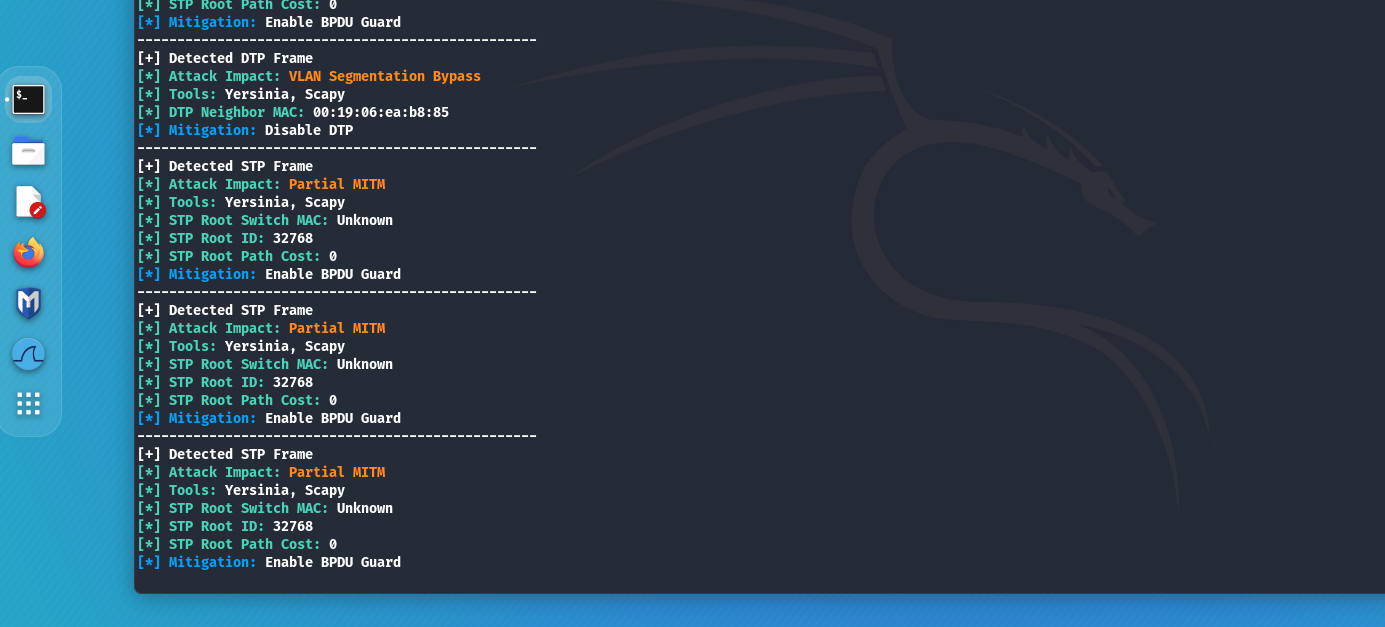
To encounter DTP during penetration testing is a rare case, usually it happens on switch ports forgotten by the administrator who forgot to turn them off or put them in switchport nonegotiate mode. The main problem is that all Cisco switch ports are in VLAN 1 by default and are in Dynamic Auto mode. Dynamic Auto is the mode of a port in a DTP context that will wait for a trunk initiation from a neighboring port. If a DTP Desirable frame (a frame that triggers the port to switch to trunk) arrives on that port, the port will become trunked. If an attacker sends a DTP Desirable frame to a port in Dynamic Auto mode, the port becomes trunked, which means it can hop to all VLAN segments within that switch, a.k.a. VLAN Hopping.
VLAN ID Tags (802.1Q)
An attacker can accidentally bump into a trunk port. Either it happened by accident, or it was due to misconfiguration of the switch port that the IP phone and computer were connected to, or the attacker hacked into the hypervisor, which in production is often on the trunk port.
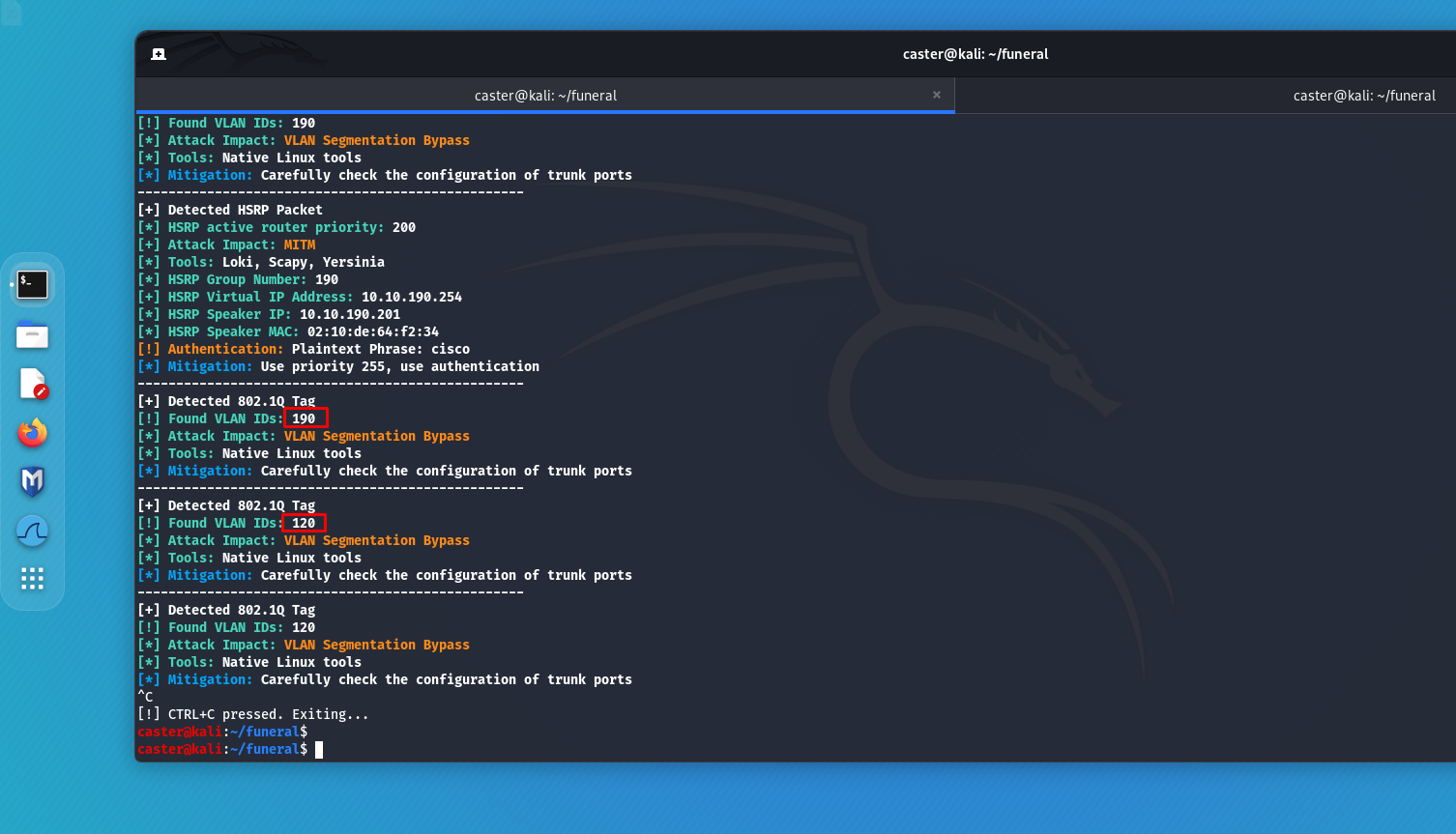
The attacker on the trunk port only needs to listen to the traffic, extract numeric VLAN IDs, then use them to create virtual interfaces and jump to the target VLAN segments.
Mitigations
It is necessary to disable the DTP protocol on all switch ports, as well as disable all switch ports in use and move them all to a separate VLAN 666 SHUTDOWN
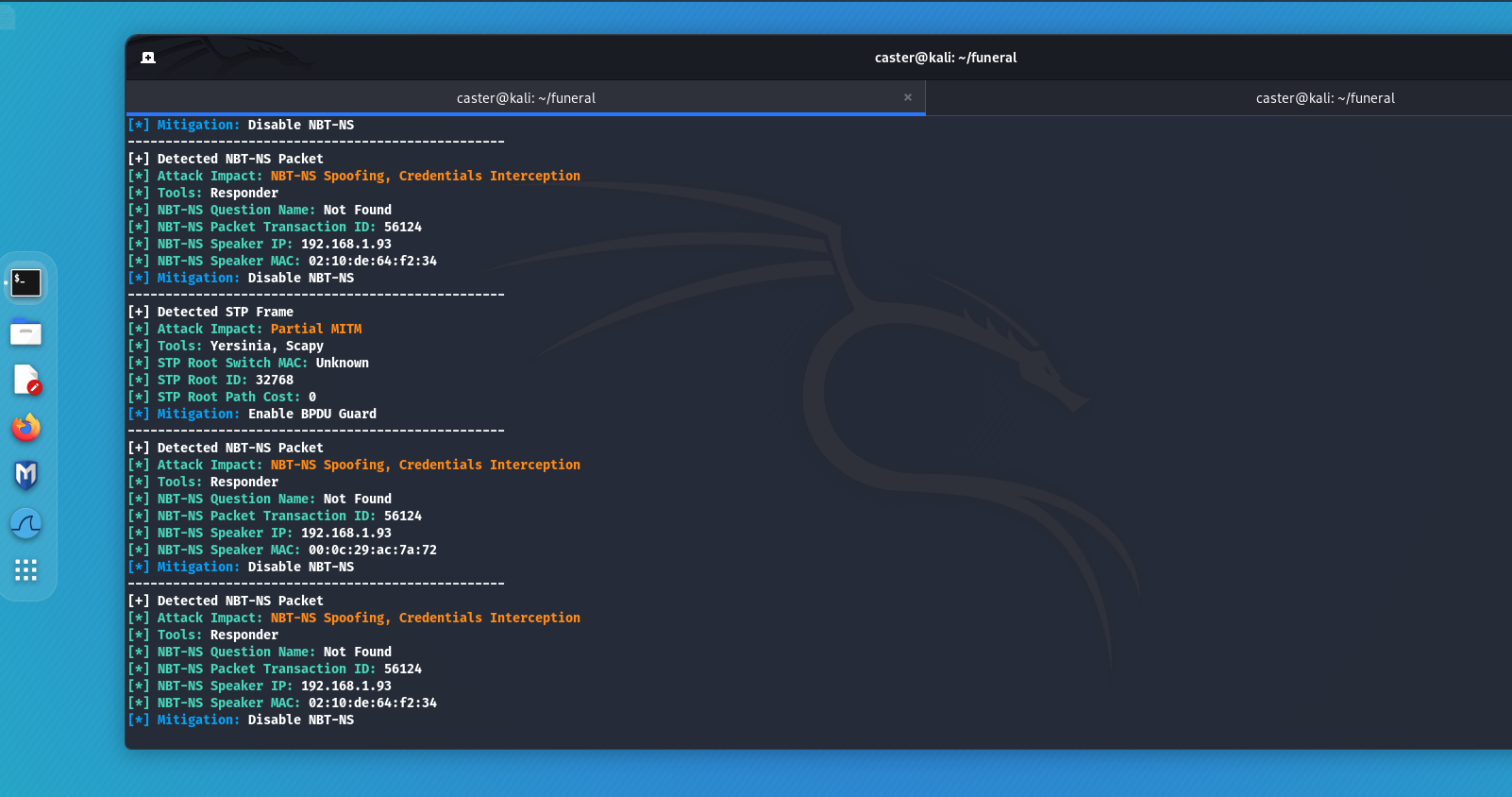
Spanning Tree
STP (Spanning Tree Protocol) - is a link layer protocol that prevents a broadcast storm in a network by blocking redundant connections. It is used in every enterprise network. This protocol can be attacked by hijacking the Root role. This attack executes by sending the BPDU frame with the lowest priority value. As a result, an attacker can perform a partial MITM attack, because not all traffic runs through the root switch.
With Above you can detect an STP frame and build a potential network attack vector.
caster@kali:~$ sudo above --interface eth0 --timer 100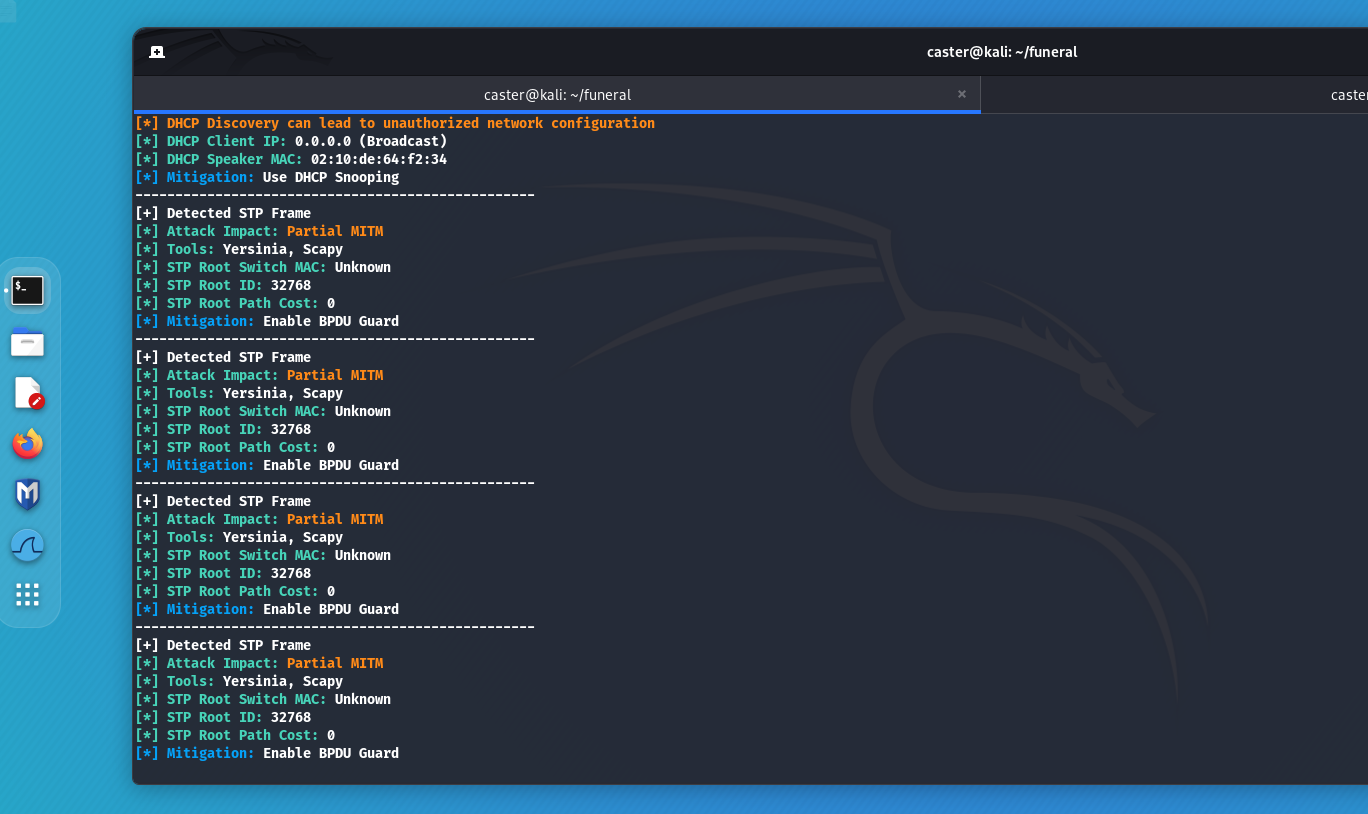
Mitigations
To thwart STP attacks on the protocol, all you need to do is enable BPDU Guard. This security mechanism will shut down a port if a BPDU frame arrives on it (which the attacker does), and the presence of a BPDU frame on user ports is clearly an anomaly, because only switches send BPDU frames
Dynamic Routing
Dynamic routing is a software process in which routers on a network automatically exchange routing information. Dynamic routing is used on every major corporate network, but network administrators often forget about the security of the dynamic routing domain.
If an attacker sees dynamic routing protocols hello packet activity on the air, he can connect to the routing domain and perform the following attacks:
- Subnets Discovery: The attacker can obtain information about existing subnets, allowing him to better understand the network topology and plan further attacks. This attack occurs when an attacker connects to a routing domain, such as with FRR;
- Routing Table Overflow: In this attack, the attacker sends many false routes into the network, causing the routing table of routers to overflow. This can cause a denial of service (DoS) and disrupt network operations;
- Blackhole: An attacker can redirect traffic to non-existent or invalid routes, effectively creating “black holes” where traffic is lost.
caster@kali:~$ sudo above --interface eth0 --timer 100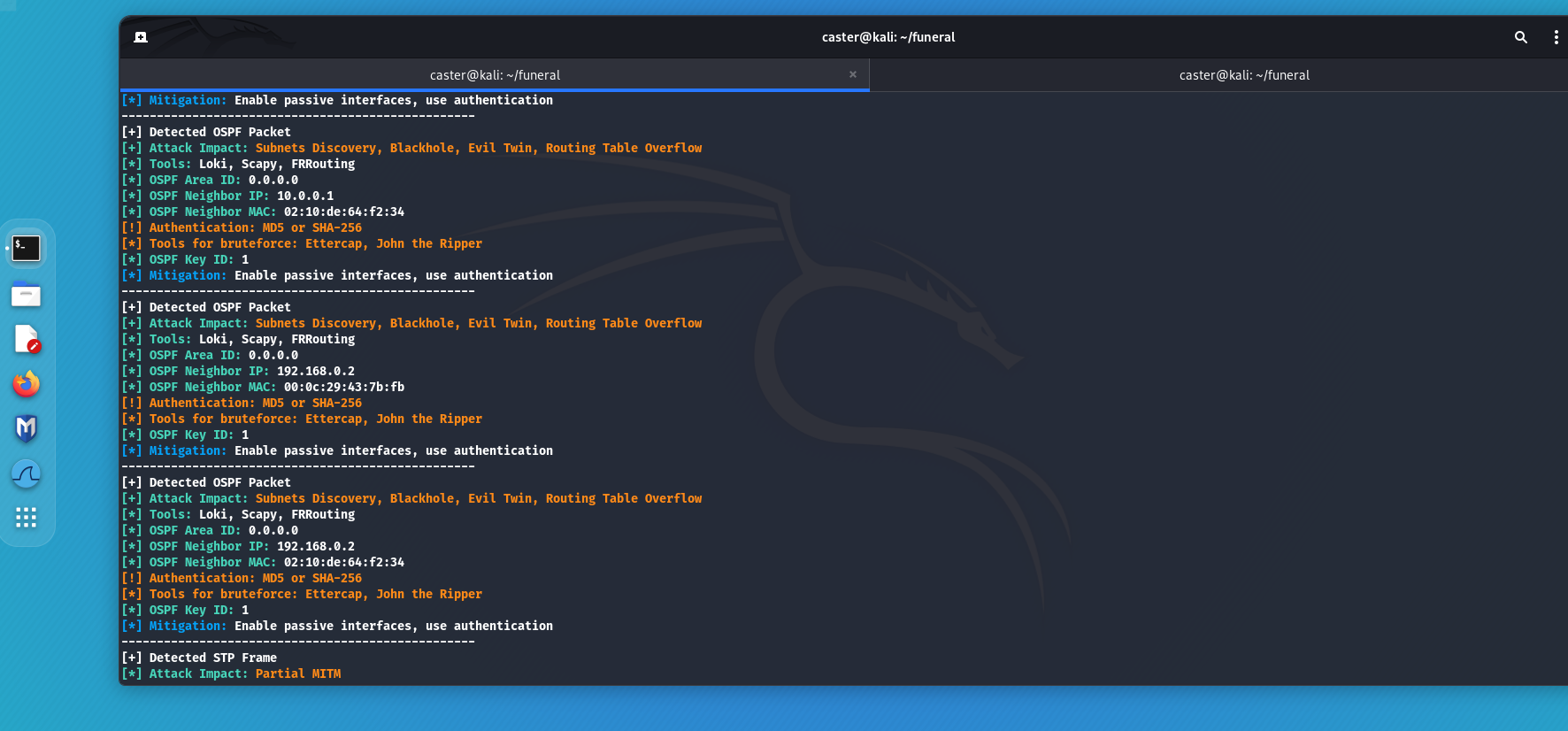
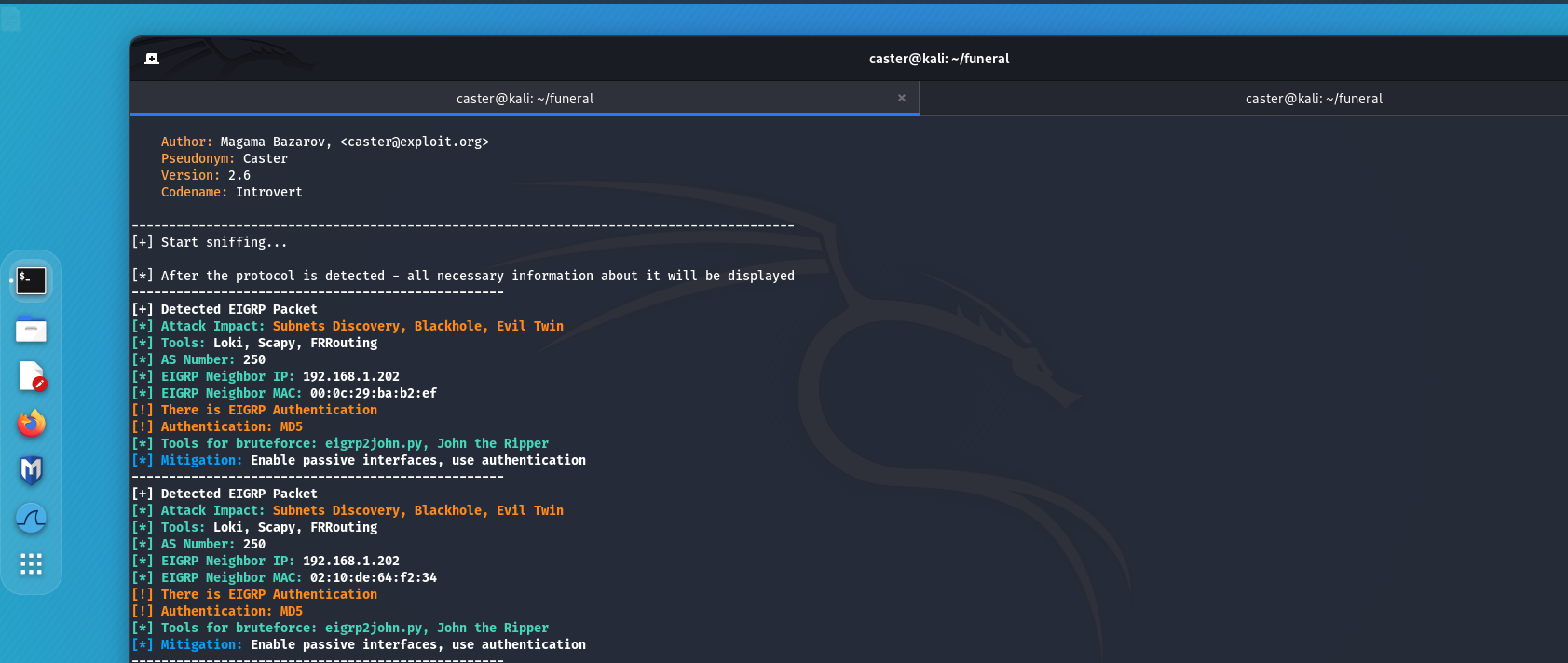
Mitigations
- Passive interfaces are network interfaces on which the router neither sends nor receives routing messages. They can be used to reduce redundant exchange of routing information and to protect the network from certain types of attacks.
- Authentication: The use of routing packet authentication helps ensure that the router from which the information is coming is a trusted device. However, when setting up authentication, I don't advise you to relax. If you are going to protect the routing domain using authentication, make sure that these passwords are strong enough. They are hashed using cryptographic hash functions, and an attacker will be able to read the hash values from a traffic dump and brute force the password. With the resulting password, he can easily connect to the routing domain.
First Hop Redundancy
FHRP (First Hop Redundancy Protocol) - is a group of network protocols that provide fault tolerance and availability to the first node (router or gateway) in a network. The main purpose of FHRP is to ensure that the network continues to operate smoothly in the event of a failure of one of the routers or gateways by providing an alternate path for traffic.
The basic protocols of FHRP are:
- HSRP (Hot Standby Router Protocol):
- A protocol developed by Cisco.
- Creates a standby router group where one router is designated as the active router and the rest are designated as standby routers.
- If the active router fails, one of the standby routers becomes the active router.
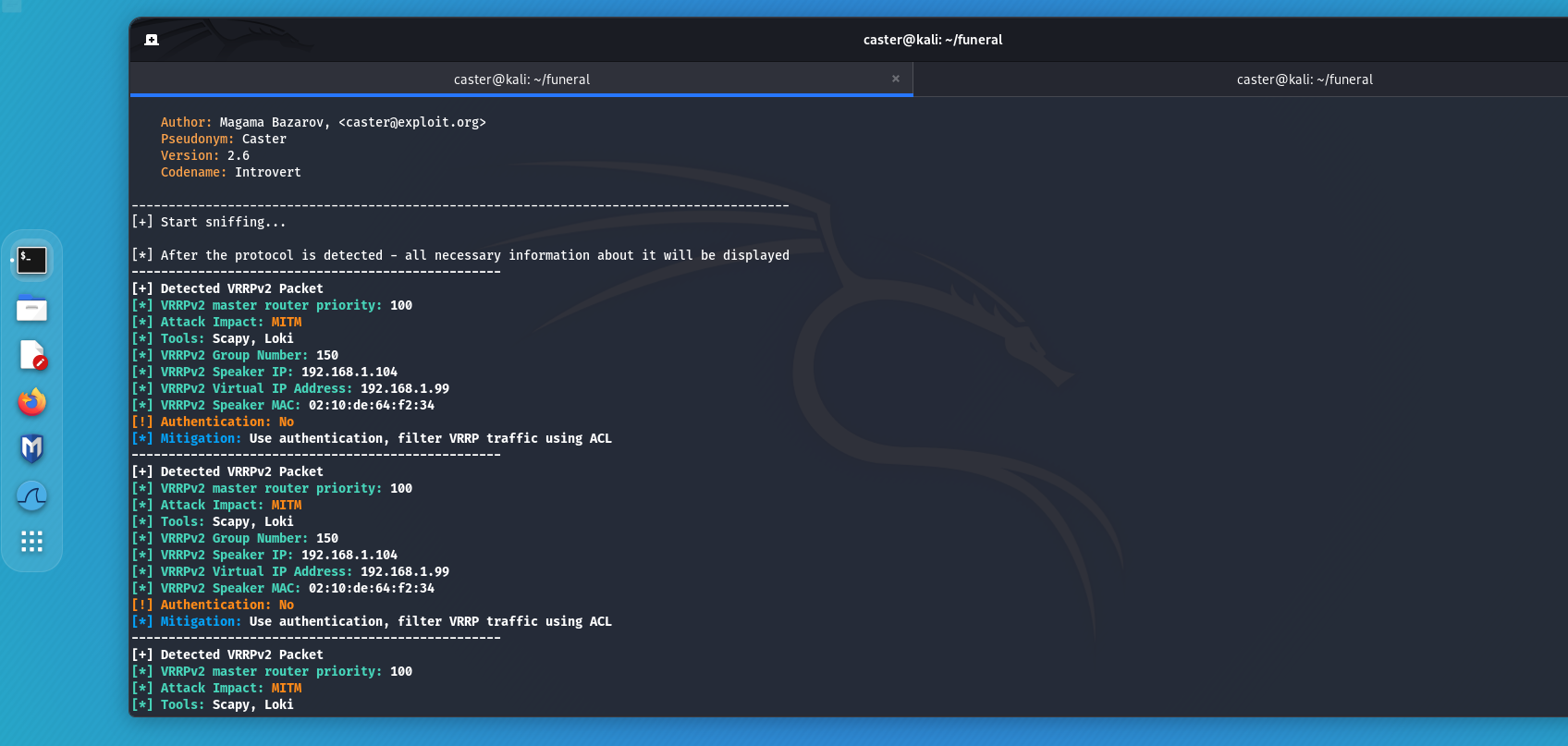
- VRRP (Virtual Router Redundancy Protocol):
- An open standard developed by the IETF.
- Works similarly to HSRP, but is supported by a wide range of equipment from different manufacturers.
- Designates one router in a group as the master and the others as backups.
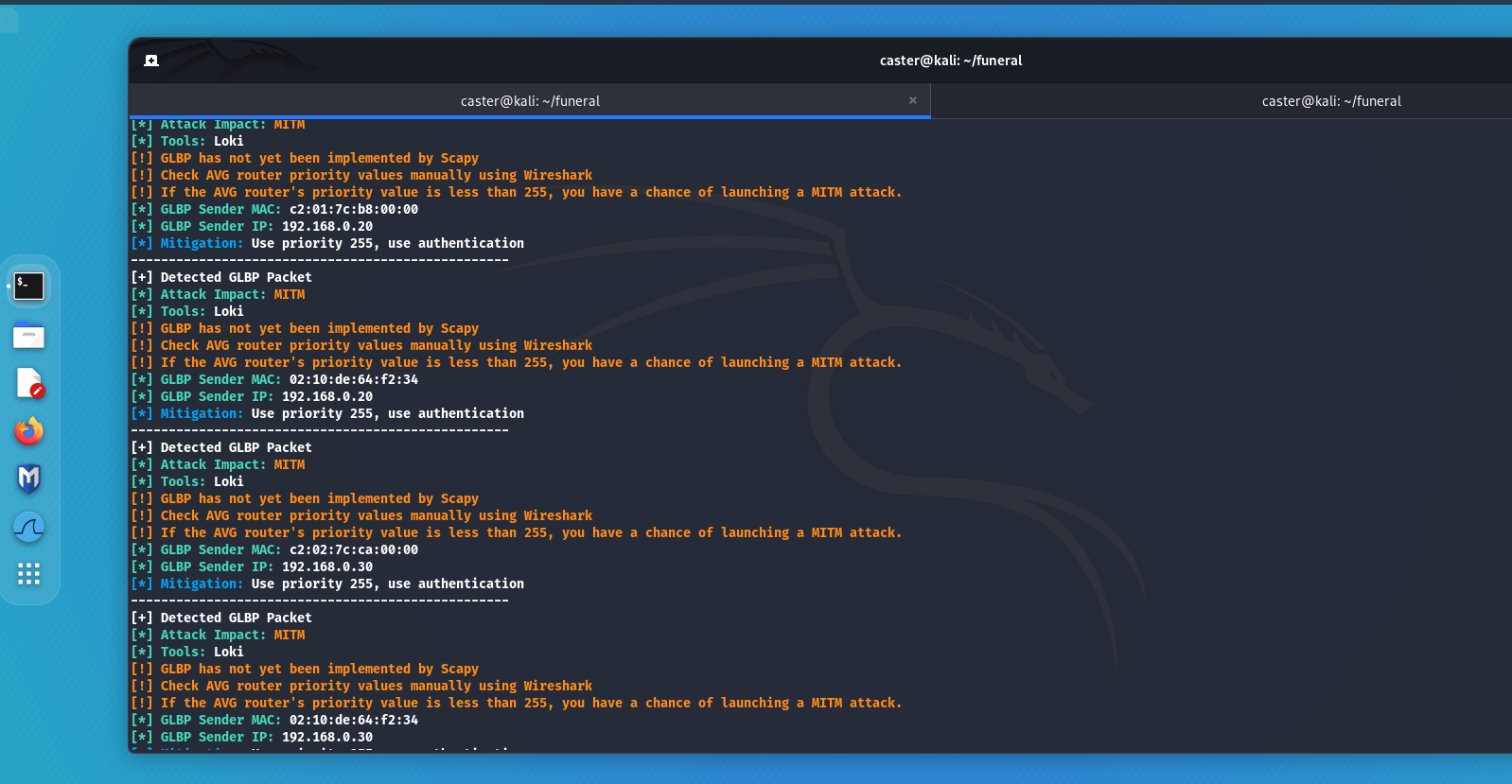
- GLBP (Gateway Load Balancing Protocol):
- A protocol developed by Cisco.
- In addition to providing fault tolerance, also distributes the load among multiple gateways.
- Uses active virtual gateway (AVG) to manage load balancing between active virtual forwarders (AVF).
FHRP speakers use special MCAST messages to communicate with each other. They can be seen on the air by an attacker, learning information about the VIP address, group number, authentication, and priority value. If the master value is less than 255, the attacker can inject the packet with the highest priority, thereby hijacking the role of the master. This results in a MITM attack against an entire logical segment.
caster@kali:~$ sudo above --interface eth0 --timer 100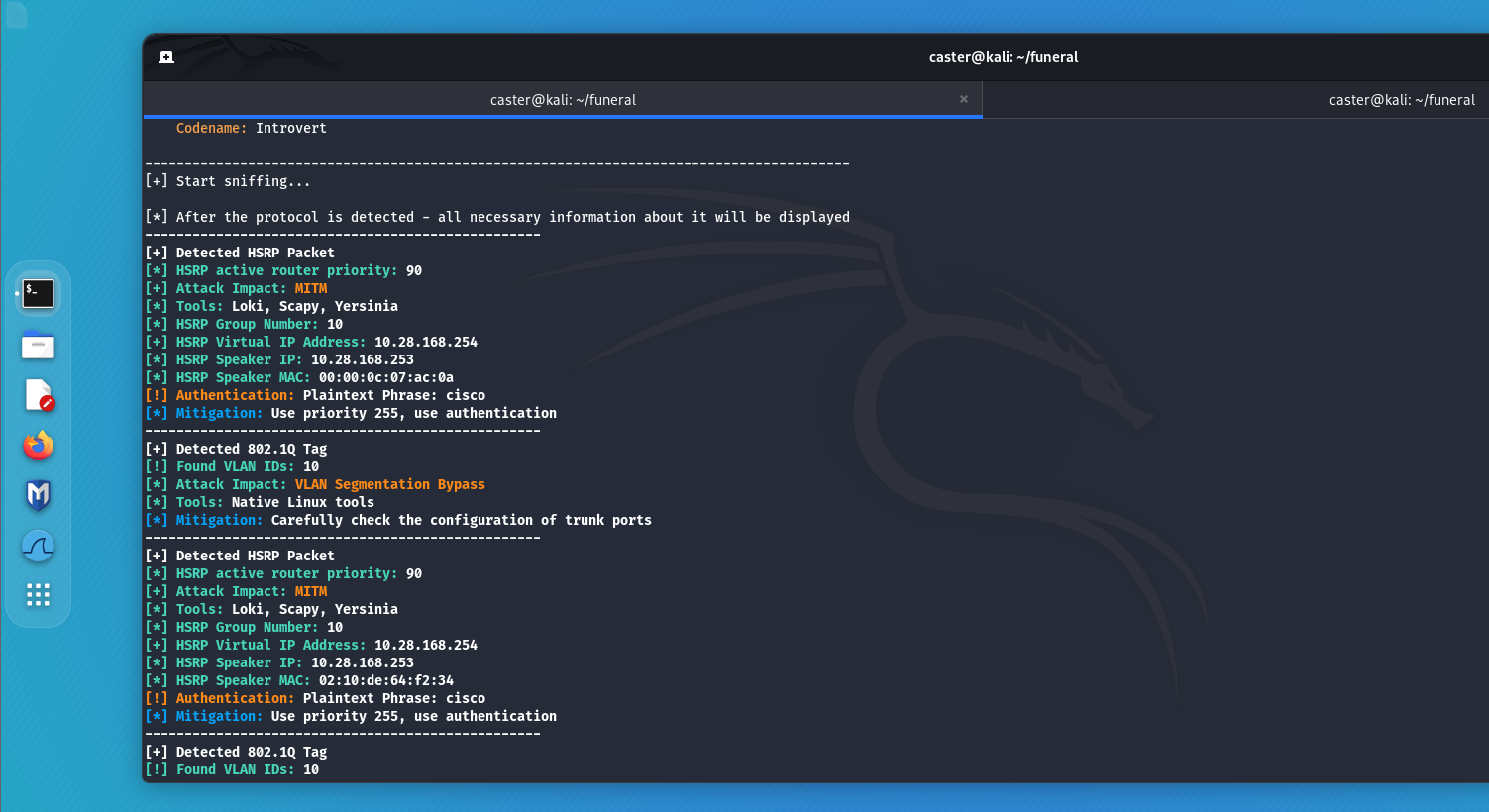
Mitigations
- Configure authentication for FHRP protocols (HSRP, VRRP, GLBP) to ensure that only trusted devices can participate in the exchange of routing information.
- Configure ACLs to allow only trusted devices to send and receive FHRP messages.
Name Resolution Protocol Attacks
One of the most common attacks on Windows machines involves an attacker responding to LLMNR/NBT-NS/MDNS requests from legitimate devices and impersonating the requested hosts. A tool often used for this attack is Responder, which automates the process. As a result of LLMNR/NBT-NS/MDNS poisoning, the attacker obtains credentials in the form of a NetNTLMv2-SSP hash from the account from which the request was generated. These protocols are also used in an Active Directory environment.
Above can capture the activity of these protocols and the attacker will realize that he has a chance at LLMNR/NBT-NS Poisoning
caster@kali:~$ sudo above --interface eth0 --timer 100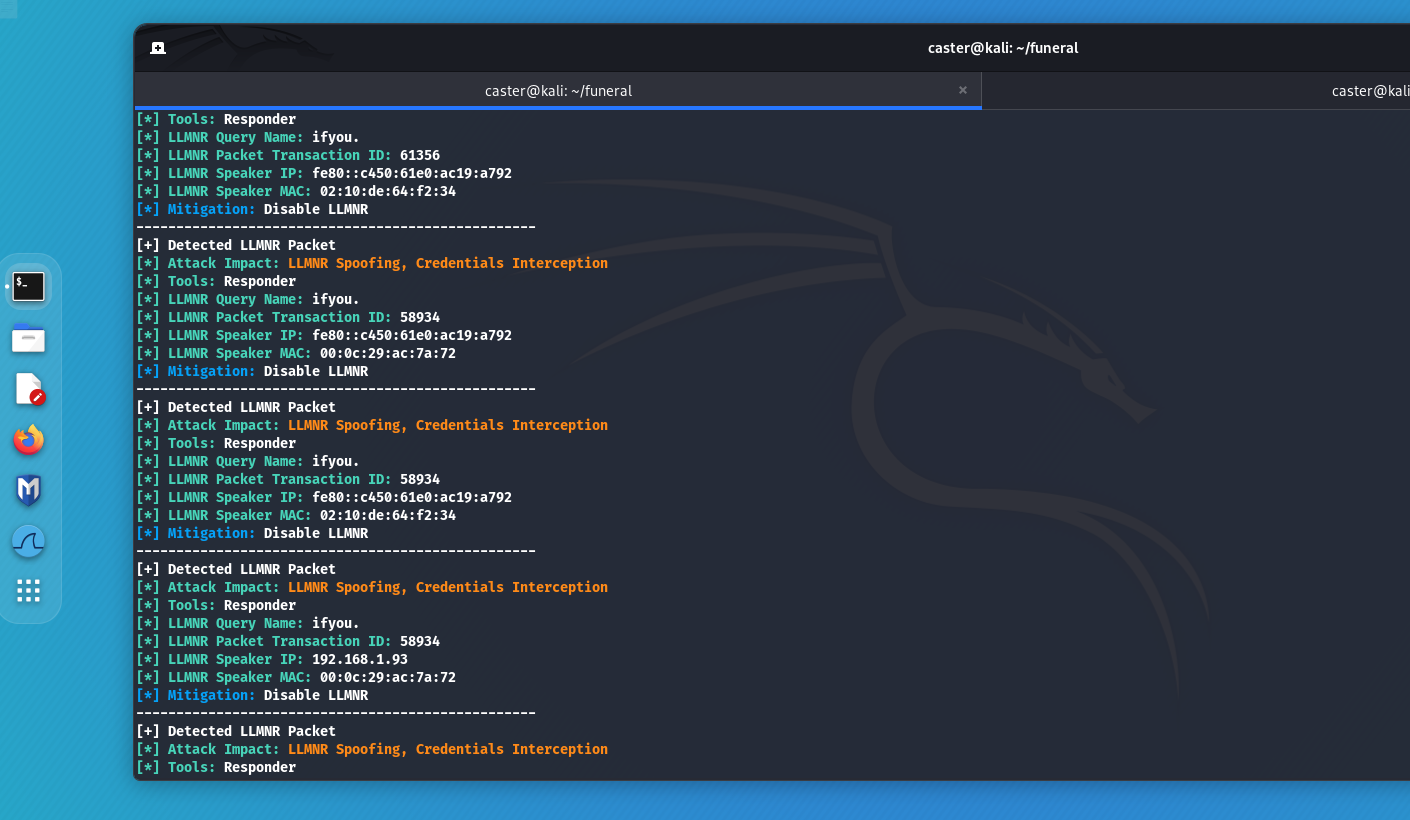
Mitigations
- Disable LLMNR/NBT-NS protocols.
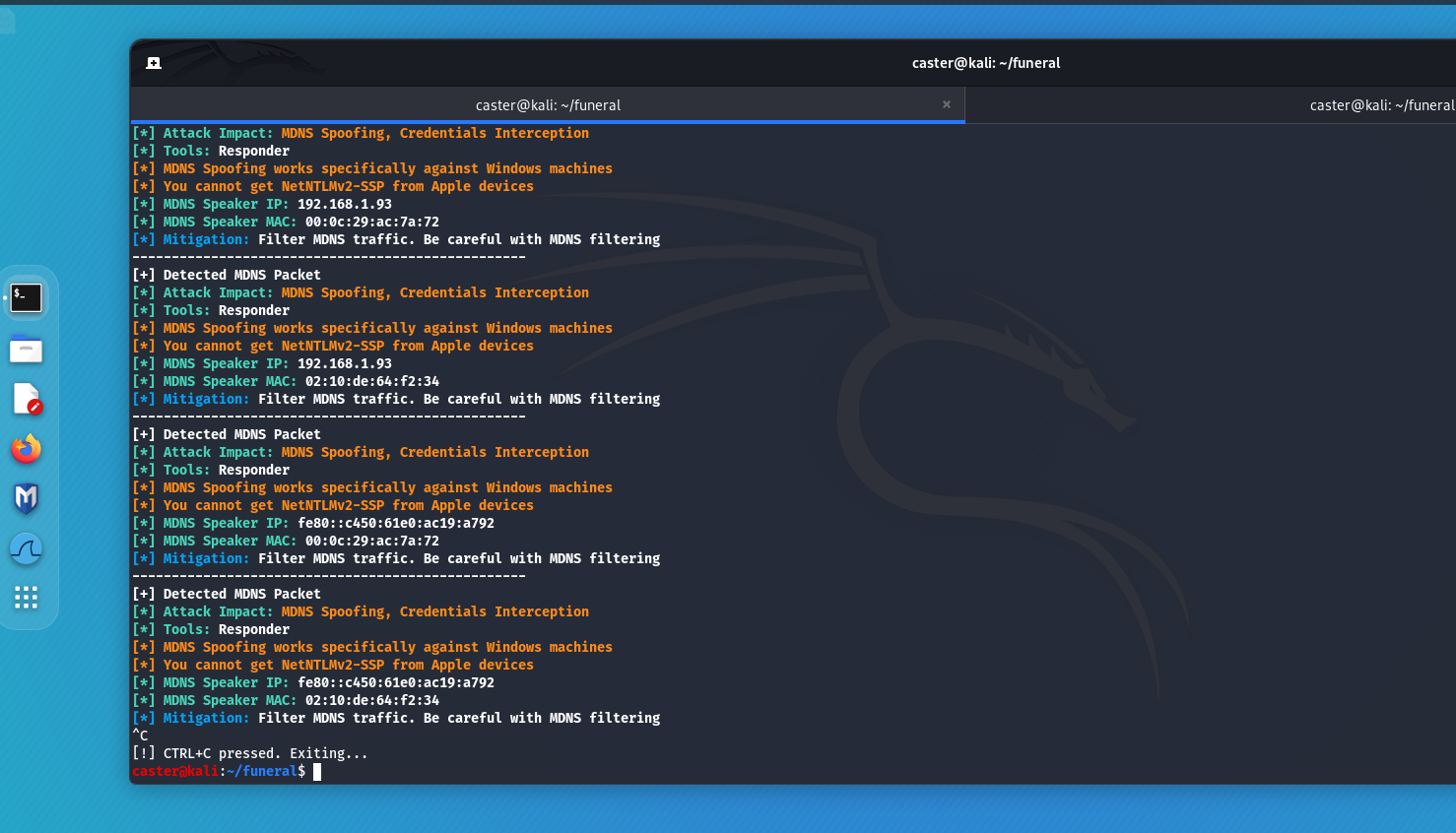
MDNS, on the other hand, is not so simple... It is used by legitimate hosts, printers, Apple devices, Chromecast. And blocking this protocol can cause network problems. So the best option is to monitor MDNS traffic at the IDS level. Here is an example of a small signature for Suricata:
alert udp any 5353 -> any 5353 (msg: “MDNS Response Packet Detected, Possible MDNS Poisoning”; flow:stateless; content:“|84 00 00 00 00 00 00 00 00 01|”; sid:1000002; rev:1;)
alert - indicates the type of rule. In this case, alert indicates that a warning will be generated when the rule is triggered;
udp - indicates the transport layer protocol to which the rule will respond. udp indicates that the rule applies to UDP traffic;
any 5353 -> any 5353 are the source and destination network addresses and ports. "any" indicates any IP address, and 5353 indicates the port that is used by the MDNS protocol;
msg: "MDNS Response Packet Detected, Possible MDNS Poisoning" is the message that will be displayed when the rule is triggered;
flow:stateless - specifies that the processing and inspection of traffic is independent of the state of the connection. A common practice for UDP traffic where there is no connection established before sending data, connectionless protocol;
content:"|84 00 00 00 00 00 00 00 00 01|" - content that is searched for in the packet, a byte sequence representing a specific part of the MDNS packet, namely the response, which can be an indicator of an attack;
sid:1000002 - the unique rule identifier (SID, or Signature ID). This is a number that uniquely identifies a rule in a rule set;
rev:1 - indicates the version of the rule. This is a number that is incremented when a rule is updated or modified.
IPv6 Takeover (DHCPv6)
DHCPv6 (Dynamic Host Configuration Protocol for IPv6) - is a protocol used to automatically configure IPv6 settings on devices on a network. It allows network devices to automatically obtain settings such as IP address, default gateway, and other settings required for IPv6 networking. Unlike its predecessor DHCP for IPv4, DHCPv6 works exclusively with IPv6 addresses.
However, an IPv6 Takeover attack is possible when it is involved. By using the mitm6 tool and sending DHCPv6 Advertise messages, the attacker imposes itself as a DNS server at the IPv6 level. If the attacker notices DHCPv6 packets activity on the air, it can build a vector for this attack.
caster@kali:~$ sudo above --interface eth0 --timer 100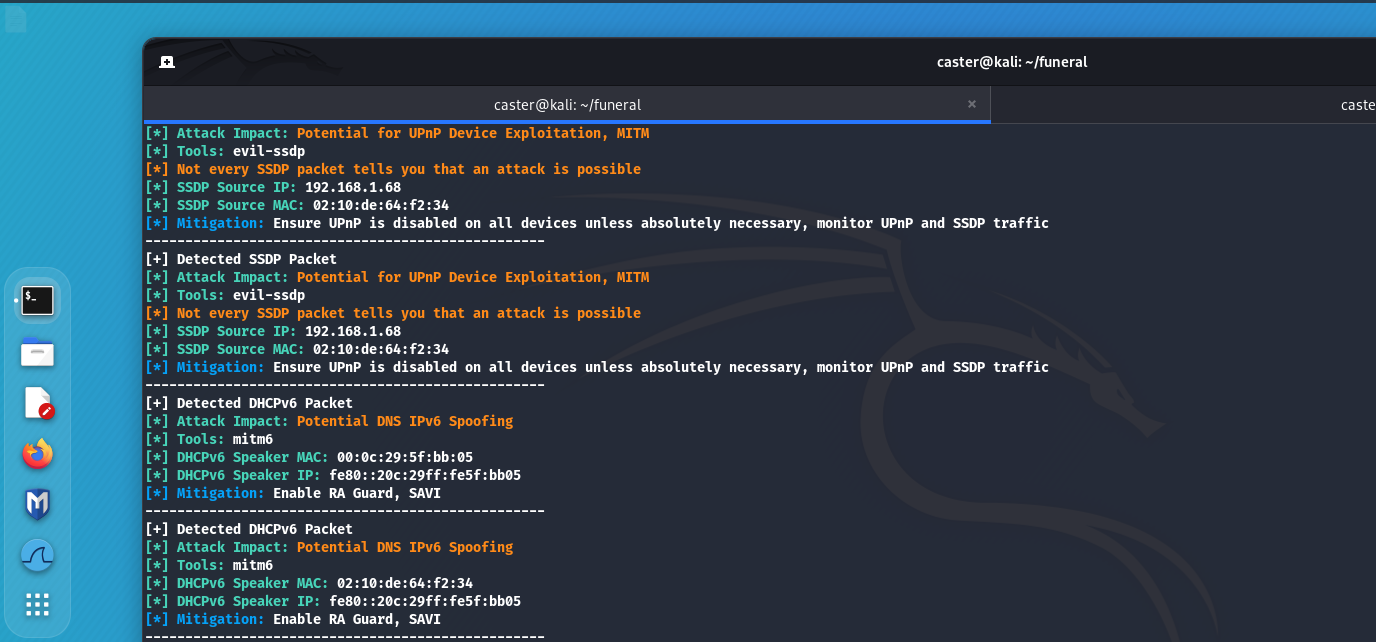
Mitigations
Suricata can be used to detect this attack. Here is an example of such a signature that will detect DHCPv6 Advertise messages inside a user segment. In principle, only a DHCPv6 server can send such messages, which is not expected in the user segment, so this can be considered an anomaly.
alert udp any any -> any 546 (msg:"Suspicious DHCPv6 Advertise Packet Detected, Possible attack using mitm6"; content:"|02|"; depth:1; sid:1000008; rev:1;)
alert - indicates the type of rule. In this case, alert indicates that a warning will be generated when the rule is triggered;
udp - indicates the transport layer protocol to which the rule will respond. udp indicates that the rule applies to UDP traffic;
any any -> any 546 - the first any indicates any source IP address, the second any indicates any source port, the arrow -> indicates the direction of traffic from source to destination, the third any indicates any destination IP address, 546 indicates the destination port, which is the standard port for DHCPv6 clients;
msg: "Suspicious DHCPv6 Advertise Packet Detected, Possible attack using mitm6" is the message that will be displayed when the rule is triggered;
content:"|02|" is an indication of the specific packet content that must be detected for the rule to be triggered. |02| means that the rule is looking for a packet that has the byte 02 in the specified position. An entry in the form |02| is used to denote a hexadecimal value in the content.
depth:1 - specifies how deep in the packet to search for the specified content means that only the first byte of the packet should be checked;
sid:1000008 - the unique rule identifier (SID, or Signature ID). This is a number that uniquely identifies a rule in a rule set;
rev:1 - indicates the version of the rule. This is a number that is incremented when the rule is updated or modified.
Outro
In this article, I demonstrated a way to silently analyze the security of network equipment based solely on traffic analysis. This approach is applicable for both offensive and defensive purposes. It allows you to identify vulnerabilities and potential threats without attracting attention or disrupting network operations. Using this method of analysis helps security professionals effectively protect their infrastructure, ensuring that network devices operate reliably and securely.
