Nihilism: Access Layer Security
Access level security is a sensitive issue, unauthorized connections to the local network can lead to insider attacks and serious damage to the infrastructure. In this article, I will demonstrate a few network security techniques at the access layer.

Access level security is a sensitive issue, unauthorized connections to the local network can lead to insider attacks and serious damage to the infrastructure. In this article, I will demonstrate a few network security techniques at the access layer.
Caster - Nihilism
Genre: Defensive
Label: exploit.org
Release Date: 31.08.2024
Performed by: Caster
Written by: Magama Bazarov
Mastered by: Magama Bazarov
Cover Man: Magama Bazarov (Sony ILCE-7M3, f/5.6, 1/3 sec)Intro
Endpoints security is quite a hot issue, it is important to be able to provide access layer security to protect the network from unauthorized connections to the network. This article is about link layer security and legitimate hosts. This layer of the network is prone to attacks such as spoofing, VLAN Hopping, DHCP Spoofing, IPv6 Takeover and others.
I have prepared the following infrastructure for this article:
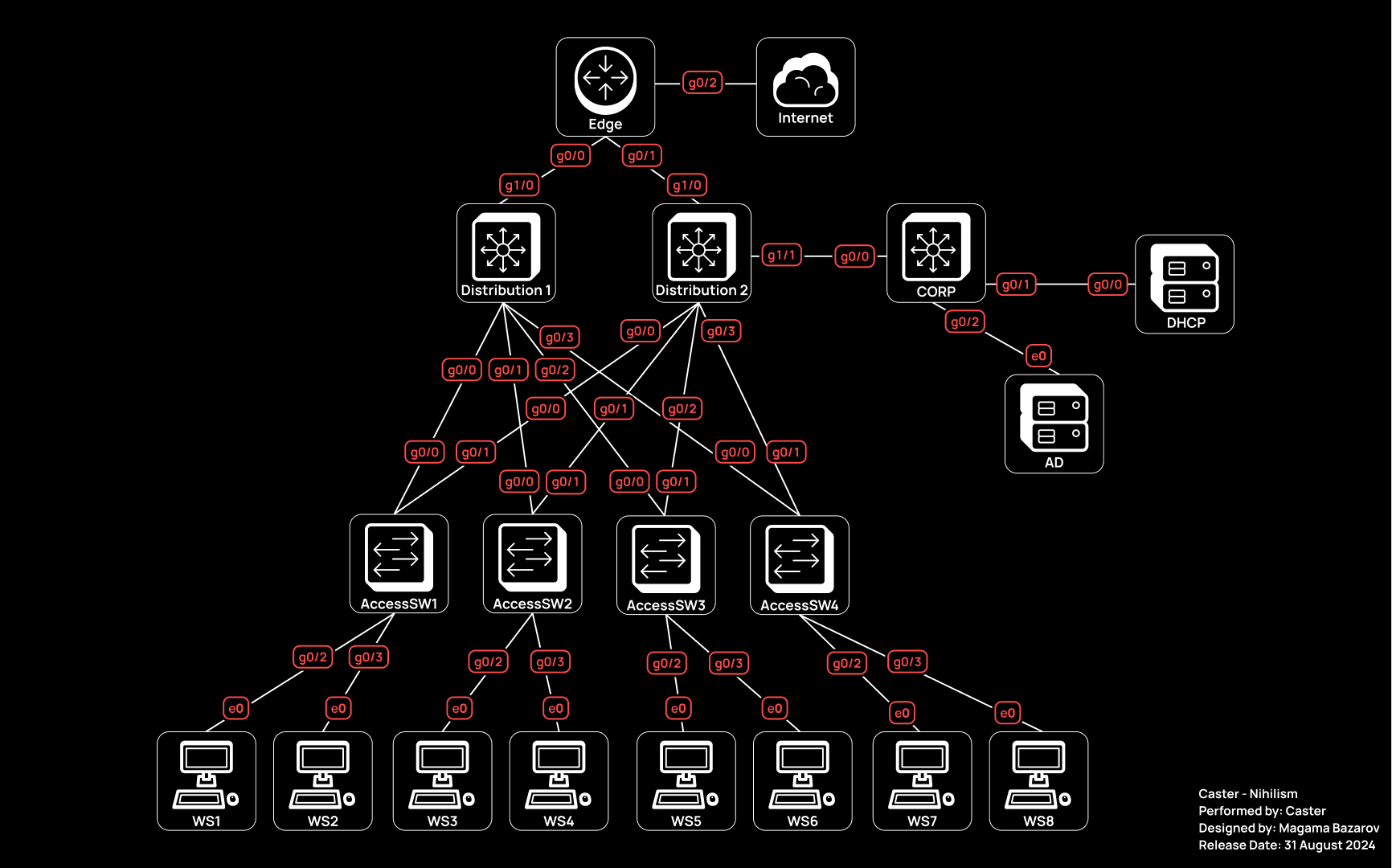
It is simple, consists of two levels: access level and distribution level.
There is also an Edge router and an additional switch in the distribution layer where AD controller and DHCP server are connected. The distribution layer will be responsible for dynamic routing and Inter-VLAN Routing. Cisco vIOS images are used as networking . The end hosts are using Windows 10 Enterprise. This is where I will be demonstrating sample configurations for a better understanding of how and what works.
| Switch | VLAN |
|---|---|
| AccessSW1 | 20 |
| AccessSW2 | 40 |
| AccessSW3 | 60 |
| AccessSW4 | 80 |
| VLAN | Subnet |
|---|---|
| 20 | 10.10.20.0/24 |
| 40 | 10.10.40.0/24 |
| 60 | 10.10.60.0/24 |
| 80 | 10.10.80.0/24 |
| VLAN | Subnets |
|---|---|
| 20 | 10.10.20.254 (HSRP) |
| 40 | 10.10.40.254 (HSRP) |
| 60 | 10.10.60.254 (HSRP) |
| 80 | 10.10.80.254 (HSRP) |
| Host | VLAN |
|---|---|
| WS1 | 20 |
| WS2 | 20 |
| WS3 | 40 |
| WS4 | 40 |
| WS5 | 60 |
| WS6 | 60 |
| WS7 | 80 |
| WS8 | 80 |
Port Security
It is a classic of the switch port security genre, in fact, with this feature you can simply limit the number of ports that can be behind a certain switch port. Port Security is not a panacea and will not really provide a level of access protection against unauthorized connections. It is more of a hardening and protection against CAM Table Overflow attack.
By the way, a few words about it. This attack is taught in many places, but in real conditions it is of little use, and besides, it can cause damage to the infrastructure. Unicast flood occurs when a switch's CAM table is flooded. This is a phenomenon when unicast traffic becomes broadcast. This can seriously affect the stability of the segment. This attack is taught in training materials, but it cannot be used in the real world.
Scenario 1: Restriction on one MAC address
If only one device, such as a workstation or laptop, is connected to a switch port, it is recommended that you configure Port Security with a limit of one MAC address. This minimizes the risk of unauthorized connection of another device. But before configuring Port Security, the switch ports must be configured in `Access' mode and associated with a VLAN ID.
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# switchport port-security
AccessSW1(config-if)# switchport port-security maximum 1
AccessSW1(config-if)# switchport port-security violation restrict
AccessSW1(config-if)# switchport port-security mac-address stickyAccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# switchport port-security
AccessSW2(config-if)# switchport port-security maximum 1
AccessSW2(config-if)# switchport port-security violation restrict
AccessSW2(config-if)# switchport port-security mac-address stickyAccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# switchport port-security
AccessSW3(config-if)# switchport port-security maximum 1
AccessSW3(config-if)# switchport port-security violation restrict
AccessSW3(config-if)# switchport port-security mac-address stickyAccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# switchport port-security
AccessSW4(config-if)# switchport port-security maximum 1
AccessSW4(config-if)# switchport port-security violation restrict
AccessSW4(config-if)# switchport port-security mac-address stickyg0/2andg0/3are connections to end stations
maximum 1: limits the number of MAC addresses that can be registered on the port to one;
violation restrict: if a device with a different MAC address attempts to connect, the port will block traffic from the new device and send notifications to the administrator;
mac-address sticky: allows the switch to automatically memorize the first MAC address connected to the port and store it in the configuration, even after the device reboots.
Scenario 2: Restriction of two MAC addresses for VoIP
In cases where a VoIP phone and a computer are connected to the port in a burst, you must allow two MAC addresses. VoIP phones usually require a separate MAC address for themselves and for the computer connected to them. The value would be raised to 2
Nihilism(config-if)# switchport port-security maximum 2Depending on the usage scenario, you can configure the port to support one or two MAC addresses, allowing you to adapt the settings to different environments, such as VoIP devices. This is a classic of the genre and a simple example of simple protection against unauthorized network connectivity, but Port Security is not a panacea and 802.1X is much more impressive in this regard.
BPDU Guard
The STP protocol is a solution to the problem of avoiding broadcast storms, this is achieved by blocking redundant connections between switches. The STP protocol is 39 years old and is used in every corporate network. The STP tree can be vulnerable to spoofing attacks, by sending unauthorized BPDU frames that can affect the tree structure. The most popular attack from this class is STP Root Switch Spoofing. In this attack, the attacker generates a special BPDU frame with zero priority value to hijack the role of the root switch. However, this will only result in a partial MITM attack, not all traffic goes through the root switch.
How does BPDU Guard work?
BPDU Guard works as follows: if a BPDU frame is received on a switch port that is configured as an access port, that port will automatically be placed in the error-disabled state. This prevents any attempt to modify the STP tree structure by unauthorized devices connected to the port.
BPDU Guard Configuration
BPDU Guard is provided to protect the STP tree. This function works very simply: when a BPDU frame is received on a user port, the port itself will be blocked. The presence of BPDU frames on the ports of end stations can indicate either an anomaly or an attack attempt. As with Port Security, the switch port must be in Access mode before BPDU Guard can be configured
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if-range)# spanning-tree bpduguard enable
AccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if-range)# spanning-tree bpduguard enable
AccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if-range)# spanning-tree bpduguard enable
AccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if-range)# spanning-tree bpduguard enable
g0/2andg0/3are connections to end stations
Port Recovery after BPDU Guard triggering
If BPDU Guard puts the port in an error-disabled state, it can be restored using the command:
AccessSW1(config)# errdisable recovery cause bpduguardAccessSW2(config)# errdisable recovery cause bpduguardAccessSW3(config)# errdisable recovery cause bpduguardAccessSW4(config)# errdisable recovery cause bpduguardThis is how you can protect the access layer from STP tree attacks.
DHCP Snooping
DHCP Snooping - is a security feature of the switch to protect the DHCP server from attrition and spoofing attacks. The technology is actually very simple and works based on the logic of trusted and untrusted ports:
- Trusted Port: this port mode is configured between intermediate devices, such as: 1) switch-to-switch, 2) switch-to-router;
- Untrusted Port: this port mode is configured on end station ports, for example: computers, laptops, IP telephony, printers
Triggers
DHCP Snooping provides switch-level DHCP server protection by blocking DHCP messages that may originate from unauthorized DHCP servers on untrusted ports, among them:
- DHCP Offer: This is a DHCP server's response to a client request to offer an IP address. Unauthorized servers may attempt to send spoofed DHCP Offer messages to take control of IP addressing on the network;
- DHCP Ack: This is a confirmation message from the DHCP server to the client to assign an IP address. Unreliable servers may attempt to send a DHCP Ack to get the client to accept incorrect network settings;
- DHCP Nak: this is a message indicating that an IP address has been denied. An attacking server may use DHCP Nak to prevent a client from obtaining an IP address from a legitimate server.
Table Saturation
Another important aspect of rushing the implementation of DHCP Snooping is to ensure that the DHCP Snooping table is fully and accurately saturated with all legitimate hosts on the network. This table serves as the basis for many network security mechanisms, particularly Dynamic ARP Inspection (DAI), why is this important?
- Protection against ARP spoofing: DAI uses the DHCP Snooping table to check the matching of ARP requests and responses in the network. This check consists of matching MAC addresses and IP addresses against entries stored in the DHCP Snooping table. If an entry in the table is missing, the DAI will not be able to authenticate the ARP packet, which can result in legitimate traffic being blocked or malicious traffic being allowed through. Saturating the table with all legitimate hosts allows the DAI to effectively protect the network from ARP spoofing;
- Ensuring filtering accuracy: If the DHCP Snooping table is not sufficiently populated, the DAI may misinterpret ARP requests, which can lead to false positives and unnecessary traffic blocking. This can negatively impact network performance and cause accessibility issues for legitimate users;
- Attack Resistance: A fully saturated DHCP Snooping table reduces the likelihood of successful attacks such as Man-in-the-Middle (MitM) because the DAI will be able to accurately identify IP and MAC address matches. This prevents data interception or spoofing on the network.
How to achieve full saturation
- Monitoring DHCP traffic: Make sure that all hosts on the network obtain IP addresses through trusted DHCP servers so that their data is correctly written to the DHCP Snooping table;
- Customize GPO: Create a script that sequentially executes the
ipconfig /releaseandipconfig /renewcommands on client devices. This will force computers to request new IP addresses from the DHCP server. - Policy Enforcement: Enforce this script via Group Policy in Active Directory so that it will be executed the next time users log on or at a specified time. This will ensure that DHCP entries are updated for all devices on the network.
- Customize GPO: Create a script that sequentially executes the
Force IP address updates via GPO: To ensure that all computers on the network update their DHCP requests and thus are correctly written to the DHCP Snooping table, you can use Group Policy (GPO) in Windows to execute the ipconfig /release and ipconfig /renew commands on all client machines:An example of a simple PowerShell script to do this is:
ipconfig /release
ipconfig /renewThis approach will automatically update IP addresses on all managed devices, ensuring that the DHCP Snooping table is populated with up-to-date data on all legitimate hosts.
This is a very important aspect, if even one legitimate host is not in the DHCP Snooping table, that host can run into serious problems when Dynamic ARP Inspection (DAI) is enabled. DAI will inspect all ARP packets and match them against the information in the DHCP Snooping table. If there is no record of the host, the DAI may treat its ARP packets as suspicious or potentially malicious, resulting in blocking traffic from that host. This can completely disrupt the host's network and cause significant disruptions to the host's operation.
Enabling DHCP Snooping
Now you need to globally enable DHCP Snooping. And it must also be enabled selectively on VLANs:
AccessSW1(config)# ip dhcp snooping
AccessSW1(config)# ip dhcp snooping vlan 20AccessSW2(config)# ip dhcp snooping
AccessSW2(config)# ip dhcp snooping vlan 40AccessSW3(config)# ip dhcp snooping
AccessSW3(config)# ip dhcp snooping vlan 60AccessSW4(config)# ip dhcp snooping
AccessSW4(config)# ip dhcp snooping vlan 80Trust and Untrust Ports
Now you need to configure trusted and untrusted ports. However, you should realize that when DHCP Snooping is activated, all ports on the switch automatically become untrusted and you need to explicitly define trusted ports. First define trusted and untrusted ports, then globally enable DHCP Snooping, that's the rule. In my case, the trusted ports are the connections from the access layer switches to the distribution layer switch and the untrusted ports are the endpoints on Windows.
Trusted:
AccessSW1(config)# interface range g0/0, g0/1
AccessSW1(config-if)# ip dhcp snooping trustAccessSW2(config)# interface range g0/0, g0/1
AccessSW2(config-if)# ip dhcp snooping trustAccessSW3(config)# interface range g0/0, g0/1
AccessSW3(config-if)# ip dhcp snooping trustAccessSW4(config)# interface range g0/0, g0/1
AccessSW4(config-if)# ip dhcp snooping trustg0/0andg0/1are connections up to the distribution level switches
Limit Rate for DHCP Snooping: Protection against DHCP Exhaustion
DHCP Exhaustion - is an attack in which an attacker sends multiple spoofed DHCP requests in an attempt to exhaust the pool of available IP addresses on a DHCP server. As a result, legitimate devices are unable to obtain an IP address and connect to the network, resulting in a denial of service (DoS). To protect against such attacks on switches with DHCP Snooping enabled, you can use the Limit Rate mechanism, which limits the rate at which DHCP requests are processed on a port.
What is Limit Rate?
Limit Rate - is a feature that allows you to limit the number of DHCP requests that the switch accepts on a particular port in a given period of time. This measure prevents overloading the DHCP server and protects the network from DHCP Exhaustion attacks. When Limit Rate is enabled, the switch monitors the number of DHCP requests received on a port. If the number of requests exceeds the set value for a set amount of time, the excess requests will be blocked. This prevents a DHCP Exhaustion attack by reducing the likelihood of exhausting the IP address pool on the DHCP server.
Limit Rate is configured on the interface. Specify the maximum number of DHCP requests that can be processed on a port per second. For example, to limit the number of requests to 10 per second:
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# ip dhcp snooping limit rate 10AccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# ip dhcp snooping limit rate 10AccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# ip dhcp snooping limit rate 10AccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# ip dhcp snooping limit rate 10g0/2andg0/3are connections to end stations
This value can be adjusted depending on the expected load on the port and the level of protection required. A lower value helps protect the network better, but may limit legitimate requests if set too low. But this value can always be adjusted based on your wishes.
Verification
For example, on an AccessSW1 switch, you can test the operation of DHCP Snooping:
AccessSW1#show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
50:00:00:0B:00:00 10.10.20.1 86072 dhcp-snooping 20 GigabitEthernet0/2
50:00:00:11:00:00 10.10.20.2 86046 dhcp-snooping 20 GigabitEthernet0/3In my case, only two computers are on VLAN 20, I re-requested the address on them via DHCP and their data ended up in the DHCP Snooping database. Again, on your network this table should be completely populated with all your legitimate hosts.
Saving the DHCP Snooping Database
To ensure stable operation of DHCP Snooping and related mechanisms such as Dynamic ARP Inspection (DAI), it is important to keep the DHCP Snooping database on the switch. This prevents data loss when the switch reboots and prevents DAI from blocking legitimate connections due to missing information about them in the DHCP Snooping table.
To save and restore the DHCP Snooping table after a switch reboot, you must enable the database save feature:
AccessSW1(config)# ip dhcp snooping database flash:dhcp_snoop.dbAccessSW2(config)# ip dhcp snooping database flash:dhcp_snoop.dbAccessSW3(config)# ip dhcp snooping database flash:dhcp_snoop.dbAccessSW4(config)# ip dhcp snooping database flash:dhcp_snoop.dbYou can also make the DHCP Snooping database update automatically:
AccessSW1(config)# ip dhcp snooping database write-delay <sec>AccessSW2(config)# ip dhcp snooping database write-delay <sec>AccessSW3(config)# ip dhcp snooping database write-delay <sec>AccessSW4(config)# ip dhcp snooping database write-delay <sec>Here <sec> is the interval at which the database will be updated on the flash memory. Typically, a value between 10 and 300 seconds is used, depending on network activity.
Here, by the way, is how the DHCP Snooping database file will be stored inside the AccessSW1 switch memory:
AccessSW1#show flash:
273 211 Aug 30 2024 09:28:36 dhcp_snoop.dbDHCP Option 82
DHCP Option 82, also known as the “DHCP Relay Agent Information Option,” is additional information that the switch adds to DHCP requests that pass through it. It includes information about the port and VLAN through which the request was received. This information helps the DHCP server to more accurately manage IP address allocation and to keep track of which switch and port the request was sent through.
If you don't need it, you can turn it off:
AccessSW1(config)# no ip dhcp snooping information optionAccessSW2(config)# no ip dhcp snooping information optionAccessSW3(config)# no ip dhcp snooping information optionAccessSW4(config)# no ip dhcp snooping information optionThis is how you can protect a DHCP server from spoofing and attrition attacks. The most important thing is to understand the entire network and how everything works to avoid shooting yourself in the foot.
Dynamic ARP Inspection
Dynamic ARP Inspection (DAI) - is a switch security feature designed to protect the network from ARP Spoofing, one of the most common Man-in-the-Middle (MITM) attacks. Within corporate networks, this technique is actively used by pentesters to test for vulnerabilities, so it is important to be able to effectively protect the network from such threats. The problem with ARP is that there is no authentication mechanism, so hosts trust any ARP frames they receive, making them vulnerable to spoofing attacks.
DAI and DHCP Snooping Communication
DAI integrates closely with DHCP Snooping, using the DHCP Snooping table to inspect and filter ARP packets. When DAI is active, it inspects every ARP packet that passes through the switch and maps it to information contained in the DHCP Snooping table. This table stores MAC address, IP address, and port mappings derived from DHCP traffic.
Why it matters?
- Authentication of ARP packets: DAI uses the DHCP Snooping table to check the legitimacy of ARP packets. If an ARP packet does not match the data in the table, it can be blocked, preventing a possible attack;
- Prevent Man-in-the-Middle (MitM) attacks: DAI effectively protects the network from MitM attacks, where an attacker attempts to spoof MAC addresses and intercept traffic between devices;
- Blocking malicious ARP packets: If DAI detects that an ARP packet is attempting to change the IP to MAC address mapping in the table, it blocks the packet, protecting the network from address spoofing.
DAI Configuration
For DAI to work successfully, you must first configure DHCP Snooping so that the DHCP Snooping table is populated with up-to-date data on all legitimate hosts. You can then proceed to configure the DAI. First, you must enable DAI:
AccessSW1(config)# ip arp inspection vlan 20AccessSW2(config)# ip arp inspection vlan 40AccessSW3(config)# ip arp inspection vlan 60AccessSW4(config)# ip arp inspection vlan 80Trusted Ports
Then assign trusted ports, which are ports through which ARP packets are not filtered by DAI. These are typically ports connected to other switches or routers that control traffic and are considered trusted sources of ARP packets
AccessSW1(config)# interface range g0/0, g0/1
AccessSW1(config-if)# ip arp inspection trustAccessSW2(config)# interface range g0/0, g0/1
AccessSW2(config-if)# ip arp inspection trustAccessSW3(config)# interface range g0/0, g0/1
AccessSW3(config-if)# ip arp inspection trustAccessSW4(config)# interface range g0/0, g0/1
AccessSW4(config-if)# ip arp inspection trustg0/0andg0/1are connections up to the distribution level switches
DAI Limit Rate
To protect the network from attacks that can overload ARP inspection, such as attempts to send ARP requests in bulk (for example, during an ARP Spoofing attack), you can configure Limit Rate on untrusted ports. This limits the number of ARP packets that the switch can process on each untrusted port.
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if-range)#ip arp inspection limit rate 15AccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if-range)#ip arp inspection limit rate 15AccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if-range)#ip arp inspection limit rate 15AccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if-range)#ip arp inspection limit rate 15In this example, the limit is set to 15 ARP packets per second for ports g0/2 and g0/3. This helps prevent switch congestion and blocks attackers trying to send many spoofed ARP requests.
ARP ACL
If necessary, you can create an ARP ACL to avoid checking devices with a static IP. In case there are hosts on your network with a static address:
Nihilism(config)# arp access-list DAI
Nihilism(config-arp-nacl)# permit ip host <IP> mac host <MAC>Dynamic ARP Inspection (DAI) is a powerful tool to protect your network from ARP Spoofing and Man-in-the-Middle attacks. Configuring DAI in conjunction with DHCP Snooping ensures that ARP packets are inspected based on valid DHCP table data. Proper separation of ports into trusted and untrusted ports, as well as configuring ARP request rate limiting, helps ensure a high degree of security for your network infrastructure.
Storm Control
Storm Control - is a switch security feature designed to prevent broadcast, multicast, and unicast storms in the network. Storms occur when certain types of traffic (such as broadcast packets) begin to dominate the network, which can lead to network congestion and denial of service (DoS). In a security context, Storm Control is particularly useful for blocking excessive amounts of noisy ARP/NetBIOS scans, which can be either legitimate network operations or part of an attacker's reconnaissance.
Possibilities Storm Control
- Limit Broadcast Traffic: Broadcast storms can result from ARP spoofing or unauthorized network scanning when an attacker sends a large number of ARP requests or NetBIOS packets in an attempt to obtain information about the network. Storm Control allows you to limit the number of such packets passing through a switch port, which prevents possible attacks and reduces the load on the network.
- Limit Multicast Traffic: Multicast packets, like broadcast packets, can be used for network reconnaissance. Storm Control allows you to limit the number of such packets, preventing them from negatively impacting network performance.
- Limit Unicast Traffic: In rare cases, attackers may generate a large number of unicast packets targeting a specific IP address or MAC address. Storm Control allows you to set limits on this type of traffic as well.
Storm Control provides network administrators with the ability to protect the network from various types of attacks and anomalous behavior, preventing situations in which the network could be overwhelmed or even paralyzed. This feature is especially useful in large corporate networks where the potential consequences of a network storm can be critical.
Principles of Storm Control
Storm Control works by setting thresholds for different types of traffic - broadcast, multicast, and unicast. When the amount of traffic on a port exceeds a specified threshold, the switch either blocks that traffic or disables the port to prevent further storm traffic from spreading.
Configuration Storm Control
Configuring Storm Control on the switch includes defining thresholds for different types of traffic: broadcast, multicast, and unicast. These thresholds are set as a percentage of the total port bandwidth and define the maximum amount of traffic that can pass through the port per unit of time. If the amount of traffic exceeds these thresholds, Storm Control automatically takes action by either blocking the excess traffic or resetting the port to prevent possible network storms and attacks.
Basic parameters of Storm Control settings
Broadcast traffic (Broadcast):
- Broadcast traffic is used to send data to all devices on the network. Broadcast traffic is used to send data to all devices on the network, but it can increase significantly in the event of an attack or network configuration error;
- The 30% threshold is set to control broadcast traffic. This is a high enough value to avoid accidental blocking of legitimate traffic, but also effectively prevents potential broadcast storm attacks:
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# storm-control broadcast level 30.00
AccessSW1(config-if)# storm-control action shutdownAccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# storm-control broadcast level 30.00
AccessSW2(config-if)# storm-control action shutdownAccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# storm-control broadcast level 30.00
AccessSW3(config-if)# storm-control action shutdownAccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# storm-control broadcast level 30.00
AccessSW4(config-if)# storm-control action shutdowng0/2andg0/3are connections to end stations
Multicast traffic (Multicast):
- Multicast traffic is used to send data to a specific group of devices. It is actively used in multimedia applications such as IPTV;
- Setting the threshold at 30% keeps these applications stable while protecting the network from anomalous behavior and attacks such as DoS based on multicast traffic:
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# storm-control multicast level 30.00
AccessSW1(config-if)# storm-control action shutdownAccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# storm-control multicast level 30.00
AccessSW2(config-if)# storm-control action shutdownAccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# storm-control multicast level 30.00
AccessSW3(config-if)# storm-control action shutdownAccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# storm-control multicast level 30.00
AccessSW4(config-if)# storm-control action shutdowng0/2andg0/3are connections to end stations
Unicast traffic (Unicast):
- Unicast traffic is traffic sent from one device to another. Under normal circumstances, its volume can be significant, especially during active data downloads.
- The 30% threshold provides a balance between normal user experience and protection against overload and abnormal behavior.
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# storm-control unicast level 30.00
AccessSW1(config-if)# storm-control action shutdownAccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# storm-control unicast level 30.00
AccessSW2(config-if)# storm-control action shutdownAccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# storm-control unicast level 30.00
AccessSW3(config-if)# storm-control action shutdownAccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# storm-control unicast level 30.00
AccessSW4(config-if)# storm-control action shutdowng0/2andg0/3are connections to end stations
Why a threshold value of 30% is chosen
A threshold of 30% of the port capacity is chosen for the following reasons:
- Overload Protection: A value of 30% is high enough not to interfere with normal network operations during peak loads when users are actively using network resources for downloads, broadcasts, or heavy applications. It prevents legitimate traffic from being inadvertently blocked, which could lead to user disruptions and degraded network performance;
- Protection Effectiveness: A threshold of 30% effectively prevents broadcast and multicast storms, which can be caused by both configuration errors and deliberate attacks. This level provides sufficient bandwidth for normal operation of network applications without overloading the network;
- Flexible and adaptable: The 30% threshold can be adapted depending on the specifics of the network and its load. This value is suitable for most corporate networks, but can be adjusted if necessary based on traffic analysis and actual operating conditions
Properly configuring Storm Control with thresholds of 30% of port bandwidth provides effective protection of the network from congestion caused by both normal operation and deliberate attacks. Selecting these values allows you to maintain a balance between security and performance, ensuring stable network operation even under heavy loads. A switch with Storm Control configured will become a reliable barrier to any network threats, ensuring the protection and stability of your corporate network.
Cisco Smart Install
Smart Install - is a feature developed by Cisco to simplify the deployment and management of network devices such as switches. It allows new devices that connect to the network to be automatically configured without the need for manual intervention. Smart Install was originally conceived as a tool for quick and easy deployment of network infrastructure, especially in large enterprise networks. However, despite its usefulness, this feature has attracted the attention of attackers, causing serious vulnerabilities.
Smart Install was designed to automatically download configurations and software updates to new switches that connect to the network. The main components of Smart Install are:
- Director: The main switch or router that manages the setup process for new devices;
- Client: New devices that connect to the network and automatically receive their configurations from the director
When a new switch (client) connects to the network, Director automatically downloads the configuration and required software to it, simplifying the deployment process and minimizing the need for manual intervention.
Danger
Vulnerability allows attackers to remotely offload configuration from a switch using the Smart Install protocol. With the SIET exploit, an attacker can easily offload the configuration of a Cisco switch by learning sensitive infrastructure information, learn about user configuration, view password hashes, and more.
For Cisco switch security, it is better to disable Smart Install, this is done very easily, simple one command:
AccessSW1(config)# no vstackAccessSW2(config)# no vstackAccessSW3(config)# no vstackAccessSW4(config)# no vstackBut if you really need SMI, then allow access to the TCP/4786 port only from trusted subnets using ACLs.
Discovery Protocols
Discovery Protocols, such as CDP and LLDP, play a key role in network infrastructure by facilitating device management, diagnostics, and integration. They allow network devices to automatically share information about themselves with neighboring devices. However, if not properly configured, these protocols can pose significant security risks.
What are CDP and LLDP?
- Cisco Discovery Protocol (CDP): This is a proprietary Cisco protocol that is used to exchange information between Cisco devices. CDP allows devices to learn information about neighboring devices, such as device ID, IP addresses, software versions, and other parameters.
- Link Layer Discovery Protocol (LLDP): This is a standard protocol used to discover neighboring devices in networks with equipment from different manufacturers. LLDP provides similar functionality but is cross-platform and supported by a wide range of network equipment.
Information Gathering
One of the main threats associated with CDP and LLDP is the ability to collect sensitive information (Information Gathering). These protocols run by default on all ports of network devices and transmit sensitive data that can be used by attackers to further attack the network. For example, the following data is transmitted through CDP and LLDP:
- Device model: An attacker can learn what hardware he is dealing with, which can help him prepare attacks specifically targeting vulnerabilities in that model;
- Operating system and firmware version: Software version information allows attackers to determine if a device has known vulnerabilities that can be exploited;
- IP addresses and active interfaces: Knowing the IP addresses and interface configurations, attackers can conduct further reconnaissance or launch attacks against specific nodes in the network.
CDP and LLDP transmit critical information that can be used to launch more targeted attacks against the network infrastructure. In the hands of an attacker, such data can significantly increase the likelihood of a successful attack because it provides a better understanding of the structure and state of the network.
Mitigation
If CDP or LLDP are not required for network operation, you should disable them on interfaces where they are not needed. This will reduce the risk of sensitive information leaking out. There are two tactics:
- Disabling protocols on unnecessary ports: If CDP or LLDP are not required for network operation, they should be disabled on interfaces where they are not needed. This will reduce the risk of confidential information leakage:
- Disabling CDP:
AccessSW1(config)# no cdp run
AccessSW2(config)# no cdp run
AccessSW3(config)# no cdp run
AccessSW4(config)# no cdp run- Disabling CDP on a specific interface:
AccessSW1(config)# interface g0/2
AccessSW1(config-if)# no cdp enable
AccessSW2(config)# interface g0/2
AccessSW2(config-if)# no cdp enable
AccessSW3(config)# interface g0/2
AccessSW3(config-if)# no cdp enable
AccessSW4(config)# interface g0/2
AccessSW4(config-if)# no cdp enable- Disabling LLDP:
AccessSW1(config)# no lldp run
AccessSW2(config)# no lldp run
AccessSW3(config)# no lldp run
AccessSW4(config)# no lldp run- Disabling LLDP on a specific interface:
AccessSW1(config)# interface g0/2
AccessSW1(config-if)# no lldp transmit
AccessSW1(config-if)# no lldp receive
AccessSW2(config)# interface g0/2
AccessSW2(config-if)# no lldp transmit
AccessSW2(config-if)# no lldp receive
AccessSW3(config)# interface g0/2
AccessSW3(config-if)# no lldp transmit
AccessSW3(config-if)# no lldp receive
AccessSW4(config)# interface g0/2
AccessSW4(config-if)# no lldp transmit
AccessSW4(config-if)# no lldp receive- Selective use of protocols: If it is not possible to completely disable protocols (for example, in the case of VoIP devices that rely on CDP/LLDP for configuration and quality of service management), you should limit their use to only necessary interfaces such as interconnects and IP phone ports.
Discovery Protocols such as CDP and LLDP play an important role in simplifying network management and automating processes. However, they can also carry risks associated with the leakage of sensitive information, especially if they operate by default on all ports. To protect your network, you must carefully monitor the use of these protocols, disable them on unnecessary interfaces, and consider the risks associated with their use in mission-critical systems such as VoIP.
DTP
Dynamic Trunking Protocol (DTP) - is a Cisco proprietary protocol used to automatically configure trunk connections between switches. A trunk connection allows traffic from multiple VLANs to be carried over a single physical interface. Despite the convenience that DTP provides, it can also be a source of serious vulnerabilities such as VLAN Hopping, especially if not properly configured. In my opinion, the presence of this protocol in the infrastructure is indicative of poor network design. It is up to the network administrator to determine where trunk links should be. With DTP, the network infrastructure becomes less unpredictable.
Modes
- Auto: A port enters trunk mode if its neighbor port is also configured for trunk.
- Desirable: A port is actively trying to establish a trunk connection with its neighbor port.
- Trunk: A port is forced into trunk mode and always transmits traffic of all VLANs.
- Access: The port is configured in access mode and transmits traffic of only one VLAN
Vulnerability
DTP can be a VLAN Hopping attack vector due to DTP Desirable frame injection. DTP Desirable frame injection is a technique in which an attacker sends specially formed DTP packets to a switch port that is running in `Auto' mode. If DTP on the switch port has not been disabled, the switch can go into trunk mode and the attacker can access the traffic of all VLANs passing through that port.
Mitigation
The most effective way to protect against DTP injection is to disable DTP on all ports that should not be trunk ports. This can be done by manually setting the ports to Access mode
AccessSW1(config)# interface range g0/2, g0/3
AccessSW1(config-if)# switchport mode access
AccessSW1(config-if)# switchport nonegotiate
AccessSW2(config)# interface range g0/2, g0/3
AccessSW2(config-if)# switchport mode access
AccessSW2(config-if)# switchport nonegotiate
AccessSW3(config)# interface range g0/2, g0/3
AccessSW3(config-if)# switchport mode access
AccessSW3(config-if)# switchport nonegotiate
AccessSW4(config)# interface range g0/2, g0/3
AccessSW4(config-if)# switchport mode access
AccessSW4(config-if)# switchport nonegotiate
g0/2andg0/3are connections to end stations
VTP
VLAN Trunking Protocol (VTP) - is a Cisco proprietary protocol designed to simplify the management of VLANs in a network. It allows centralized creation, deletion, and modification of VLANs on all switches that are in the same VTP domain. While VTP greatly simplifies network management, it can also pose serious security threats, especially if misconfigured or if vulnerabilities are exploited.
How does VTP work?
VTP allows network administrators to centrally manage VLANs on the network. When changes are made on one switch, they are automatically propagated to other switches in the same VTP domain. VTP uses revision numbers to determine which version of VLAN information is most current. It is important to realize that VTP operates in three modes:
- Server: A switch in this mode can create, modify, and delete VLANs. All changes are propagated to other switches in the domain;
- Client: A switch in this mode receives VLAN information from server switches and applies it, but cannot change the VLAN configuration itself;
- Transparent: The switch does not participate in VLAN management via VTP, but can pass VTP messages to other switches.
Revision numbers
VTP uses revision numbers to determine whether the VLAN configuration is up to date. Each time a change is made to the VLAN configuration on a switch in Server mode, the revision number is incremented. If a switch with a higher revision number joins the network, its configuration will overwrite the VLAN configuration on all switches in the same VTP domain, regardless of whether it is up to date or not.
Danger
Because of the nuance with revision numbers, we have serious security issues when using the VTP protocol:
- Danger when connecting older switches: If an older switch with a higher revision number but an outdated VLAN configuration joins the network, it may overwrite the current VLAN database on all switches in the domain, resulting in the loss of all current VLAN settings. Check the current VTP settings before connecting an older switch to the network:
Nihilism# show vtp status
To safely reset the VTP revision number, you can change the VTP domain name on the switch and then reset it back. This action will reset the revision number to zero:
Nihilism(config)# vtp domain TEMPORARY
Nihilism(config)# vtp domain <ORIGINAL_DOMAIN>
Nihilism(config)# end
Nihilism# write memory
- VTP packet injection: This usually happens if the attacker is on a trunk channel. VTP works only on trunk channels and cannot be reached from an access layer port. An attacker can send a VTP packet to the switch with a higher revision number and an empty VLAN database. The switch will take this as actual information and delete all existing VLANs, resulting in complete network inoperability, a kind of network paralysis.
To protect against this, simply use the transparent VTP mode, in this mode the Cisco switch does not participate in the VTP processes.
AccessSW1(config)# vtp mode transparent
AccessSW2(config)# vtp mode transparent
AccessSW3(config)# vtp mode transparent
AccessSW4(config)# vtp mode transparent
VLAN Trunking Protocol (VTP) greatly simplifies VLAN management, but can cause serious network failures if not configured properly. Vulnerabilities related to revision numbers are especially dangerous when older switches are connected or as a result of deliberate attacks. To protect your network, you should carefully monitor VTP usage, use secure modes of operation such as Transparent, and take measures to prevent unauthorized changes to VLAN configuration.
Poisoning Protection
In today's networks, Windows-based endpoints are often subject to spoofing attacks, especially within local network segments. These attacks can be very insidious, as they are designed to redirect traffic or capture user network credentials. One of the most popular utilities for performing such attacks is Responder. This is a utility used by pentesters to intercept and spoof requests for name resolvers such as LLMNR, NBT-NS, and MDNS. These attacks allow attackers to hijack network credentials and perform Man-in-the-Middle (MITM) attacks.
The problem of mitigation
While it is difficult to combat such attacks with network hardware alone, you can use Suricata's Intrusion Detection System (IDS) to detect such attacks on Windows machines. Suricata IDS provides the ability to detect attempted attacks through specially written signatures that track anomalous packets and suspicious network traffic.
IPv6 Takeover Detection
One of the vulnerabilities that can be exploited by attackers is an attack to prioritize the use of IPv6 on Windows networks. This attack vector is made possible by the popular mitm6 tool. This tool takes advantage of the preference of IPv6 over IPv4 on Windows networks and sends special DHCPv6 packets (DHCPv6 Advertise) to set its IPv6 address as a DNS server on target Windows machines. This allows an attacker to perform a MITM attack and subsequent Relay attacks.
In a network segment where only IPv4 usage is expected, detection of DHCPv6 Advertise packets can be a clear indicator of an attack. Below is the Suricata signature for detecting such packets:
alert udp any any -> any 546 (msg:"Suspicious DHCPv6 Advertise Packet Detected, Possible attack using mitm6"; content:"|02|"; depth:1; offset:0; reference:url,https://blog.exploit.org/caster-neurotransmitter/; sid:100000; rev:1;)
This signature is triggered when a DHCPv6 Advertise packet (message type 02) is detected on port 546, which is used by DHCPv6 clients.
LLMNR Poisoning Detection
To detect an LLMNR Poisoning based attack executed with Responder, you can use the following signature:
alert udp any 5355 -> any any (msg:"LLMNR Response Packet Detected, Possible LLMNR Poisoning"; flow:stateless; reference:url,https://blog.exploit.org/caster-neurotransmitter/; content:"|80 00 00 01 00 01|"; sid:1000003; rev:1;)
This signature is designed to detect LLMNR response packets that may indicate an attempted Responder attack.
NBT-NS Poisoning Protection
The following signature can be used to detect NBT-NS Poisoning:
alert udp any 137 -> any 137 (msg:"NBT-NS Response Packet Detected, Possible NBT-NS Poisoning"; flow:stateless; reference:url,https://blog.exploit.org/caster-neurotransmitter/; content:"|85 00 00 00 00 01|"; sid:1000004; rev:1;)
This signature helps detect NBT-NS packets that indicate a possible attack.
mDNS Poisoning Protection
mDNS is more complicated. You can't just turn it off, it's constantly being used by infrastructure. For example, printers, Apple appliances, Chromecast, etc. In networks where you cannot disable mDNS, you can use the following signature to detect MDNS Poisoning attacks:
alert udp any 5353 -> any 5353 (msg:"MDNS Response Packet Detected, Possible MDNS Poisoning"; flow:stateless; reference:url,https://blog.exploit.org/caster-neurotransmitter/; content:"|84 00 00 00 00 01|"; sid:1000005; rev:1;)
This signature allows you to track suspicious MDNS packets that may be part of an attack against the MDNS protocol.
Using intrusion detection systems such as Suricata IDS to protect against Poisoning attacks is a good way to improve the security of Windows networks. Properly written signatures allow for timely detection of compromise attempts, such as mitm6 and Responder, and alert the administrator to suspicious activity. This is especially important in environments where disabling vulnerable protocols such as LLMNR or MDNS is not possible due to their active use in the infrastructure.
Outro
Access layer security is an acute issue in network infrastructure to minimize the probability of unauthorized connections to the network, to conduct network attacks, etc. In today's network infrastructure, securing endpoint devices and preventing network layer attacks becomes a top priority. Utilizing powerful tools like Suricata IDS to detect and prevent attacks like Poisoning and mitm6 helps to protect critical systems from compromise. Also, network hardware with its network security mechanisms can effectively combat spoofing attacks, prevent Information Gathering, and more.
Nevertheless, security should not be limited to network technologies only. It is important to remember the importance of a comprehensive approach that includes regular software updates, careful configuration of network equipment and constant monitoring of network activity. Disabling vulnerable protocols where possible and enforcing strict security policies are key defenses that will help minimize the risk of exploitation of vulnerabilities and successful attacks.
Only a combination of advanced threat detection and prevention tools, sound network configuration management, and ongoing employee training will allow you to ensure a high level of security in your organization. Remember, the network is a living organism that is constantly changing and evolving, and securing it requires an equally dynamic and adaptive approach.
