Nihilistic: Automated Cisco IOS Security Analysis
The issue of Cisco equipment security is especially acute, as the equipment of this vendor is widely spread all over the world. In this article we will talk about automated auditing of Cisco IOS devices using my utility “Nihilist”

The issue of Cisco equipment security is especially acute, as the equipment of this vendor is widely spread all over the world. In this article we will talk about automated auditing of Cisco IOS devices using my utility “Nihilist”
Caster - Nihilistic
Genre: Defensive
Label: exploit.org
Release Date: 04 May 2025
Performed by: Caster
Written by: Magama Bazarov
Cover Man: Magama Bazarov (Sony ILCE-7M3, f/2.8, 1/200 sec)Intro
This article is about automated security auditing of Cisco IOS network devices using the Nihilist tool. The purpose of the tool is to identify and analyze configuration vulnerabilities without interfering with device operation or applying attacking techniques. Nihilist runs over SSH using the netmiko library and does not modify the hardware configuration, using read-only commands with read-only privilege level commands.
Disclaimer
Nihilist is intended solely for analyzing Cisco IOS device configurations to identify potential vulnerabilities and security bugs.
The tool is not intended and should not be used to:
- Conducting attacks or exploits;
- Disrupt network equipment;
- Modify or delete an existing configuration;
- Unauthorized access to devices;
The user is solely responsible for compliance with legal requirements, internal regulations and rules of use of the tool. The developer is not responsible for any consequences of improper or incorrect use of Nihilist.
Before running Nihilist, make sure that the account used to connect has read-only configuration permissions (read-only). This tool does not need an account that has permissions to change the configuration, write to NVRAM, etc.
Basic Concept
Nihilist is based on a simple architecture based on SSH connectivity and the use of regular expressions. Nihilist is written in Python and does not require additional software to be installed on Cisco devices.
What is Netmiko and why do I need it?
Nihilist uses the netmiko library, a popular Python framework for automating network devices. Netmiko allows you to establish SSH connections to Cisco equipment, as well as send commands to devices and receive responses in a convenient way. This library is chosen for its reliability, ease of use, and broad support for network devices, including Cisco IOS.
SSH Connection
An example of connecting Nihilist to a Cisco IOS device over SSH using Netmiko:
# Connect to the Cisco IOS
def connect_to_device(ip, username, password, port, device_type):
print(Fore.WHITE + f"[*] Running on Python {sys.version.split()[0]}" + Style.RESET_ALL)
device = {
"device_type": "cisco_ios",
"host": ip,
"username": username,
"password": password,
"port": port,
"timeout": 10,
}
try:
print(Fore.GREEN + f"[*] Connecting to {device_type} at {ip}:{port}..." + Style.RESET_ALL)
connection = ConnectHandler(**device)
print(Fore.WHITE + "[*] Connection successful!\n" + Style.RESET_ALL)
return connection
except NetmikoAuthenticationException:
print(Fore.RED + "[-] Authentication failed! Check your credentials." + Style.RESET_ALL)
exit(1)
except NetmikoTimeoutException:
print(Fore.RED + "[-] Connection timed out! Check device availability." + Style.RESET_ALL)
exit(1)
except Exception as e:
print(Fore.RED + f"[-] Connection failed: {e}" + Style.RESET_ALL)
exit(1)
Using read-only commands (show)
A special feature of Nihilist is that the tool applies only show type commands, which completely eliminates the risk of changing the configuration of the tested equipment. This is important because the tool is designed as a diagnostic tool to identify weaknesses and possible threats without tampering with the device configuration.
Function Breakdown
Let's take a detailed look at how the DHCP Snooping analysis feature of the Nihilist tool works so that you can understand exactly how the tool works. I think this is very important when you are introducing your tool to everyone and a deep understanding is key.
What is DHCP Snooping?
DHCP Snooping is a Cisco IOS security mechanism that prevents attacks associated with rogue DHCP servers. DHCP Snooping inspects DHCP traffic and restricts it based on predefined criteria. Without DHCP Snooping enabled, the network is susceptible to:
- DHCP Exhaustion;
- MITM.
Stages of the function
The checking_dhcp_snooping() function implements the following steps:
Rate LimitChecks if there is a rate limit on DHCP requests:
rate_limit = re.findall(r'ip dhcp snooping limit rate (\d+)', dhcp_snooping_config)
This is important to prevent DHCP Exhaustion
Write-delay for DHCP Snooping databaseInterval for writing changes to the database:
write_delay_match = re.search(r'ip dhcp snooping database write-delay (\d+)', dhcp_snooping_config)
If this parameter is missing, changes may not be recorded efficiently and data may be lost
DHCP Snooping Database ConfigurationChecks if the database is configured to store DHCP bindings:
snooping_database = re.search(r'ip dhcp snooping database\s+(flash:|ftp:|https:|rcp:|scp:|tftp:)/\S+', dhcp_snooping_config)
If not configured, all DHCP bindings will be lost after a reboot
Option 82 (DHCP Snooping Information Option)Enabled by default, may cause compatibility issues with DHCP servers:
option_82_disabled = "no ip dhcp snooping information option" in dhcp_snooping_config
It is recommended to disable Option 82 on most networks. However, it is worth considering on a case-by-case basis, as Option 82 is sometimes used by network engineers
Checking trusted portsPorts on which trusted DHCP traffic passes without restriction:
snooping_trust_ports = re.findall(r'ip dhcp snooping trust', dhcp_snooping_config)
If trusted ports are not available, DHCP traffic will be blocked, which will disrupt the network
Analyzing the VLAN configurationUsing a regular expression, checks which VLANs have DHCP Snooping enabled:
snooping_vlans = re.findall(r'ip dhcp snooping vlan (\S+)', dhcp_snooping_config)
If VLANs are not explicitly specified, a warning is generated
Checking if DHCP Snooping is enabled
if not dhcp_snooping_config:
print("[!] WARNING: DHCP Snooping is NOT enabled on this device!")
This is a critical warning if the mechanism is completely off.
Getting the current configurationThe command used is:
show running-config | section dhcp snooping
The result is output to the dhcp_snooping_config variable
If the result is blank, DHCP Snooping is not configured!
This is exactly how "Nihilist" performs Cisco IOS security analysis: obtaining configuration data and parsing it using regular expressions.
What does Nihilist check?
"Nihilist" performs a detailed configuration audit of Cisco devices, analyzing various security aspects. The entire audit is divided into multiple stages.
System & Operational Checks
These checks help you quickly understand the status of the device and its configuration at the most basic level:
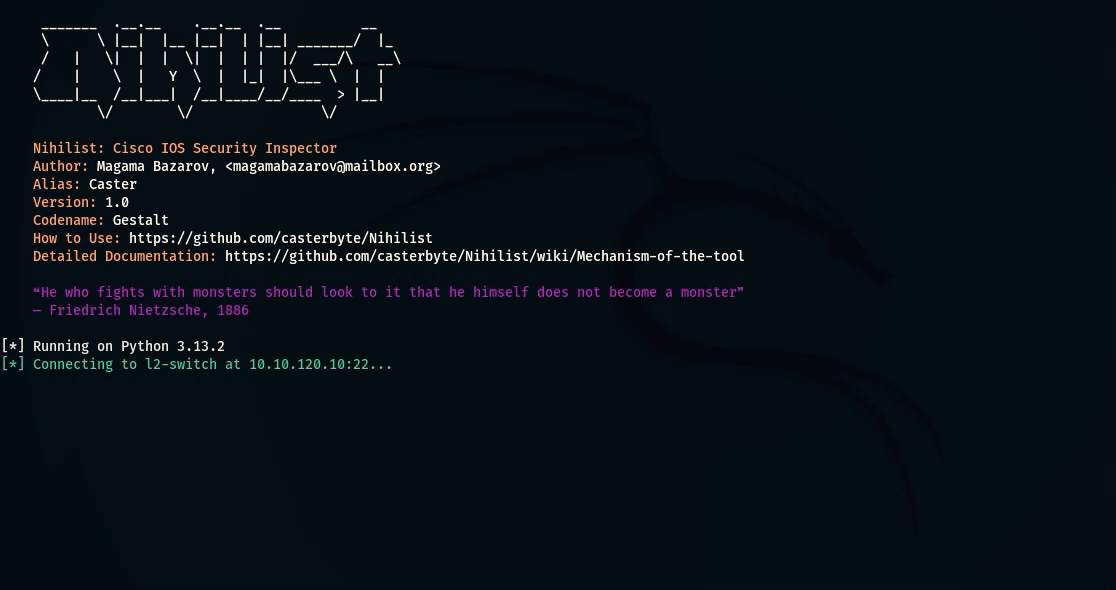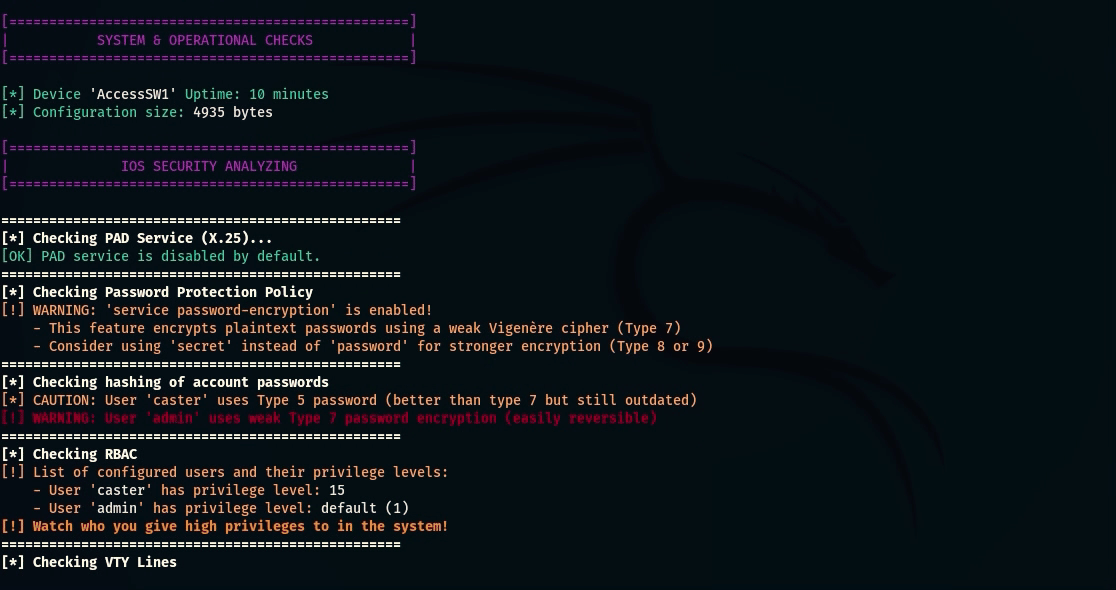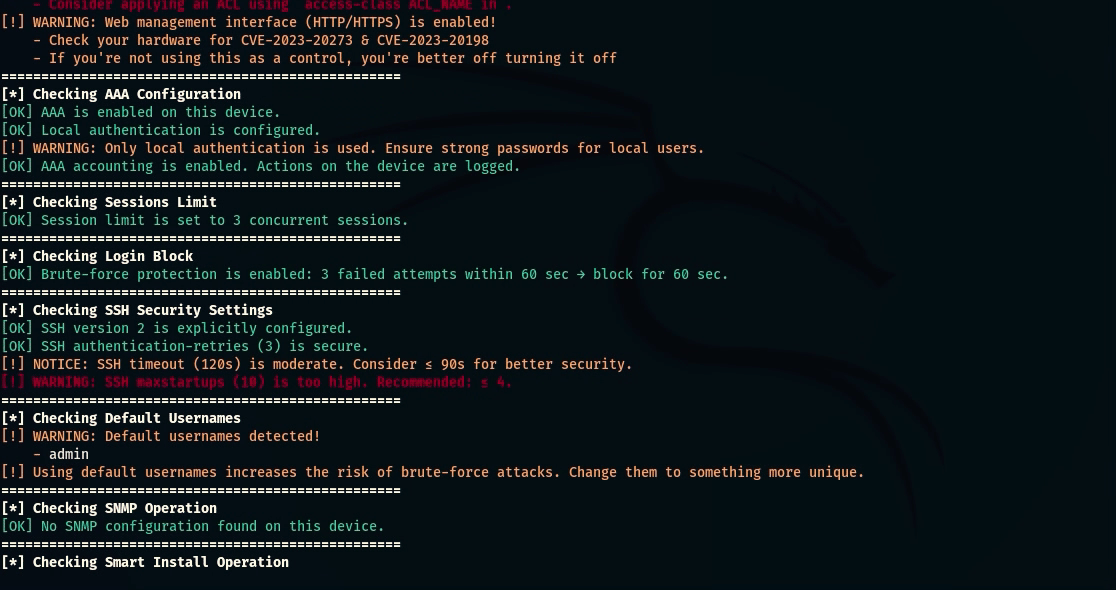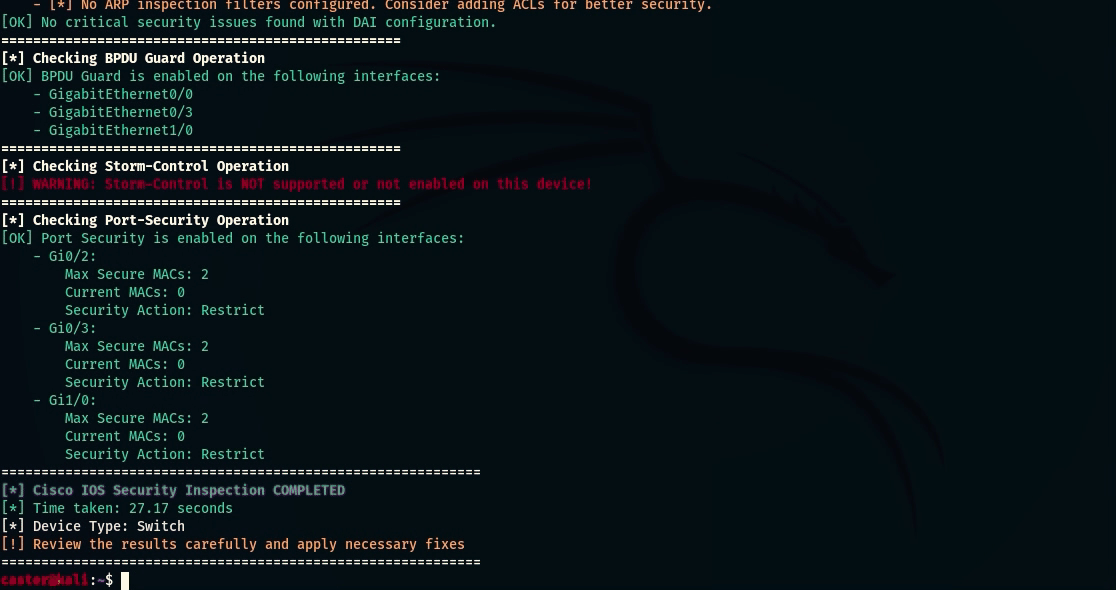
- Uptime Check: Checks how long the device has been running without rebooting. A value that is too high (years) may indicate that the device has not been updated and is vulnerable.
- Configuration Size Estimation: Analyzes the size of the current configuration. A configuration that is too large requires closer attention and may contain unwanted settings or outdated policies.
IOS Security Analyzing
This category includes checks for general device security settings, including access control, authentication, and cryptography.
- PAD Service Check: Checks if the Packet Assembler/Disassembler service is enabled, which can be used by an attacker to compromise the device;
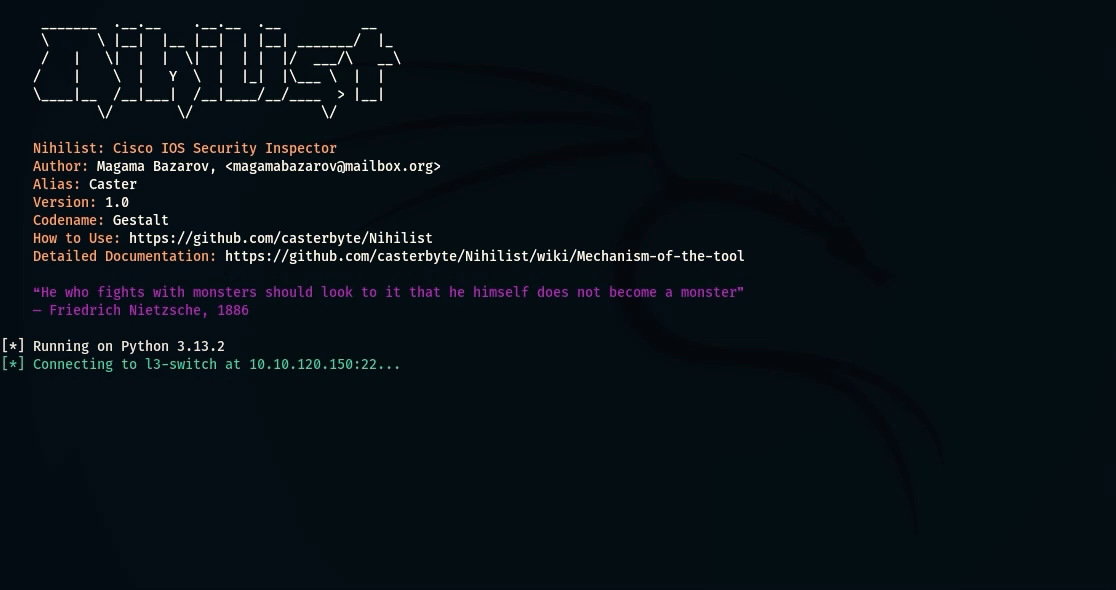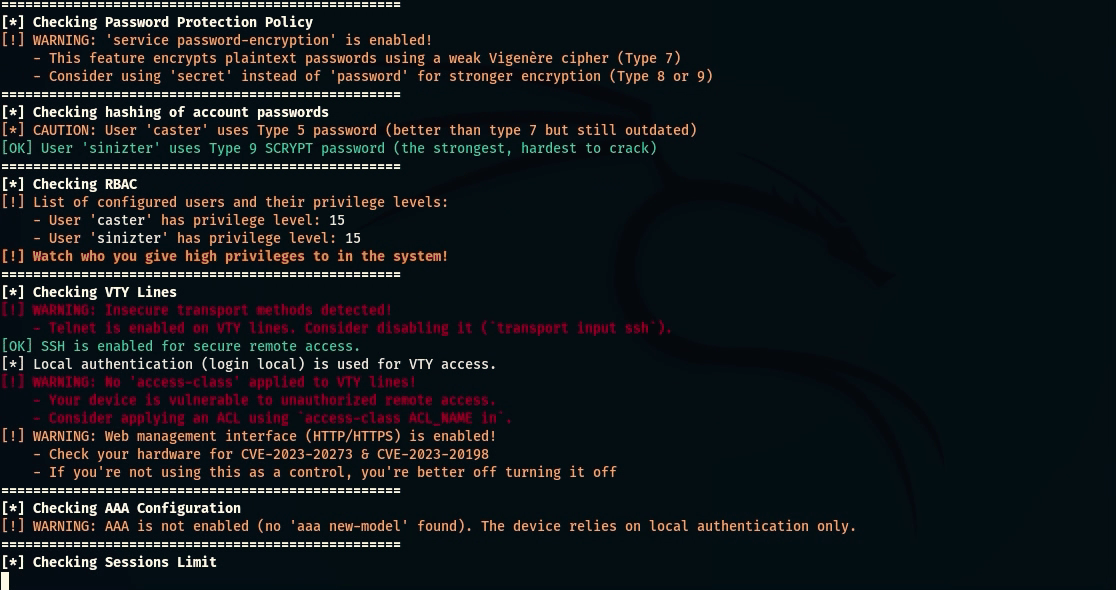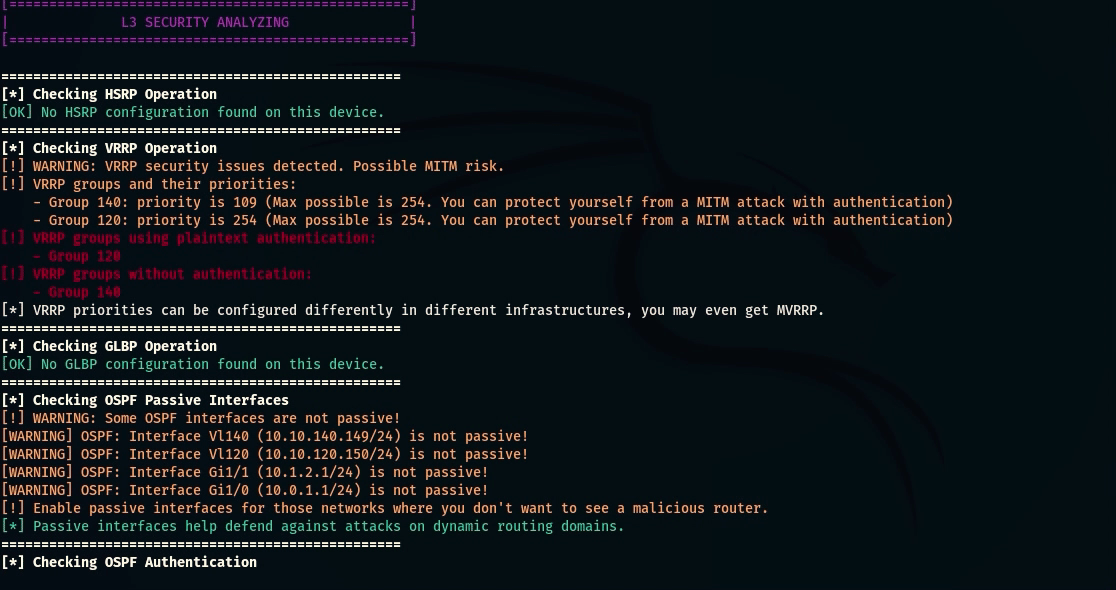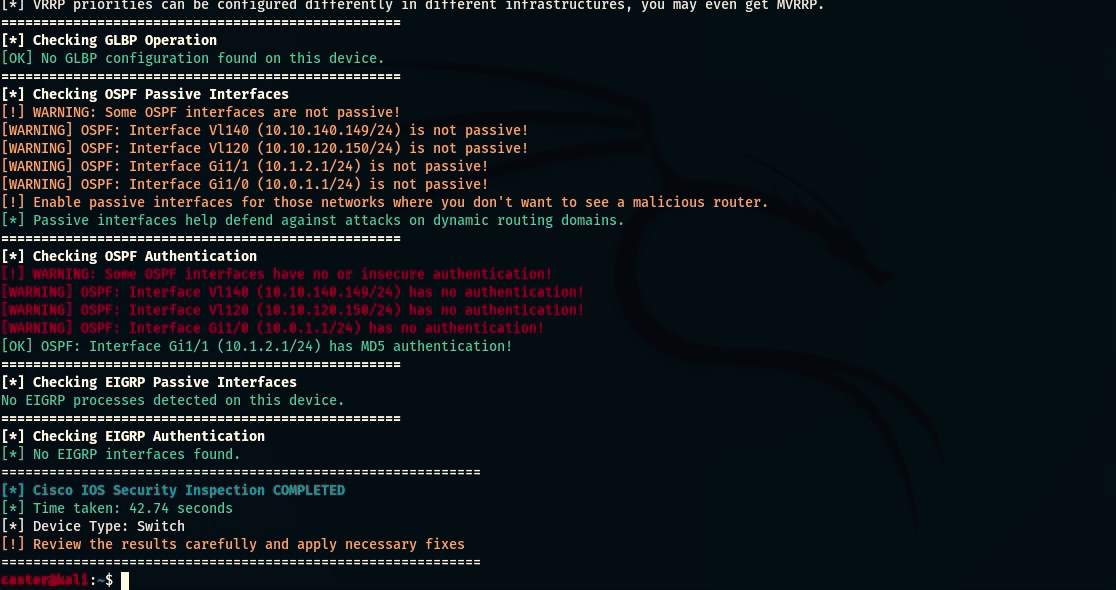
- Service Password Encryption Check: Checks if basic password encryption is present and used in the configuration;
- Password Hashing Check: Determines the type of password hashing used (types 4/5/7/8/9) and identifies weak algorithms;
- RBAC Check: Analyzes role-based access control settings and identifies potential minimum privilege violations;
- VTY Security Check: Checks the security of virtual terminals (Telnet, SSH), access-class restrictions and potential vulnerabilities;
- AAA Check: Analyzes the presence and correctness of centralized access control settings;
- Session Limit Check: Evaluates whether there is a limit on the number of concurrent user sessions;
- Login Block Protection Check: Checks for the presence of a login block-for protection mechanism to prevent brute force attacks;
- SSH Security Check: SSHv2 usage, timeout setting, and other key parameters;
- Default Usernames Check: Search for default or weak accounts (cisco, admin, root) that can be easily compromised;
- SNMP Security Check: Check SNMP community strings for weak values (public/private);
- Smart Install Check: Check for Smart Install service activity, which is often used by attackers to take over a device.
L2 Security Analyzing
Here, Nihilist identifies common Layer 2 security issues, including VLAN manipulation and attacks on link layer protocols.
- **VTP Status Check: Check the status of the VTP protocol, which can be used by attackers to modify the VLAN base;
- DTP Status Check: Checks if DTP is enabled on interfaces, which allows for a VLAN Hopping attack;
- Native VLAN Check: Analyzes Native VLAN usage to prevent double tagging attacks;
- DHCP Snooping Check: Check the state of protection against DHCP attacks (spoofing of DHCP servers);
- DAI Check: Check for protection against ARP Spoofing;
- BPDU Guard Check: Check protection against STP attacks (partial MITM, root roles hijacking);
- Storm Control Check: Analyzing protection against broadcast storms;
- Port Security Check: Check of MAC-address restrictions on ports (restriction of ports for unauthorized connection of devices)
L3 Security Analyzing
In this block, Nihilist inspects the security mechanisms of routing and redundancy protocols, identifying configuration errors and weak settings that can lead to network-level attacks.
- HSRP Check: Analyze HSRP configuration to identify risks of MITM attacks;
- VRRP Check: Analyze VRRP configuration to identify risks of MITM attacks;
- GLBP Check: Analyze GLBP configuration to identify risks of MITM attacks;
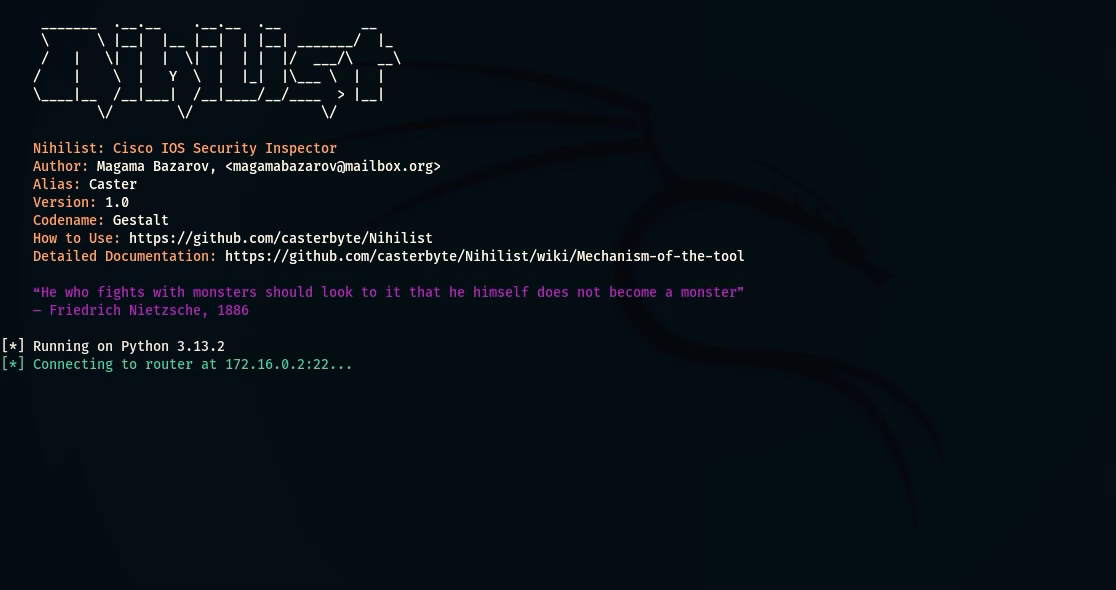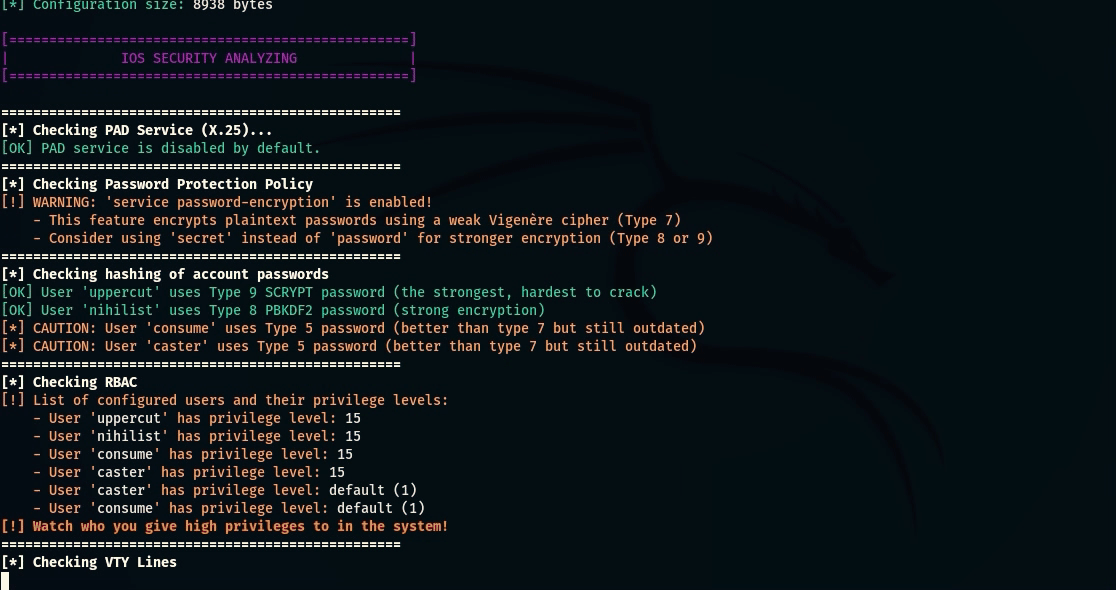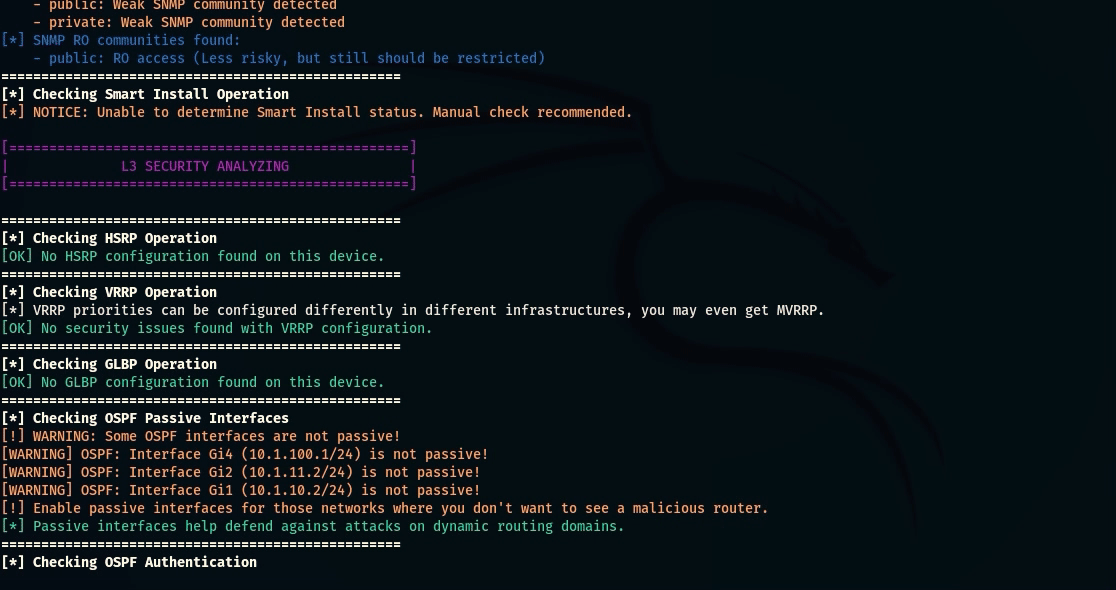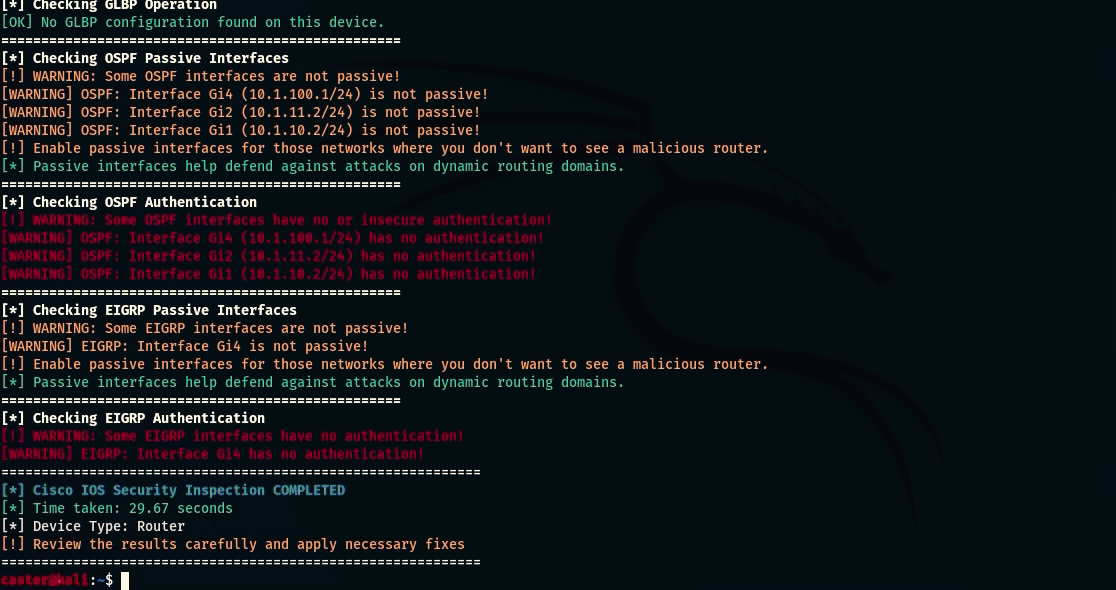
- OSPF Passive Interfaces Check: Checks OSPF interfaces for passive mode to prevent unauthorized routing;
- OSPF Authentication Check: Analyze OSPF authentication types (Null, MD5, SHA) to identify insufficient security;
- EIGRP Passive Interfaces Check: Checks EIGRP interfaces for passive mode to prevent unauthorized routing;
- EIGRP Authentication Check: Analyze the presence and reliability of authentication in EIGRP (Null, MD5, key-chains)
How to Use
To install the Nihilist:
:~$ sudo apt install git python3-colorama python3-netmiko
:~$ git clone https://github.com/casterbyte/Nihilist
:~$ cd Nihilist
:~/Nihilist$ sudo python3 setup.py install
:~$ nihilist --help
usage: nihilist.py [-h] --ip IP --username USERNAME --password PASSWORD [--port PORT] [--router] [--l2-switch] [--l3-switch]
options:
-h, --help show this help message and exit
--ip IP Specify the IP address of the device
--username USERNAME SSH Username
--password PASSWORD SSH Password
--port PORT SSH Port (default:22)
--router Specify if the device is a router
--l2-switch Specify if the device is a L2 switch
--l3-switch Specify if the device is a L3 switch
Trigger Arguments (CLI Options)
Nihilist supports as input parameters:
--ip: the user will need to specify the IP address of their device;--username: the username for SSH connection to the Cisco device;--password: the password for SSH connection to the Cisco device;--port: SSH port number, by default the tool uses port 22;--router: if the Cisco device is a router;--l2-switch: if it's a Cisco L2 switch;--l3-switch: if it's a Cisco L3 switch.
Important
- Be sure to specify only ONE of the parameters:
--router,--l2-switch, or--l3-switch, depending on the device type; - If you do not specify a device type, the audit will not be performed;
- Make sure the account has access to at least the
showcommands, as "Nihilist" is read-only and does not requireprivilege level 15
Practical Security Analysis of a Three-Layer Network
In the previous steps, I went over the functionality of Nihilist and its ability to identify vulnerabilities in the network infrastructure.
Now, to demonstrate how it works, we will perform a detailed security audit of a typical three-tier hierarchical network consisting of Core, Distribution, and Access layers.
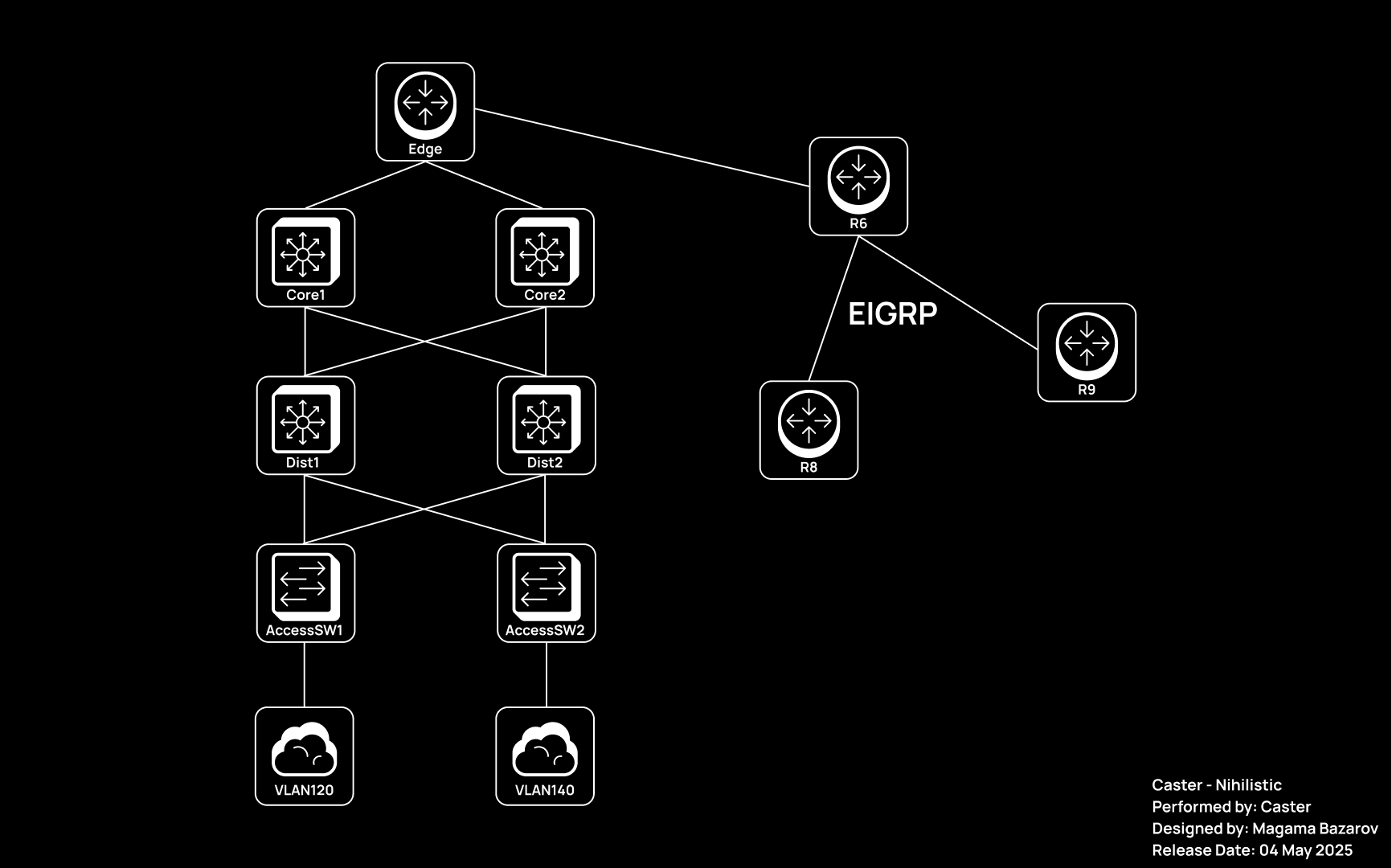
The scheme above shows the network topology that we will use as a test bed for our analysis. Our goal is to apply Nihilist to test devices at each layer, identify potential vulnerabilities, and offer recommendations for remediation.
Edge
caster@kali:~$ nihilist --ip 172.16.0.2 --username caster --password caster --router
L3 Switch
caster@kali:~$ nihilist --ip 10.10.120.150 --username caster --password caster --l3-switch
L2 Switch
caster@kali:~$ nihilist --ip 10.10.120.10 --username caster --password caster --l2-switch
Outro
Cisco equipment is very common all over the world and security is a major issue. Use it wisely and take care of the security of your infrastructure.
